W4SP Stealer Update—Attacker now Attempting to Masquerade as Popular Orgs

Hello again from the Phylum Research Team! It’s been 2 weeks since we published our deep dive into the on-going W4SP Stealer supply-chain attack targeting Python developers and this is still a very active attack. The attacker has continued releasing package after package at a slow but very steady pace.
The modus operandi appears to be the same, generally speaking. The attacker copies existing repos and injects a malicious __import__ statement into the __init__.py or setup.py. The number of layers and complexity of obfuscation varies slightly from package to package, but they all appear to still have the same common end goal of getting W4SP Stealer deployed on developers’ machines.
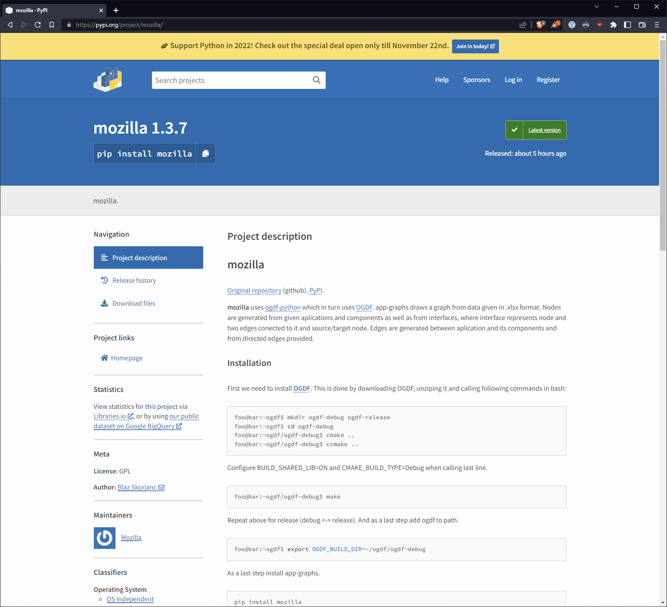
Mozilla on PyPI⁉️
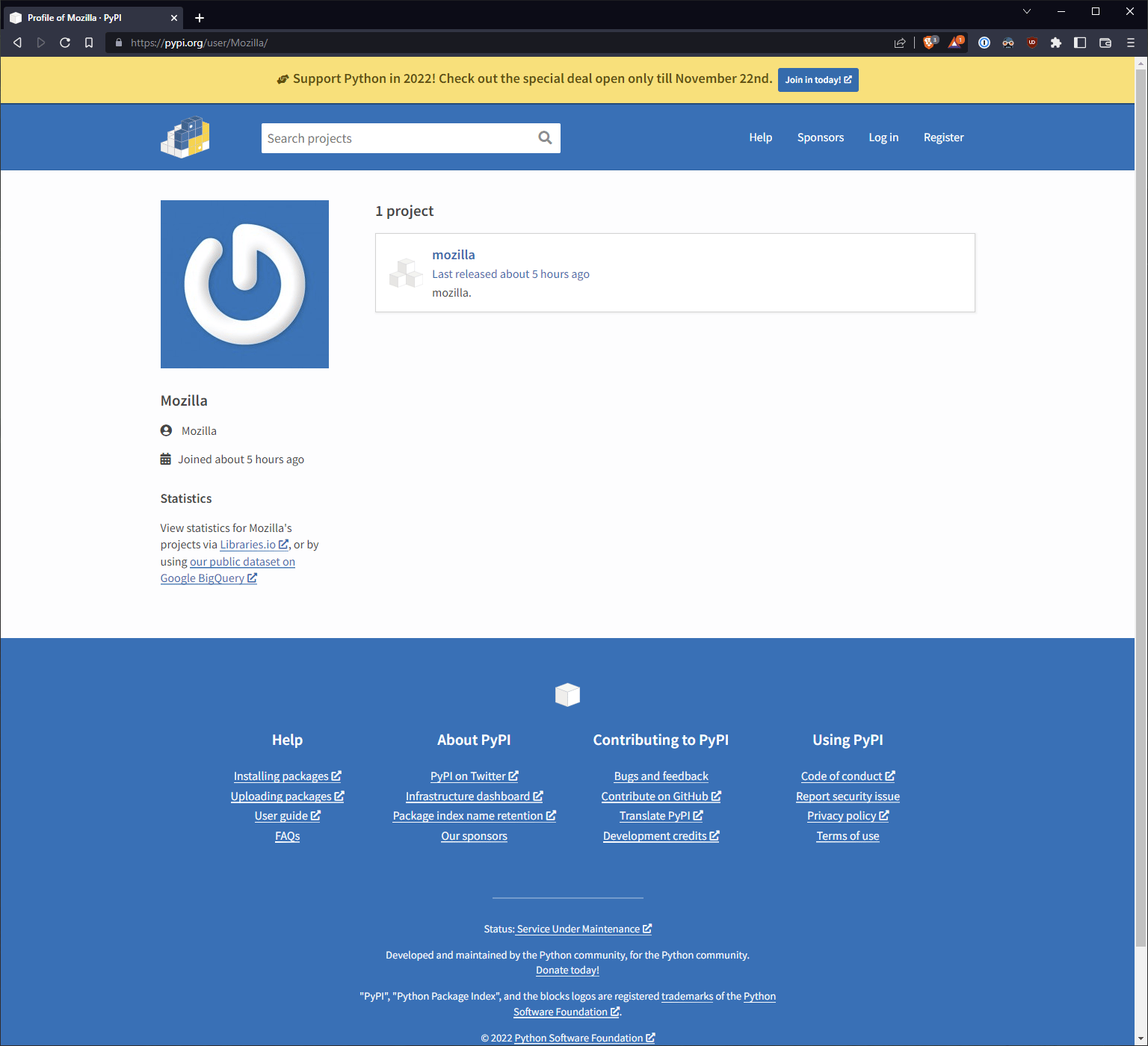
In a brazen albeit strange twist, just this morning, the attacker published a package on PyPI called mozilla under a username also registered as “Mozilla.” We’re not sure what a Python developer might expect to receive by pip installing mozilla onto their machine (perhaps a terminal-based Firefox??) but there you have it—not a typosquat, per se, but a “brandsquat” maybe? The attacker is clearly trying to pose as the organization itself, hoping to rely on brand name recognition to not raise suspicion. Either way, this particular attempt has lifted the legitimate part of the code from a package called app-graphs.
The Full List
You can see from some entries on the list that Mozilla isn’t the only brand name being used. There are a handful of packages released with Discord and TikTok in the names as well.
This attack has proven to be bold, steady and relentless. Here’s a full list of the additional packages we’ve uncovered since our last report:
mozillashortnetshortnetspylo-colorweb5color-randomsimple-colorloyauocolor-utilitytiktok-filter-apiDiscord-Embeddscolor-utility-testpyshftulerblockcypher-libdiscord-api-wrapperascii2artcrypto-paymentsapchcolors-it
We at Phylum are continuing to closely watch this attack and report all these packages as soon as we see them. Be sure to stay tuned for our next update!
Impact
As of publication, the total download count for this new set of packages is about 3000 downloads.




