Q1 2024 Evolution of Software Supply Chain Security Report

Open source makes up a considerable part of modern-day software projects. CVEs abound for open-source libraries and software packages; however, according to Kenna Security, only 2-5% of these CVEs are ever exploited in the wild. By contrast, 82% of the malicious packages identified by Phylum never receive a CVE or end up in any known vulnerability database. Without a robust solution for monitoring the open source in use, you are flying blind to the dangers and risks posed by software packages authored by individuals you do not know and whose motivations may not align with your own.
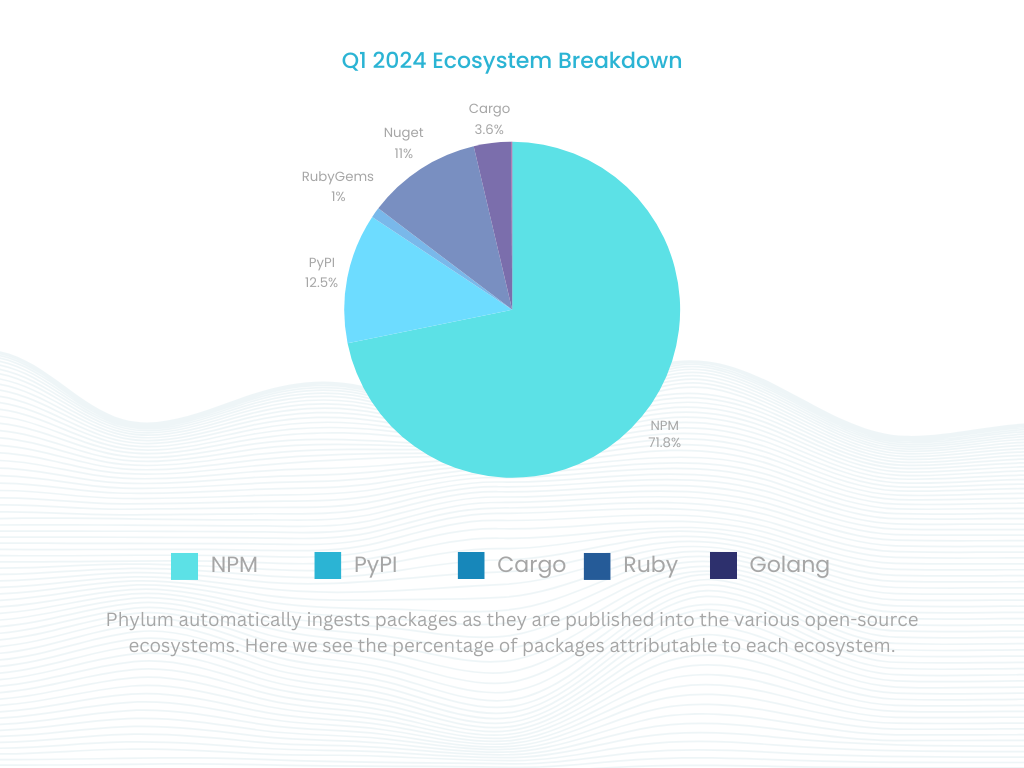
Phylum is the premier platform for identifying and mitigating supply chain attacks targeting software developers and the organizations they work for. Phylum can provide deep insights into the risks associated with open-source libraries and packages by monitoring package publications across seven ecosystems in near real-time (i.e., npm, PyPI, RubyGems, Nuget, Crates.io, Golang, and Maven). More importantly, we can alert you to these threats before they have had an opportunity to impact your software engineering efforts negatively.
The Phylum Research Team diligently reports on novel findings and summarizes quarterly the trends and statistics from open-source package registries. Join us as we delve into some of the more critical attacks and impacts from Q1 of 2024.
Overview
Over the last quarter, our automated analysis platform analyzed 186M files across 2.9M packages. This represents a 1.64% increase in files and a 16% increase in packages analyzed versus the previous quarter.
As has been the case in previous quarters, we saw an uptick in the number of packages targeting specific organizations, with a 121% increase from Q4 2023. In addition to this, we also witnessed several large spam campaigns publishing an enormous amount of packages to npm. These spam campaigns are mostly driven by financial motives tied to relatively new cryptocurrency that promises to pay developers for their open-source contributions.
Across all packages analyzed this quarter, Phylum saw the following behaviors:
- 7,818 packages targeted specific groups or organizations
- 3,668 packages referenced known malicious URLs
- 428,706 packages contained pre-compiled binaries
- 24,129 packages executed suspicious code during installation
- 7,363 packages made requests to servers by IP address
- 9,650 packages attempted to obfuscate underlying code
- 450 packages enumerated system environment variables
- 8,878 packages imported dependencies in a non-standard way
- 1,369 packages surreptitiously downloaded and executed code from a remote source
- 1,846 typosquat packages were identified
- 3,069 packages were registered by authors with throwaway email accounts
- 69,607 spam packages were published across ecosystems
- 291 depends on known malware
- 2,083 packages reviewed and deemed critical malware
Continued Targeting of Developers
We recently uncovered a complex cyberattack targeting developers via the npm ecosystem, involving a malicious npm package disguised as a code profiler. This package was found to install malware capable of stealing cryptocurrency and credentials, ingeniously hidden within a test file— a tactic we believe was chosen under the assumption that such files would escape scrutiny. Our findings reveal this to be part of a broader social engineering campaign aimed at developers, with subsequent discoveries indicating an evolution in the attacker's methodologies, including the self-hosting of malicious npm dependencies and links to activities supported by the North Korean state.
Our investigation began with the detection of a spoofed npm package named execution-time-async, designed to mimic the legitimate execution-time package. The malicious version was embedded with obfuscated code that, upon deobfuscation, was designed to trigger the download of additional malware and to exfiltrate sensitive information, such as browser login credentials. The sophistication of these techniques, including the employment of combosquatting and obfuscation, highlights the advanced methods employed by attackers to conceal and execute their malicious operations. Furthermore, the malware was programmed to execute Python scripts that further compromised victims' systems, enabling attackers to gain remote control and steal data additional data.
Our deeper analysis linked the malicious activities to specific GitHub repositories and user accounts, suggesting a potential connection to North Korean state-sponsored efforts targeting developers seeking employment. The attackers cunningly used fake job postings to distribute their malware, presenting themselves through what appeared to be legitimate coding challenges or job interview processes. This ongoing research underscores the critical need for vigilance within the open-source community and among developers to guard against such sophisticated cyber threats. It showcases the importance of meticulously examining code from untrusted sources and the need for heightened cybersecurity awareness to combat cyber attackers' increasingly sophisticated and deceptive strategies.
Large Typosquat Campaigns
On March 26, 2024, our risk detection platform at Phylum identified an expansive typosquatting campaign within the Python Package Index (PyPI), targeting various widely used Python libraries. This campaign, executed in several waves, led to the creation of over 500 typosquat variations of well-known packages such as requests, py-cord, colorama, among others. This operation aimed to deceive developers into downloading these malicious packages by mistake and underscored the sophisticated methodologies employed by attackers to exploit open-source software ecosystems. Initial experiments by the attackers with packages like schubismomv3 showed trial runs of various malware deployment techniques, signaling the preparation phase of this campaign.
The attack mechanism was primarily initiated upon installing these typosquatted packages, triggering the embedded malicious code within the setup files. A closer examination of this code revealed the attackers' attempts to execute a series of operations designed to exfiltrate sensitive information such as passwords, cookies, and wallet data from the victim's system. Subsequent payloads aimed to further compromise the system, with one such payload attempting to fetch and execute additional malicious scripts hosted on external servers. This broad campaign highlighted the attackers' intent to cast a wide net, targeting individual and organizational assets within the Python developer community.
This incident underscores the persistent threat landscape within software supply chains, particularly in open-source repositories where rapid proliferation can lead to significant impacts before detection and remediation. Our analysis and swift action by PyPI administrators were crucial in mitigating the immediate threats posed by this campaign. However, the sophistication and breadth of this attack serve as a stark reminder of the ongoing challenges faced in securing software ecosystems. As attackers continue to evolve their strategies, it remains imperative for both developers and platform administrators to maintain vigilance and implement robust security measures to protect against such malicious activities.
United Nations Outreach
In January 2024, we revisited our November findings related to a series of npm packages embroiled in a sophisticated attack chain targeting cryptocurrency assets. Initially, uncovered packages, once installed, engaged in a complex procedure of downloading, decrypting, and executing a remote file, thereafter erasing any digital footprints by manipulating files to restore the package directory to a seemingly harmless state. Following our continued investigation, nearly two dozen additional packages linked to this ongoing campaign were identified, with the QiAnXin Threat Intelligence Center attributing the operation to a North Korean Advanced Persistent Threat (APT). This revelation aligns with the crypto-themed nature of the package names and the historical context of North Korean cyber operations aimed at circumventing international sanctions through cryptocurrency theft.
Our insights into the campaign expanded as we compiled an updated list of packages related to this malicious activity, which were meticulously designed to execute a binary from various URLs upon installation. This tactic indicated a persistent and evolving threat with a clear intention to evade detection while establishing a foothold within the systems of unsuspecting developers. The endgame was not only to gain persistent access to individual systems but also to infiltrate the organizations these developers were part of, specifically targeting the cryptocurrency sector. Our role in this extended beyond analysis as we were approached by a United Nations panel for expert guidance on countering North Korea's evasion of sanctions through such cyber operations. Our unique position, supported by a vast repository of data and analytical tools, enabled us to contribute valuable insights and recommendations towards understanding and mitigating the threats posed by these state-sponsored activities, further emphasizing the critical vulnerabilities within the open-source ecosystem exploited by such actors.
Conclusion
The first quarter of 2024 witnessed sustained attacks by sophisticated and unsophisticated actors in the software supply chain. These attacks continue to be successful because the open source packages that serve as the building blocks of our software platforms are rarely vetted for the risks that they pose to the organizations that critically depend upon them.
Phylum expects these malicious attacks to continue. Attackers are proving adept at thwarting automation defenses put up by package repository maintainers. For this reason, we expect attackers will flood these repositories with more spam with increasing sophistication. Once these packages are staged, it will take very little effort for the attackers to introduce malware that will be difficult to find in the morass of spam dependencies.
Now is the time to take action and defend your developers from software supply chain attacks. Most malicious attackers are not exploiting some obscure code vulnerability; they are attacking software developers directly with surreptitious malware designed to steal everything and gain control of a developer’s system.
Phylum Q1 Research Recap
We routinely publish research on campaigns and targeted software supply chain attacks. While these do not cover all the campaigns we see, they highlight some of this quarter's more interesting attacks and behaviors.
- Update to November’s Crypto-Themed npm Attack
- npm Package Found Delivering Sophisticated RAT
- Fake Developer Jobs Laced With Malware
- Dormant PyPI Package Updated to Deploy NovaSentinel Stealer
- Typosquatting Campaign Targets Python Developers
- An Introduction to Open-Source Software Supply Chain Risk
- Malicious npm Package Caught Hijacking ERC20 Contracts to Drain USDT
About Phylum
Phylum defends applications at the perimeter of the open-source ecosystem and the tools used to build software. Its automated analysis engine scans third-party code as soon as it’s published into the open-source ecosystem to vet software packages, identify risks, inform users, and block attacks. Phylum’s open-source software supply chain risk database is the most comprehensive and scalable offering available. Depending on an organization’s infrastructure and appsec program maturity, Phylum can be deployed throughout the development lifecycle, including in front of artifact repositories, in CI/CD pipelines, or integrated directly with package managers. Phylum also offers a threat feed of real-time software supply chain attacks. The company is built by a team of career security researchers and developers with decades of experience in the U.S. Intelligence Community and commercial sectors. Phylum won the Black Hat 2022 Innovation Spotlight Competition, was named to Inc. Magazine’s 2023 Best Workplaces, and became a Top Infosec Innovator by Cyber Defense Magazine. Learn more at https://phylum.io, subscribe to the Phylum Research Blog, and follow us on LinkedIn, X and YouTube.




