Enterprise Strategy Group Report: The Growing Complexity of Securing the Software Supply Chain

Tech Target’s Enterprise Strategy Group (ESG) recently published a report called “The Growing Complexity of Securing the Software Supply Chain,” based on survey results from 368 security professionals in North America, specifically in the developer sector.
The survey results validate that open-source software usage is growing, along with a rise in security incidents. It provides organizations with the evidence they need to better understand the risk involved with software supply chain processes and guidance.
Security Perception vs. Attack Reality
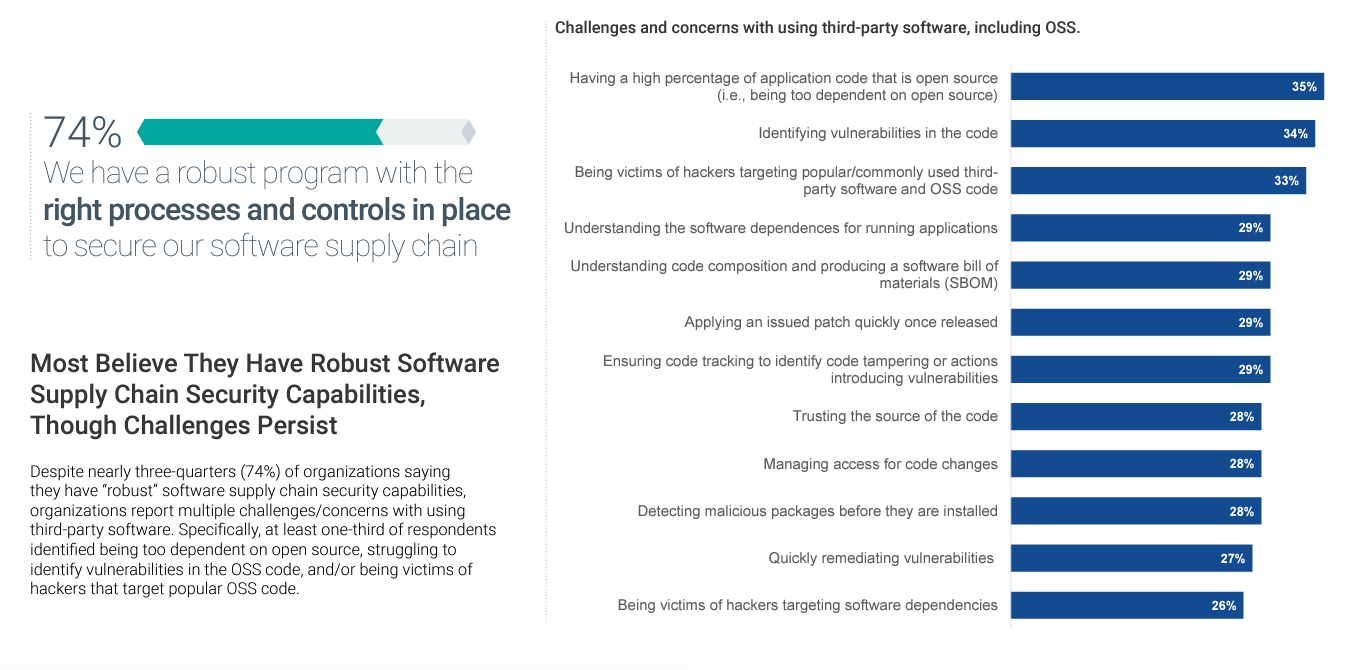
The participants' survey responses reveal a common dichotomy within the world of cybersecurity: perceived security vs. actual. A substantial percentage (74%) of organizations believe their programs are well-appointed to secure their software supply chain. Only 33% are concerned about falling victim to hackers targeting popular third-party software and open-source software (OSS) code.
Coincidentally, a similar proportion responded that they used security tools focused on third-party and open-source software. 34% report using an automated OSS package risk management and contextualization tool and SAST tools, and 32% report using third-party vulnerability scanning. These tools are often used to compare threats against a known vulnerability database, but known software vulnerabilities are not an attackers preferred method of compromise.
This is concerning given, on average, only 18% of the zero-day vulnerabilities and malicious code-based attacks identified by Phylum are ever assigned a common vulnerabilities and exposures identifier (CVE). So, while most organizations think they are protected from software supply chain attacks, it’s highly unlikely unless they have a tool in place to detect malicious code-based attacks or zero-day vulnerabilities.
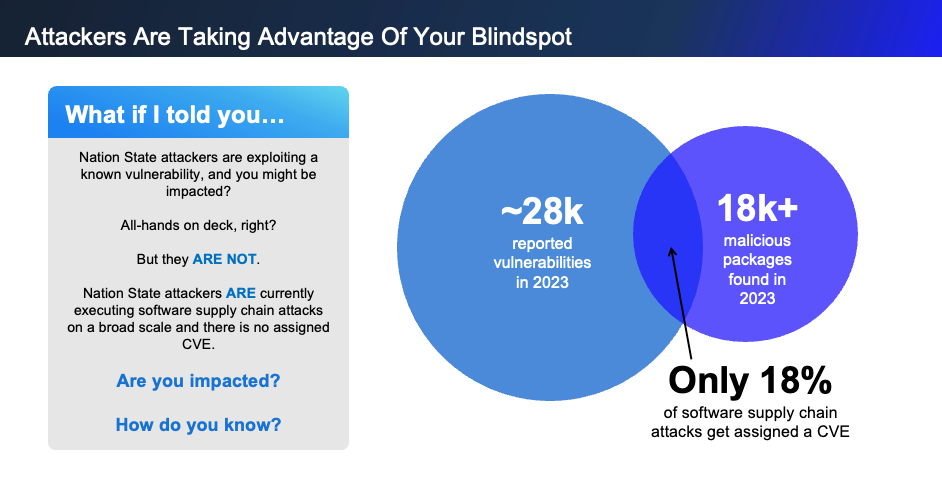
It's then no surprise that most organizations (91%) reported experiencing a software supply chain-related incidents in the last year. Bad actors are counting on this lack of visibility in order to easily compromise organizations and escalate devastating attacks. Our Q4 2023 research report, which showed the number of organizations targeted for attacks had grown significantly (262.63%) from the previous quarter, which had already risen by 47% from the quarter before. Targeted attacks increased again in Q1 2024 by 121% over Q4 2023. This trajectory underscores the general trend of increasing software supply chain attacks overall, but also sounds the alarm on how organizations are blind to how they are being openly targeted.
However, according to the report, when asked the biggest challenges and concerns with using third-party software (including OSS) only 33% of respondents reported being worried about being victims of hackers targeting popular/commonly used third-party software and OSS code, only 26% are worried about being victims of hackers targeting software dependencies and only 28% are concerned about trusting the source of the code.
Maybe if this report was published post-XZ compromise, respondents would prioritize differently. Understanding the risks around the people involved - the project authors and contributors - is critical: the actor who implemented the XZ backdoor also contributed to other prominent projects, in many cases following a similar pattern of behavior (minus the final implementation of a malicious payload), adding small, innocuous changes to multiple forks of a popular library.
After all, how can you properly prioritize threats if you’re not even considering the risks that contribute to the majority of software supply chain attacks?
Policy Governance, OSS Security, and SBOMs
Only 44% of participants were completely confident that their developers were following proper governance policy and only using secure OSS. Although current regulations require the use of software bill of materials (SBOMs) to improve security, only 22% indicated they were using an SBOM generation tool. Of that small percentage, less than half (48%) indicated using such a tool was a mandatory part of their application development process. This is unsurprising considering the complexity and high number of touchpoints typically required to operationalize SBOMs.
Phylum understands this complexity and helps organizations simplify their SBOM creation and ingestion by distilling the process down to these three easy steps.
1) Define Policy: Phylum provides organizations with a flexible policy framework to formulate a simple policy based on their business risks and regulatory requirements.
2) Onboard Stakeholders: Stakeholders can easily be onboarded through invitations or various integration paths. Our comprehensive API and extension framework offers customization and assimilation to existing workflows and business processes.
3) Manage Findings: once stakeholders are on board, the platform manages and automates the SBOM lifecycle, facilitating collaboration, continuous policy compliance, and simplifying the process for improved adoption.
Confused Targets Make an Attackers Job Easy
This report’s responses reveal an interesting contradiction: participants' confidence in their current security processes vs. the significant growth in malicious code-based attacks against software supply chains. While this perception vs. reality is common across cybersecurity, this specific vector is such an easy target that it amplifies the need for clarity.
The study also includes guidance for cross-team collaboration to unify against the complexities associated with software supply chain security. Even though over half of the responses of these cybersecurity and IT teams indicate they are final decision-makers, it is important to include other teams in the evaluation process to avoid development productivity impact and ensure repeatable processes for better governance.
While it is a promising indicator that 44% of the participants plan to prioritize scanning OSS components and third-party libraries for vulnerabilities, known vulnerabilities are only exploited 2%—7% of the time. On the other hand, malicious code-based attacks execute 100% of the time and should take a top spot on the priority list.
The responses in this report clearly show that organizations are still confused as to how they should best protect their software supply chains. However, it is encouraging to see the number of organizations starting to take software supply chain security more seriously. If there’s one message to take away from this report it’s that all organizations need to start going on offense instead of relying on code scanning, patches and uninformed remediation to keep applications safe.
Read the full results in the ESG ebook here.




