Rust Crate Shipping xz Backdoor

By now, news of the malicious backdoor in the XZ Utils compression library has been widely circulated. Though the potential damage appears to have been largely mitigated by the heroic work of a single engineer, aftershocks of this attack remain. Today’s brief offering concerns one such that Phylum found in the Rust ecosystem, the quick action taken by the Rust crate maintainer, and what danger may remain.
--cta--
Background
How did we get here?
The Lempel-Ziv-Markov chain algorithm (LZMA) is a data compression algorithm implemented by liblzma in XZ Utils, a general-purpose data compression library. The Rust crate of the same name provides Rust developers with bindings to the liblzma implementation. This code is available on GitHub under the Portable-Network-Archive/liblzma-rs repository. On Friday, 5 April 2024, the Rust crate maintainer bumped its liblzma-sys version to 0.3.2.
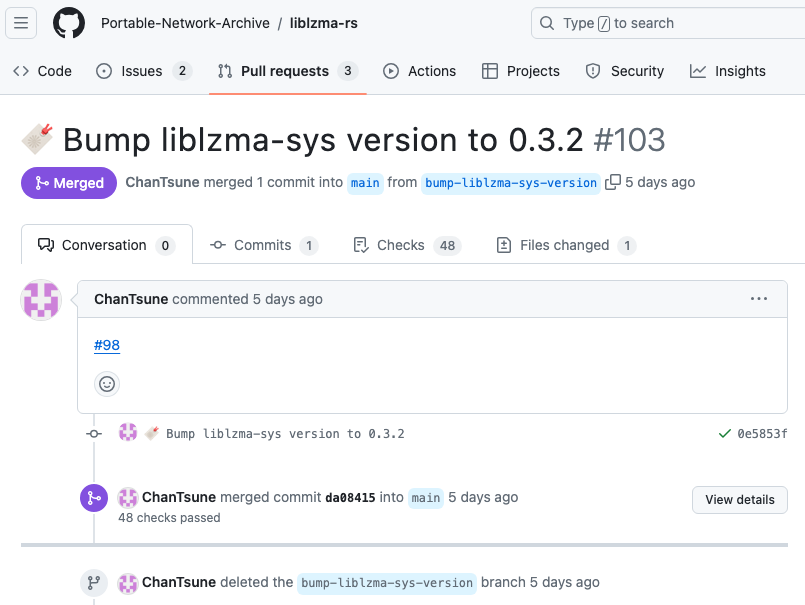
As it turns out, this was precisely the version of liblzma-sys containing the notorious xz backdoor:
- File:
liblzma-sys-0.3.2/xz/tests/files/bad-3-corrupt_lzma2.xz- SHA256 Hash:
ecda10d8877d555dbda4a4eba329e146b2be8ac4b7915fb723eaacc9f89d16bd
- SHA256 Hash:
- File:
liblzma-sys-0.3.2/xz/tests/files/good-large_compressed.lzma- SHA256 Hash:
9aef898229de60f94cdea42f19268e6e3047f7136f2ff97510390a2deeda7032
- SHA256 Hash:
The explicit circumstances under which the xz backdoor would be triggered in these files have been extensively discussed elsewhere, and that is no less of a concern here. However, the presence of these files on any system exposes that system to potential future attacks, such as a “living off the land” attack. These kinds of attacks use what files are available on a given system, rather than shipping malware directly to a victim.
Phylum’s automated platform
Monitoring open source while you sleep
crates.io is one of the seven open source ecosystems that we actively monitor. Within minutes of the publication of the liblzma crate on 5 April 2024, our automated platform raised a critical warning that liblzma had a malicious dependency in liblzma-sys.
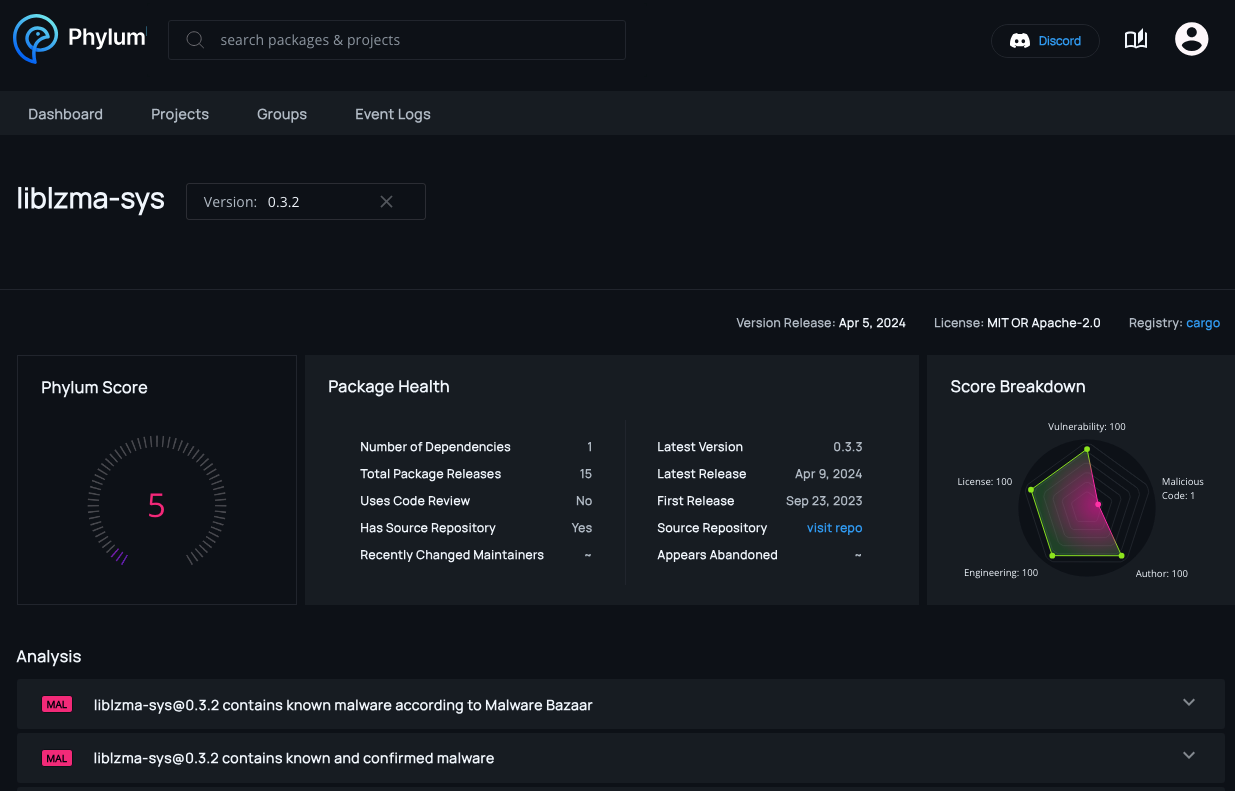
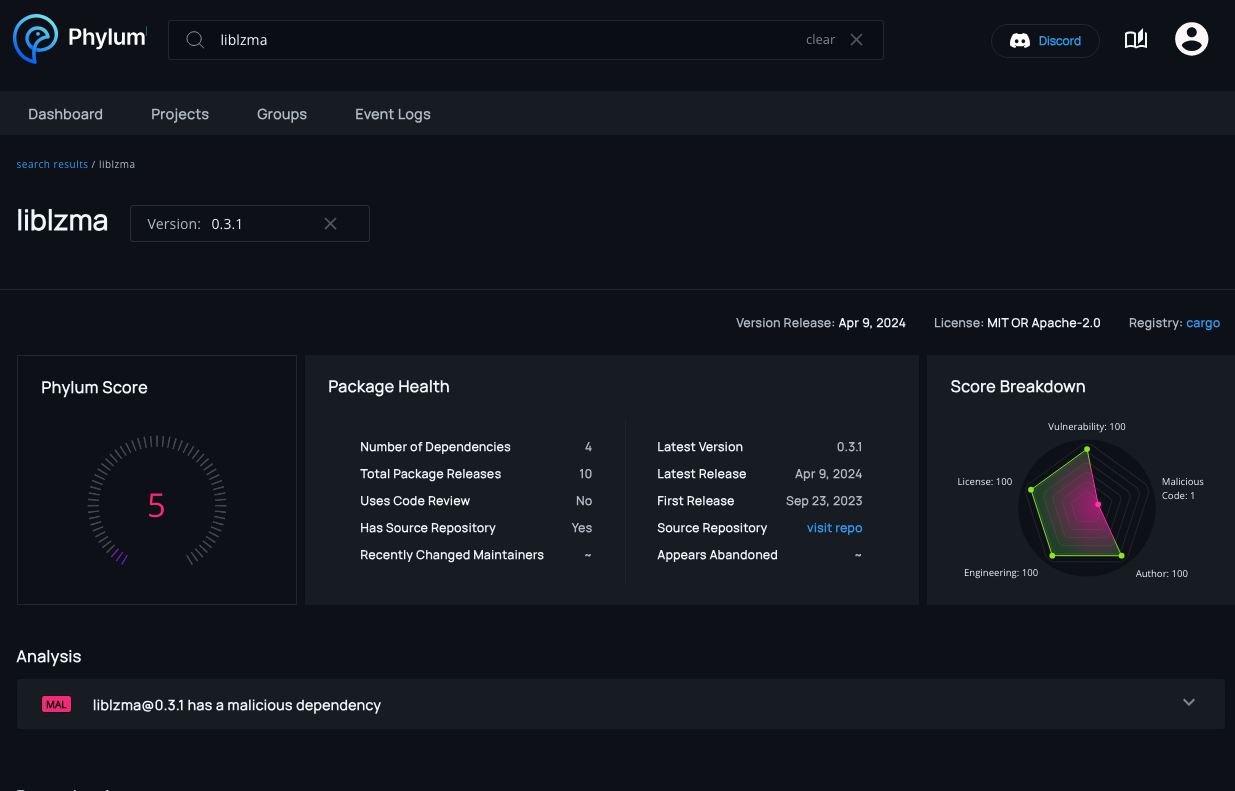
Critical issues break builds, so Phylum users were notified and protected from any immediate malfeasance accompanying this crate.
Reporting and Mitigation
On Tuesday, 9 April 2024, Phylum contacted the Rust security team and raised an issue on GitHub:
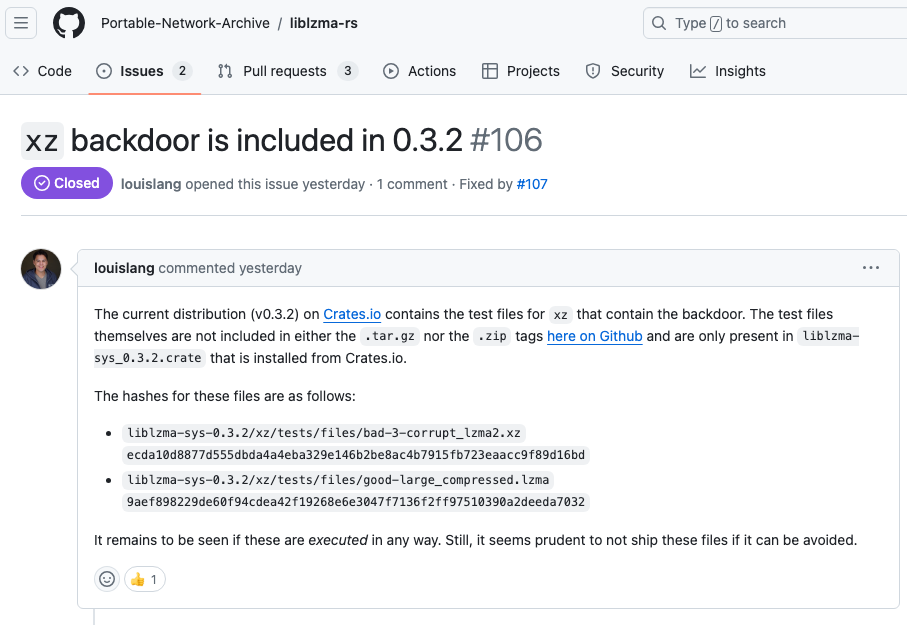
Eight hours later, these files were removed from the repository.
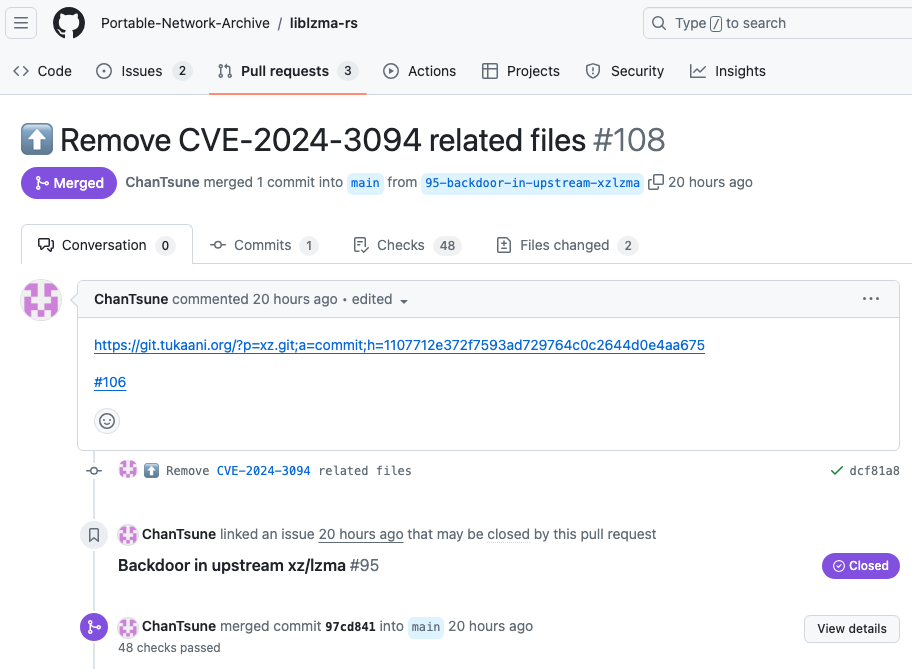
Moreover, affected versions of the liblzma and liblzma-sys crates were yanked from crates.io, but only after numerous downloads of these crates occurred (over 5500 for liblzma and over 1100 for liblzma-sys).
Conclusion
Rust developers should check that their development environment is free from these yanked crates. All the pieces necessary to exploit the malware in these files are well documented by now, and the presence of these files only helps an attacker.




