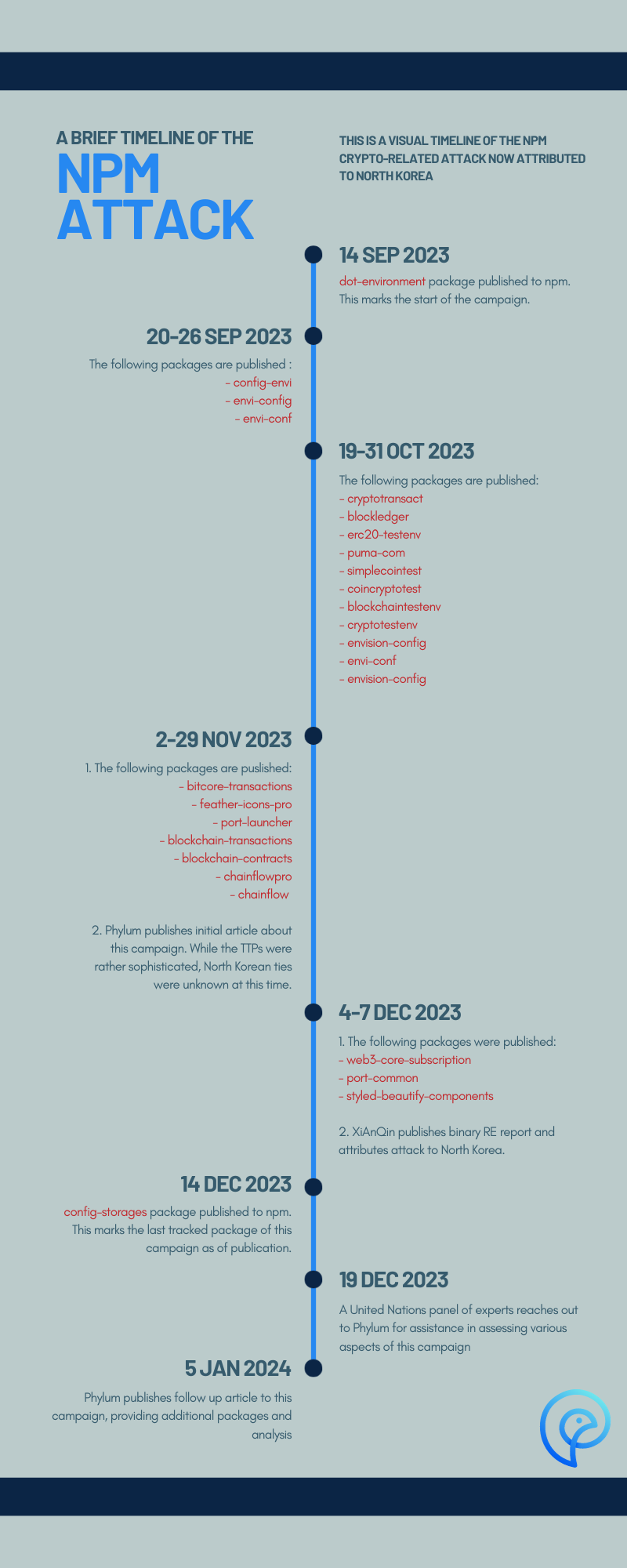
Update to November’s Crypto-Themed npm Attack

Back in November, we published a write-up about a collection of npm packages involved in a complex attack chain. These packages, once installed, would download a remote file, decrypt it, execute an exported function from it, and then meticulously cover their tracks by deleting and renaming files. This left the package directory in a seemingly benign state after installation.
Since that initial report, we have identified nearly two dozen additional packages belonging to this still active campaign. Additionally, the QiAnXin Threat Intelligence Center released a detailed analysis of the binary involved in this campaign, conclusively linking it to a North Korean APT. With this revelation, and given that the package names were crypto-themed, it becomes increasingly apparent that the campaign’s ultimate objective was likely twofold: first, to gain persistent access to the systems of developers who installed these packages, and second, to leverage this access to infiltrate the broader organization these developers belong to—likely entities within the cryptocurrency sector. Presumably the end goal, given the recent history of North Korean hacking objectives, was to steal substantial cryptocurrency assets, thereby circumventing the heavy sanctions imposed upon them—more on that later.
Updated Package List
As of the publication of this post, the following list represents what we have identified as packages belonging to this particular campaign. It includes packages released prior to what we identified in the original post, as well as packages published since that post.
| Package | Version | Publish Time |
|---|---|---|
| config-storages | 3.41.2 | 2023-12-14 07:05:00 |
| web3-core-subscription | 6.1.6 | 2023-12-07 20:07:47 |
| port-common | 1.0.0 | 2023-12-04 04:31:21 |
| styled-beautify-components | 6.1.6 | 2023-12-04 01:45:11 |
| bitcore-transactions | 1.2.1 | 2023-11-29 04:01:26 |
| feather-icons-pro | 4.29.1 | 2023-11-28 18:33:32 |
| port-launcher | 16.0.3 | 2023-11-13 00:23:26 |
| blockchain-transactions | 5.0.3 | 2023-11-07 06:13:27 |
| blockchain-contracts | 5.0.4 | 2023-11-07 05:04:13 |
| chainflowpro | 5.0.5 | 2023-11-07 04:52:17 |
| chainflow | 5.0.3 | 2023-11-02 11:40:14 |
| cryptotransact | 5.0.3 | 2023-10-31 09:18:57 |
| blockledger | 5.0.3 | 2023-10-31 09:03:03 |
| erc20-testenv | 5.0.3 | 2023-10-31 04:28:15 |
| puma-com | 5.0.3 | 2023-10-30 01:49:09 |
| simplecointest | 5.0.0 | 2023-10-26 03:13:40 |
| coincryptotest | 5.0.1 | 2023-10-26 03:03:05 |
| blockchaintestenv | 3.2.2 | 2023-10-25 05:16:39 |
| cryptotestenv | 3.2.1 | 2023-10-25 04:45:47 |
| envision-config | 0.1.3 | 2023-10-24 02:49:38 |
| envi-conf | 0.1.3 | 2023-10-24 02:47:10 |
| envision-config | 0.1.1 | 2023-10-19 03:38:24 |
| envi-conf | 0.1.0 | 2023-09-26 04:05:13 |
| envi-config | 0.1.1 | 2023-09-25 10:33:34 |
| config-envi | 0.0.1 | 2023-09-20 12:25:04 |
| dot-environment | 1.1.0 | 2023-09-14 09:22:43 |
For an in-depth analysis of the attack chain in this campaign, please see our original blog post. Looking at the packages as a whole, we can draw some interesting conclusions over the three months this campaign has been active. The packages demonstrate a consistent malicious strategy characterized by downloading and executing a remote file upon package installation. The URLs from which the binary is pulled vary, suggesting the use of multiple hosting points to evade tracking and detection. The file names and parameters used in the execution scripts also differ across packages, suggesting a deliberate effort to evade static detection systems. Furthermore, the cleanup methods—the deletion and renaming of files post-execution—also vary slightly, pointing again towards a careful effort to avoid leaving traces or creating patterns easily recognizable by security tools.
Attribution to North Korea
At the heart of this attack is the binary payload. On December 7, QiAnXin Threat Intelligence Center published a thorough write-up detailing their work on reverse engineering this binary. In their report, they state the following (please note the original report is in Chinese, so the following quote is a Chinese-to-English translation done by Google Translate):
QiAnXin Threat Intelligence Center recently discovered a batch of relatively complex downloader samples. These samples are loaded through multiple layers of nested PE files, and finally download the subsequent payload from the C2 server and execute it. One of the C2 server IP addresses was recently disclosed as being used in a software supply chain attack, in which attackers delivered malware by disguising themselves as encryption-related npm packages. Combining the content of the above report and the information of the downloader sample itself, it can be confirmed that these downloader malware are related to this npm package supply chain attack.
They go on to say
Based on the code characteristics of the downloader and other related samples, we related it to the historical attack samples of the Lazarus organization, and coupled with Lazarus's common supply chain attack methods, we believe that the attacker behind this npm package poisoning incident is likely to be Lazarus.
It’s worth noting that while the above evidence certainly does implicate North Korea generally, it’s possible that this could be a different North Korean-backed group apart from Lazarus that just happens to share some common infrastructure.
North Korean Crypto Hacks as a Means to Circumvent International Sanctions
As was the case in June’s npm attack by North Korean APT known as Lazarus, this campaign, too, appears to be heavily focused on crypto. From a global political perspective, this makes sense. North Korea has faced heavy international sanctions for decades, primarily due to its nuclear weapons program. These sanctions, led by the UN and supported by the US and other countries, aim to restrict North Korea’s access to foreign trade and financial systems. They target various sectors, including banking, commodities, and technology, with the objective of pressuring North Korea to dismantle its nuclear program.
In response to these sanctions and with very limited access to global financial systems, North Korea sought additional means to fund its weapons program and other state activities. Starting around the mid-2010s, coinciding with the rise of Bitcoin, other digital currencies, and DeFi platforms, they turned to crypto hacking as a successful and covert means to generate revenue. In fact, according to a 2023 report by Recorded Future, since 2017, North Korea has stolen an estimated $3 billion worth of cryptocurrency—$1.7 billion of which was stolen in 2022 alone; a sum that, astoundingly, is “equivalent to approximately 5% of North Korea’s economy or 45% of its military budget”. Based on this account, it’s quite clear that these hacking efforts are essential to the North Korean revenue stream and a necessary means to circumvent sanctions.
Shifting Targets
According to an analysis by Elliptic of recent Lazarus activity, “it has shifted its focus from decentralized services to centralized ones.” Elliptic cites increased security among DeFi platforms, brought about largely due to previously successful attacks from groups like Lazarus in this space and other inherent challenges in breaching decentralized services, as a driving factor for Lazarus’ shift back to targeting centralized services. They say
decentralized services often boast small workforces and – as the name suggests – are to varied extents decentralized. Hence, gaining malicious access to a developer may not necessarily equate to getting administrative access to a smart contract.
In contrast, centralized platforms, with their bigger workforces and centralized IT systems, present more lucrative and feasible targets for significant cyber theft. This strategic shift underlines the adaptability of the Lazarus Group in pursuing high-value targets in the crypto space.
The Lazarus Group’s recent shift back to favoring centralized services has proven quite effective, as evidenced by four major hacks in the summer of 2023. These include the $37.3 million heist from the crypto payment platform CoinsPaid, the $60 million theft from the crypto payment provider Alphapo, the $41 million heist from the online crypto casino stake.com, and the $54 million breach of the crypto exchange CoinEx.
The Open-Source Vector
Regardless of the target, a common attack methodology used by North Korean APTs is social engineering. Often, this involves some kind of deceptive tactic, such as a fake job interview with a person of interest, where the attacker will surreptitiously get the victim to install or run software that contains an attacker-written dependency hosted on an open-source ecosystem such as npm, PyPI, Maven, etc. In light of this, our team at Phylum has been approached by a United Nations panel of experts for additional insights on how North Korea uses, in this case, npm as a vector for these crypto-targeted attacks. Phylum ingests and analyzes tens of thousands of packages daily across a range of open source ecosystems, including npm. Given the amount of data we have and the tools we’ve created to operate on this amount of data, we are in a unique position to happily provide assistance to the UN in the form of opinions, additional analysis, code snippets, screenshots, recommendations, etc. related to this campaign.
Conclusion
Nation-state activities, particularly those of North Korean APTs, continue to plague open-source ecosystems. Leveraging social engineering, these actors find the world of open-source ecosystems an advantageous entry into organizations. Once inside, they establish persistence and subsequently pivot from a developer’s compromised machine to infiltrate the broader organization. Their ultimate aim is to exfiltrate significant amounts of cryptocurrency.
North Korea targets cryptocurrency because of its anonymous nature and purely digital existence, making it an effective tool to bypass the severe sanctions they face. Stealing cryptocurrency has become critical to North Korea’s state revenue stream. Their formula, infecting a single developer and then pivoting deeper into the organization, combined with social engineering, has proven alarmingly successful. This effectiveness is so pronounced that the United Nations has convened a panel of experts to investigate North Korea’s non-compliance with UN sanctions, and as part of that investigation, the UN has reached out to Phylum for assistance.
This ongoing activity by North Korea underscores the continued vulnerability of the open-source ecosystem, highlighting how threat actors can exploit the inherent trust developers place in these platforms for malicious activities.




