Q3 2024 Evolution of Software Supply Chain Security Report

Executive Summary
As the software development landscape evolves, the security threats targeting open-source ecosystems are becoming more sophisticated and pervasive. In the latest quarter, Phylum's automated analysis platform processed millions of packages and files, uncovering many malicious behaviors compromising software supply chains. The risks have never been more significant, from spam floods overwhelming repositories to nation-state-backed campaigns targeting specific industries. This report delves into the key findings, including innovative new attack vectors, such as malicious code hidden in image files and trojanized versions of widely-used libraries like jQuery. By examining these trends and the tactics employed by threat actors, software developers, and organizations can better understand the evolving threat landscape and take action to protect their software environments.
Through detailed case studies and statistical insights, Phylum highlights the ongoing battle against cyber threats, focusing on attacks driven by financial incentives, sophisticated social engineering, and nation-state actors seeking to bypass sanctions through cybercrime. The analysis emphasizes the critical importance of rigorous security practices, automated detection tools, and continual vigilance in managing open-source dependencies.
Overview
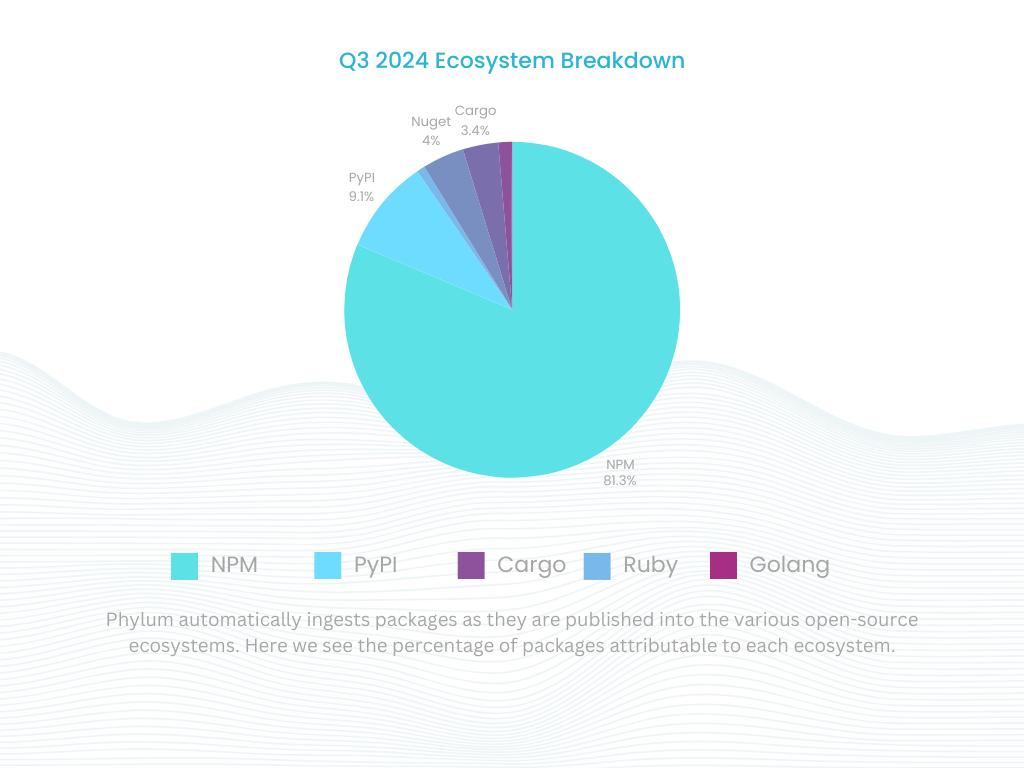
During this quarter, Phylum's automated software supply chain analysis platform processed 341.4 million files across 3.8 million packages, representing the continuously growing scale of threats. This extensive analysis revealed an alarming uptick in the volume and sophistication of attacks targeting software ecosystems, with particular emphasis on packages targeting specific organizations, leveraging obfuscated code, and engaging in social engineering.
Major Themes:
Two dominant trends emerged: the rise in the number of spam packages flooding ecosystems such as npm and PyPI and increasingly targeted attacks driven by financial, criminal, and nation-state actors. These campaigns underline the persistent threat posed by poorly vetted open-source packages, especially in critical industries like cryptocurrency and finance.
Key Findings
Phylum's analysis also revealed several concerning trends within the packages analyzed:
- 2,499 packages were specifically designed to target groups or organizations, often linked to cyber espionage or financial theft.
- 13,494 packages contained URLs known to be malicious, underscoring the growing risk of dependency injection attacks.
- 192,998 packages included pre-compiled binaries, creating potential attack vectors for binary tampering.
- 32,798 packages executed suspicious code during installation, a 23% increase compared to the last quarter.
- 9,260 packages made server requests to IP addresses, attempting to communicate with command-and-control servers.
- 20,254 packages attempted to obfuscate their underlying code, making detecting malicious activity much more difficult.
- 1,056 packages were identified as typosquats, indicating a concerted effort by attackers to trick developers into installing malicious versions of popular packages.
- A massive 173,195 spam packages were published across ecosystems, severely degrading the integrity of open-source repositories and threatening the trust developers place in these platforms.
- 20,343 packages were flagged as containing critical malware, requiring immediate attention.
Broader Trends and Insights
Obfuscation on the Rise:
A significant trend this quarter was the dramatic rise in obfuscation techniques. With 20,254 packages using obfuscation methods to hide malicious intent, attackers are making it harder for automated systems and security professionals to identify threats. This increase aligns with the observed attacks on prominent targets such as Ledger in Q4 2023, where attackers employed complex obfuscation techniques to hide malware intended to exfiltrate sensitive financial data.
Targeting Software Developers and Organizations:
Phylum identified 2,499 packages specifically crafted to target developers and organizations, often leveraging sophisticated social engineering techniques. These targeted attacks have increasingly focused on key industries such as finance and cryptocurrency, posing a major risk to companies relying on open-source dependencies.
Noteworthy Attacks or Campaigns
Garbage Patch: The NPM Spam Epidemic
This quarter, the rise of 173,195 spam packages across ecosystems like npm became a significant threat, turning open-source package repositories into a chaotic environment. This surge is primarily driven by the emergence of financial incentive models, such as cryptocurrency-based reward systems that compensate developers for publishing open-source code. Unfortunately, these incentives have led opportunists to publish hundreds of thousands of low-quality, non-functional packages. This phenomenon, detailed in The Great NPM Garbage Patch, presents a substantial challenge for developers attempting to sift through the growing volume of junk in search of legitimate software packages.
This flood of spam packages creates significant security risks. Attackers can disguise malicious payloads within these junk packages, potentially distributing malware across the ecosystem. Even though many of these spam packages are benign, the sheer volume makes it difficult for automated systems to separate legitimate code from potentially harmful files. The impact of this garbage wave is twofold: it degrades the overall trust in package registries, and it provides cover for more dangerous attacks, as the sheer volume of publications can overwhelm security mechanisms.
North Korean APTs Targeting Developers
Phylum continues to track the malicious attacks of North Korean Advanced Persistent Threat (APT) groups targeting developers through npm. These campaigns have evolved significantly throughout multiple campaigns, relying on sophisticated social engineering tactics to compromise their targets. For example, one common technique involves releasing malicious npm packages that impersonate useful developer tools or are disguised as part of job application processes. As detailed in North Korea Still Attacking Developers via NPM, attackers use these packages to steal cryptocurrency, login credentials, and other sensitive information from compromised machines.
The scale and persistence of these attacks point to North Korea’s strategic interest in leveraging open-source ecosystems to bypass economic sanctions through cybercrime. These campaigns are often highly targeted, focusing on cryptocurrency developers and fintech companies. Moreover, the attackers have developed advanced evasion techniques, using obfuscated code and rapidly pulling down packages after they've been published to limit detection. Phylum’s research has been crucial in identifying and mitigating these threats, showcasing the evolving and highly sophisticated nature of state-sponsored cyberattacks.
Trojanized jQuery in Persistent NPM Campaign
One of the more alarming developments this quarter was the discovery of a persistent campaign shipping a trojanized version of the popular jQuery library via npm. The attackers significantly increased their potential reach by targeting such a widely used library, making this attack particularly dangerous. As Phylum’s investigation revealed, the malware hidden in these modified jQuery packages exfiltrates sensitive data from developer environments, potentially compromising individual developers and entire organizations. The details of this attack are covered in Persistent NPM Campaign Shipping Trojanized jQuery, which highlights how attackers are capitalizing on developers’ trust in popular libraries.
This incident demonstrates the dangers of relying on commonly used libraries without rigorous vetting. Developers often trust that well-known packages like jQuery are safe, but attackers who insert malicious code into popular libraries can exploit this trust. The trojanized jQuery packages were part of a more extensive campaign to infiltrate corporate environments, intending to steal sensitive information such as access credentials. Phylum's automated detection tools were instrumental in uncovering this campaign, emphasizing the critical need for ongoing vigilance in open-source ecosystems.
Fake AWS Packages Delivering C2 Malware via JPEGs
Phylum discovered fake AWS packages distributing command-and-control (C2) malware hidden within JPEG files in an innovative new attack. This method represents a sophisticated evolution in malware delivery tactics, as image files are often overlooked during routine security scans. As outlined in Fake AWS Packages Ship Command-and-Control Malware in JPEG Files, the attackers embedded malicious code in the JPEGs, which would execute when the package was installed. This allowed the attackers to establish a C2 channel, allowing them to control the compromised system remotely.
Using image files to deliver malware adds a new layer of complexity to software supply chain attacks. Traditional security tools might miss this threat because the malicious payload is embedded in a seemingly harmless file. By leveraging fake AWS packages, attackers could also exploit the trust developers place in cloud services like AWS. This campaign underscores the need for more advanced security mechanisms that can detect and prevent such novel attack vectors and the importance of educating developers on the risks posed by third-party packages.
New Tactics from Familiar Threat Actors
Phylum also uncovered new techniques from familiar threat actors this quarter, further illustrating the evolving nature of supply chain attacks. In New Tactics from a Familiar Threat, a well-known group that had previously targeted npm shifted its focus to new obfuscation and remote file execution methods. These attackers have shown remarkable adaptability, constantly refining their techniques to avoid detection by automated security tools. This ability to innovate quickly makes them a persistent threat to open-source ecosystems.
One of the key techniques used in this latest campaign involved obfuscating the package's true intent by embedding the final payload in remote files that were only downloaded after installation. This approach minimizes the chances of detection during the initial review of the package, as no malicious code is present in the package itself at the time of publication. Instead, the attackers delay the malware delivery until the package is installed in a vulnerable environment, ensuring the payload is executed under the radar. Phylum’s work in detecting and exposing these campaigns highlights the importance of robust security measures in protecting the software supply chain from evolving threats.
Conclusion
The persistent rise of sophisticated malware attacks within the open-source ecosystem reflects a broader trend of increasing risk to the software supply chain. Phylum anticipates further sophistication in attack techniques driven by state-sponsored actors and opportunistic criminals. As open-source usage expands, vigilance, automation, and governance will be the key defenses against future threats.
Phylum Q3 Research Recap
We routinely publish research on campaigns and targeted software supply chain attacks. While these do not cover all the campaigns we see, they highlight some of this quarter's more interesting attacks and behaviors.
https://blog.phylum.io/fake-aws-packages-ship-command-and-control-malware-in-jpeg-files/
https://blog.phylum.io/new-tactics-from-a-familiar-threat/
https://blog.phylum.io/persistent-npm-campaign-shipping-trojanized-jquery/
https://blog.phylum.io/north-korea-still-attacking-developers-via-npm/
https://blog.phylum.io/the-great-npm-garbage-patch/
About Phylum
Phylum defends applications at the perimeter of the open-source ecosystem and the tools used to build software. Its automated analysis engine scans third-party code as soon as it’s published into the open-source ecosystem to vet software packages, identify risks, inform users, and block attacks. Phylum’s open-source software supply chain risk database is the most comprehensive and scalable offering available. Depending on an organization’s infrastructure and appsec program maturity, Phylum can be deployed throughout the development lifecycle, including in front of artifact repositories, in CI/CD pipelines, or integrated directly with package managers. Phylum also offers a threat feed of real-time software supply chain attacks. The company is built by a team of career security researchers and developers with decades of experience in the U.S. Intelligence Community and commercial sectors. Phylum won the Black Hat 2022 Innovation Spotlight Competition, was named to Inc. Magazine’s 2023 Best Workplaces, and became a Top Infosec Innovator by Cyber Defense Magazine. Learn more at https://phylum.io, subscribe to the Phylum Research Blog, and follow us on LinkedIn, X and YouTube.