Phylum Adds Open Policy Agent (OPA) and Continuous Reporting
Customers now have more flexibility when creating and enforcing custom policies, and can show compliance with key software supply chain frameworks, regulations and guidelines.
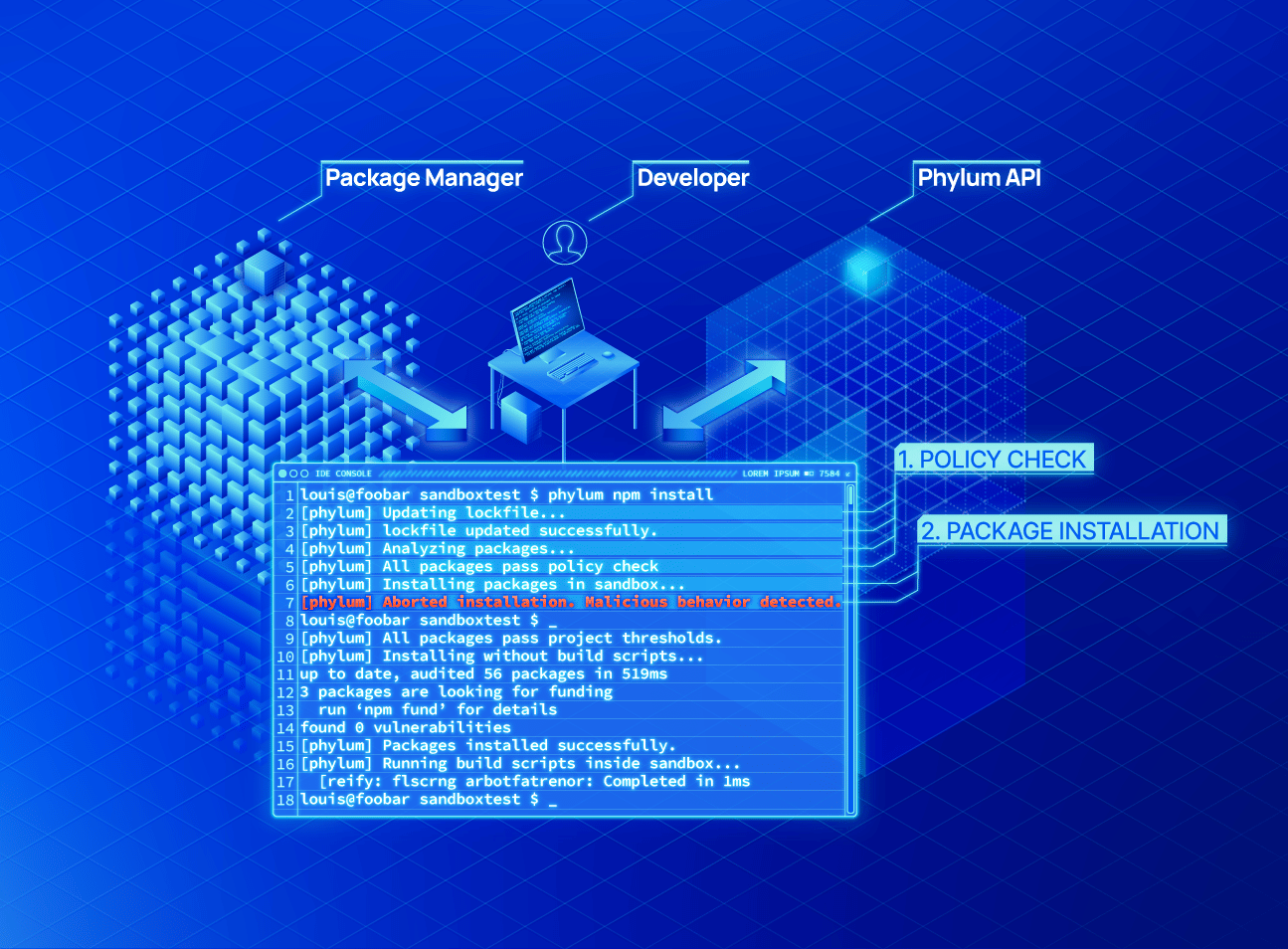
Phylum’s policy engine sits directly between the open-source ecosystem and the tools developers use to build source code, in line with the package selection process. It protects directly from an endpoint or plugs directly into a CI/CD pipelines so developers experience seamless, always-on protection and policy enforcement. Additionally, the Phylum Birdcage execution sandbox applies a zero-trust security model to the package installation process, providing defense-in-depth in the event that a software supply chain attack is perpetrated at runtime. This combination allows developers to work in their preferred environments and provides assurance for security teams that only secure and compliant code is being used.
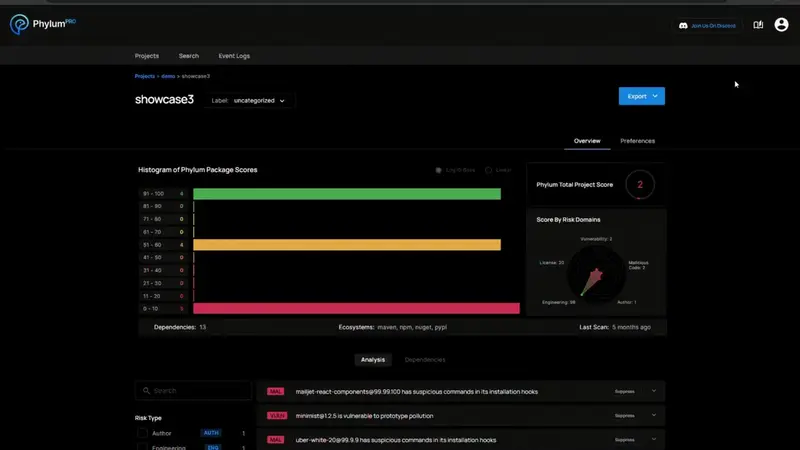
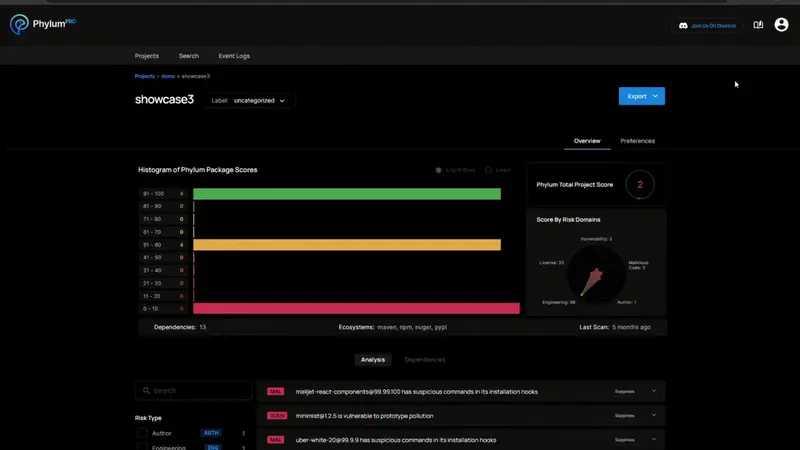
The Phylum platform comes equipped with a default policy that detects risks across five domains - software vulnerabilities, license misuse, OSS malware, author risk and reputation and engineering risk – and blocks attacks. The default policy also allows organizations to comply with software supply chain security regulations in NIST, ISO and more. Leveraging OPA, users with more specific requirements can easily write custom policies as needs evolve. Policy enforcement significantly limits risk and reduces remediation efforts, while continuous reporting allows organizations to keep more thorough records and document security posture on an ongoing basis.