Q4 2023 Evolution of Software Supply Chain Security Report

Phylum is the front-runner in software supply chain attack identification and protection. Across the current digital landscape - where open source is used in 97% of projects and comprises more than 70% of code bases - keeping tabs on threats and risks originating from the use of open source is absolutely critical. By automatically and continuously monitoring the publication of open source packages across seven diverse ecosystems (i.e., npm, PyPI, RubyGems, Nuget, Crates.io, Golang, and Maven), Phylum can provide a deep insight into the risks associated with using open source libraries and packages.
During the last quarter of 2024, Phylum witnessed a continued increase in attacker sophistication and a startling increase in the number of organizations being directly targeted by threat actors. Nation-state-backed actors continued to publish malware to the likes of npm and PyPI, drawing the attention of the United Nations as North Korea leveraged supply chain attacks to fund its missile program.
Phylum has been diligently tracking each of these attacks, alerting the public to the most interesting or pressing threats throughout the year.
Overview
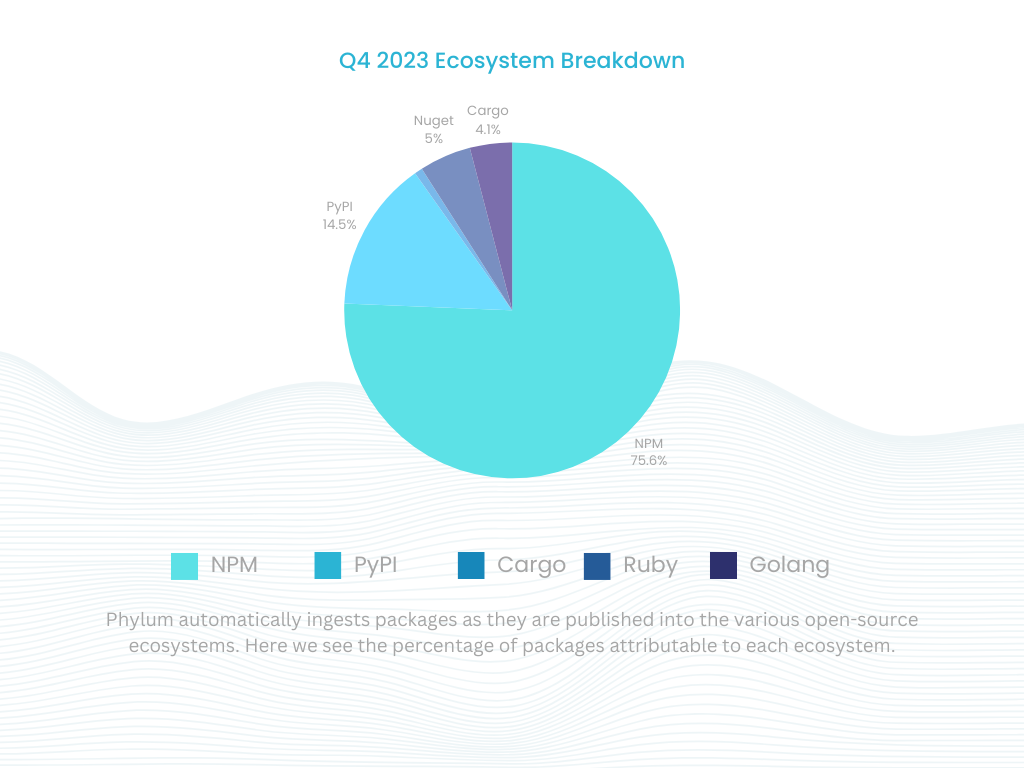
As was the case in Q3 2023, we saw a continued increase in actor sophistication in the fourth quarter. This quarter, Phylum analyzed 183M files across 2.5M packages. This represents a decrease of approximately 9.85% in analyzed files and approximately 16.67% in package publications from the previous quarter. The breakdown of packages published across each individual ecosystem is captured below:
Across all packages analyzed this quarter, Phylum saw the following behaviors:
- 3,532 packages targeted specific groups or organizations
- 9,324 packages referenced known malicious URLs
- 299,415 packages contained pre-compiled binaries
- 28,120 packages executed suspicious code during installation
- 6,907 packages made requests to servers by IP address
- 6,972 packages attempted to obfuscate underlying code
- 99 packages enumerated system environment variables
- 52 packages imported dependencies in a non-standard way
- 6,032 packages surreptitiously downloaded and executed code from a remote source
- 2,825 typosquat packages were identified
- 3,650 packages were registered by authors with throwaway email accounts
- 363,158 spam packages were published across ecosystems
- 603 depends on known malware
- 1,678 packages reviewed and deemed critical malware
The number of packages published decreased slightly when compared to the previous quarter. However, the number of organizations targeted is substantially higher. A larger proportion of packages published attempted to gain execution in specific organizations (e.g., dependency confusion). Incredibly, we saw a 262.63% increase in targeted attacks compared to Q3 2023, which was already up 47% from Q2 2023! This represents a general trend across 2023 of an increase in direct, targeted attacks.
Attackers also continued to make use of code obfuscation to mask the underlying intent of their malware. In Q4, we saw a 26.7% increase in actors obfuscating their malicious packages. Importantly, obfuscation made an appearance in one of the more noteworthy campaigns of Q4, namely, the supply chain attack on Ledger. Thus, an increase in code obfuscation in open source packages and software libraries may serve as a harbinger of continued attacks against software developers.
North Korea Funds Its Missle Program With Malicious npm Packages
Phylum was the first company to identify nation-state activity targeting open source package registries. In June 2023, we reported on a series of oddly sophisticated package publications, which was shortly thereafter included in a security advisory from Github. Throughout the course of 2023, we continued to track the activities of the Lazarus group across several additional campaigns, with a new (but very similar) campaign emerging in Nov 2023, again publishing packages to npm as part of a social engineering campaign.
In 2023, $3.8B of digital assets were stolen by attackers. According to Chainalysis, nearly 45% of this pilfered cryptocurrency was stolen by North Korean-backed operatives to sidestep imposed sanctions and further their weapons and nuclear programs.
The attacks in question utilized a sophisticated, multi-stage approach involving downloading and manipulating remote files, executing scripts on developer workstations, and performing a meticulous cleanup process, leaving the system clean, should anyone decide to investigate. This stealthy and complex strategy highlights the evolving threats in open-source ecosystems, with attackers performing behaviors we’d see in traditional cyberattacks focusing on gaining a foothold in a network, maintaining persistence, and minimizing the attacker's footprint.
The success of these campaigns has unsurprisingly drawn the attention of various government bodies and resulted in a direct query from the United Nations to Phylum requesting additional information on these campaigns as well as guidance and recommendations for member states and private sector companies.
Phylum expects these attacks to continue into 2024. As campaigns continue to be identified, we predict a continued increase in the sophistication of the attack chains deployed by nation-state-backed actors.
Red Teams Emulate Supply Chain Attackers
In Dec 2023, Phylum published an article outlining the discovery of an additional set of oddly sophisticated packages. Unlike some of the other campaigns, this one was highly targeted.
These packages contained an encrypted component that could only be unlocked with data from the environment of a local machine in a specific network, where the decryption key was the hostname of a specific organization. Once decrypted, the payload was executed, and user credentials were moved laterally inside the network to a Microsoft Teams Webhook. This meant one of two things: a threat actor had gained a deep foothold in the network, or this was the work of an internal employee, perhaps as part of a larger security audit.
Realizing these packages' specific focus, we contacted the targeted organization. If this was an external threat actor, it was vital that they were made aware of it before the attacker could do significant damage.
As we waited for a response, and without clear insight into the motivations behind these packages, we continued our analysis of what appeared to be a very advanced and sophisticated attack comparable with other APT (Advanced Persistent Threat) campaigns we have encountered before.
Phylum was able to make contact with the targeted company in question. And in doing so, we were able to determine that this was part of a broad internal security assessment aimed at mimicking pressing real-world threats. The attack looked to copy the behaviors the organization was seeing from attackers leveraging the software supply chain as a conduit into their network.
As sophisticated security organizations realize the real and present danger of software supply chain attacks, one must ask themselves, “Is my organization properly equipped to deal with an attack of this sort?”
Cloud Providers Targeted
Two common themes have generally emerged as motivations for software supply chain attacks: stealing credentials to production systems and stealing financial resources (e.g., bank account information, cryptocurrency, etc.). This held true in the attack we uncovered in Oct 2023.
The threat actor targeted a select group of widely used cloud provider SDKs in this attack. A review of the code indicated that the attacker was specifically interested in sensitive credentials to cloud infrastructure.
Capitalizing on the trust developers place in these packages, the attacker subtly altered a key part of the code responsible for managing and handling credentials. This modification introduced a stealthy HTTP POST request for the users’ access and secret keys to a remote URL under the attacker’s control. By making only minor changes and republishing these altered packages on PyPI with similar names, the attacker aimed to blend in, making detection difficult while maintaining the packages’ expected functionality.
This method, employed in at least five packages, involved a basic yet effective technique to obscure the remote URL, demonstrating a calculated approach to infiltrating trusted software components on developer workstations and production infrastructure.
NuGet Hit With Software Supply Chain Attack
In Q3 2023, Phylum identified a nascent typosquatting campaign targeting the Rust ecosystem. In Q4, we followed up on this by identifying a campaign targeting the C# ecosystem, Nuget.
In Oct 2023, our automated system began alerting us to a series of package publications that were being released laced with the SeroXen RAT. The malware packages in question targeted legitimate packages via the common typosquat attack vector.
SeroXen, a new Remote Access Trojan (RAT), is falsely advertised as a legitimate tool and sold as a user-friendly package on a dedicated website, making it easily deployable without extensive technical skills. AT&T Cybersecurity's May 2023 post offers an insightful analysis of SeroXen, highlighting its evasion tactics, such as its fileless nature and techniques to avoid virtualization and sandbox detection. SeroXen's use of encrypted payloads and anti-debugging methods makes it a significant threat.
Interestingly, the attacker behind this campaign went out of their way to spoof the metadata served on Nuget, arbitrarily inflating download counts to that of the legitimate packages it was mimicking. As developers often use GitHub stars or downloads as a proxy for determining if a package is good or used broadly, outright lying about downloads is an effective strategy for getting individuals to install and use your package.
The presence and care the attacker took to spoof package metadata in Nuget further emphasizes the vulnerabilities and risks posed by using packages from open source registries.
Ledger Hardware Wallets Compromised
Ledger is known for its broad offering of hardware wallets in the cryptocurrency space. The storage of financially valuable assets on end-user devices makes it a juicy target for would-be supply chain attackers, which we watched unfold during Q4 of 2023.
The security breach occurred as a result of a spear phishing attack targeting a former employee of Ledger. The attack aimed to extract the company’s npm publishing credentials, which surprisingly (and to the shock of security professionals) the ex-employee still had access to.
The attacker then used these credentials to publish several malicious updates to @ledgerhq/connect-kit, specifically affecting versions 1.1.5 to 1.1.7. These compromised versions used a modified WalletConnect tool for linking decentralized applications to mobile wallets and redirecting funds to a wallet controlled by the attacker.
Ledger, in their official communication, indicated that the rogue packages were active for approximately five hours, with a critical period of under two hours during which funds were actively siphoned off. In collaboration with WalletConnect, Ledger promptly issued a secure version 1.1.8 of the Ledger Connect Kit, addressing the immediate danger posed by the malicious versions. However, they advised users to delay using the Ledger Connect Kit for an additional 24 hours, likely to ensure that any requests to the corrupted CDN expired and/or were removed from the cache. The incident highlights the increasingly complicated attack surface and severe consequences resulting from successful software supply chain attacks.
Conclusion
The last quarter of 2023 was dominated by sophisticated attacks taking advantage of poorly defended software supply chains. Open source software packages serve as the fundamental building blocks for nearly all software in the world. Astoundingly, these building blocks are rarely vetted or analyzed for risk by organizations that critically depend upon them.
As we move into 2024, the software supply chain will remain one of the easier vectors for getting a foothold inside a secure network. As a result of this, we expect a continued rise in sophisticated attacks targeting specific organizations in the financial and cryptocurrency spaces. Additionally, we expect attackers to leverage access to customer data and assets in broad ransomware-style campaigns, releasing pilfered information unless the ransom is paid.
If you aren’t already taking your software supply chain security seriously, now is the time. It represents a clear and present danger to the stability and security of your infrastructure, software developers, and, most importantly, your customers.
Phylum Q4 Research Recap
We routinely publish research on campaigns and targeted software supply chain attacks. While these do not cover all of the campaigns we see, they highlight some of the more interesting attacks and behaviors from this quarter.
- Cloud Provider Credentials Targeted in New PyPI Malware Campaign
- Phylum Discovers SeroXen RAT in Typosquatted NuGet Package
- Obfuscated PyPI Packages Purporting to be i18n Libraries Actually Stealing Telegram Data
- Dozens of npm Packages Caught Attempting to Deploy Reverse Shell
- Crypto-Themed npm Packages Found Delivering Stealthy Malware
- Encrypted npm Packages Found Targeting Major Financial Institution
- Ledger npm Repo Breached in Spear Phishing Attack