Securing the Innovation Pipeline – 5 Key Considerations on Software Supply Chain Risk
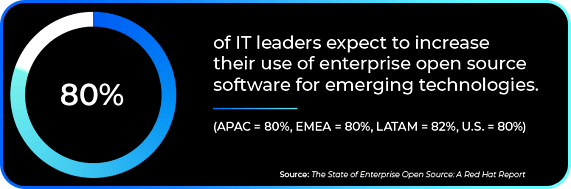
A recent RedHat report stated that open-source software growth will continue to outpace proprietary software and that 80% of IT leaders expect to increase their use of open-source software for emerging technologies and innovation.
If businesses are betting their digital transformation and innovation on open-source software; efforts to achieve a comprehensive understanding of the open-source software supply chains are therefore essential.
Transparency into the provenance of software offers a baseline for building a system-wide view of specific software dependencies and associated risks.
Gaining a solid understanding of the following questions will provide a solid foundation from which to address critical gaps in the security of the overall software supply chain. Providing insight into risks in a way which can operate at the speed of modern development is critical to ensuring that problems are identified before becoming significant issues.
- What is the risk implied by using components in the development of business-critical software, including updates to components that may not yet have had a thorough audit?
- How can I ensure that using security controls won’t slow down the pace of development?
- How can we leverage machine learning to ensure that we stay ahead of threats?
- What can be done to encode business risk into the software development process?
- Can understanding (and mitigation) of risks and existing issues be pushed as far left in the software development process as possible?
Given the rapidly evolving ecosystems needed for innovation, we need modern tools and strategies that can proactively identify risks in your software supply chain, prioritize those risks based upon business context, and provide remediation recommendations to support growth initiatives.
To learn more about Phylum’s automated malware identification capability, how we support secure and efficient use of open-source software and what you can do to encourage your team to take the next steps, contact us for a conversation.




