Q2 2024 Evolution of Software Supply Chain Security Report


Software supply chains are complicated. In this complicated web of globally distributed software, attackers can lie in wait, releasing malicious software libraries to unsuspecting developers and organizations. It is prohibitively difficult to manually scan and analyze every package a given organization consumes. Thousands of open-source packages are often pulled together for a single project, where each package consists of hundreds of files made up of thousands of lines of code. How can one reasonably be expected to identify subtle malicious modifications and general subterfuge amongst the chaos that is daily software engineering?
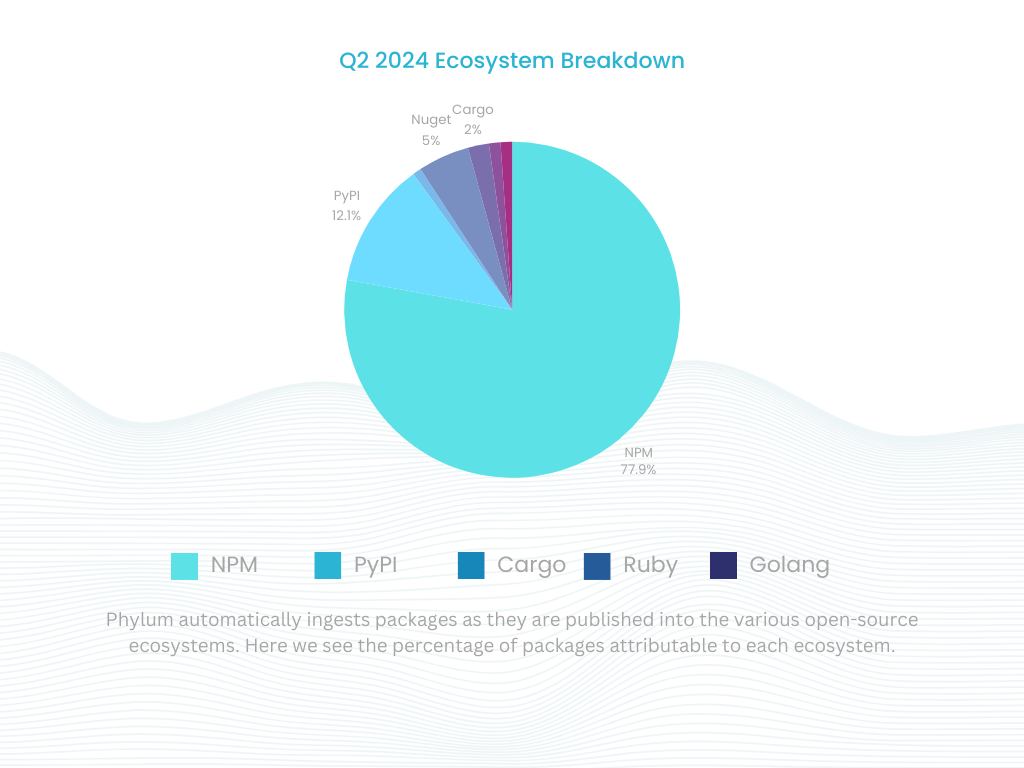
Phylum is the premier platform for identifying and mitigating supply chain attacks targeting software developers and the organizations they work for. Phylum can provide deep insights into the risks associated with open-source libraries and packages by monitoring package publications across seven ecosystems in near real-time (i.e., npm, PyPI, RubyGems, Nuget, Crates.io, Golang, and Maven). More importantly, we can alert you to these threats before they have had an opportunity to negatively impact your software engineering efforts.
The Phylum Research Team diligently reports on novel findings and summarizes the quarterly trends and statistics from open-source package registries. Join us as we delve into some of the more critical attacks and impacts from Q2 of 2024.
Overview
Over the last quarter, our automated analysis platform analyzed 190M files across 2.9M packages. The number of files and packages analyzed remained consistent between Q1 2024 and Q2 2024.
During Q2 2024, we noted that overall dependency confusion packages were down slightly (note Q1 2024 had a 121% increase over Q4 2023), with 5,229 packages targeting specific organizations. Interestingly, the overall verified malicious package publications were up 6.98%, with a 22.15% increase in obfuscation. This indicates that attacks on specific organizations have remained at high levels relative to 2023, and attack sophistication has continued to evolve.
Across all packages analyzed this quarter, Phylum saw the following behaviors:
- 5,229 packages targeted specific groups or organizations
- 9,896 packages referenced known malicious URLs
- 214,402 packages contained pre-compiled binaries
- 24,980 packages executed suspicious code during the installation
- 7,682 packages made requests to servers by IP address
- 11,787 packages attempted to obfuscate underlying code
- 410 packages enumerated system environment variables
- 2,759 packages imported dependencies in a non-standard way
- 1,436 packages surreptitiously downloaded and executed code from a remote source
- 1,042 typosquat packages were identified
- 8,504 packages were registered by authors with throwaway email accounts
- 239,171 spam packages were published across ecosystems
- 299 depends on known malware
- 2,228 packages reviewed and deemed critical malware
The Polyfill Debacle
In June 2024, a significant supply-chain security incident emerged when the CDN of the polyfill[.]io domain began serving malware to hundreds of thousands of websites. The domain and its associated GitHub account, acquired by a Chinese company in February 2024, were used to inject malware into websites embedding cdn[.]polyfill[.]io. This JavaScript library, meant to enable modern functionalities on older browsers, became a vector for malicious activities.
Our research team identified numerous packages directly referencing the polyfill.io domain. Although not all were compromised, several posed a real danger to end users under the right circumstances. As a result, developers using these packages should scrutinize the references to better understand their potential risks. This incident underscores the importance of secure practices, such as implementing Subresource Integrity (SRI) checks, when dynamically loading external resources.
This episode highlights the delicate nature of open source. By compromising a single source, in this case, polyfill.io, the attackers were able to make broad impacts across the software development landscape. The interconnected nature of many of these packages and resources means the weakest link in your organization's security may very well exist outside of your organization, where you have little control or oversight.
Staying ahead of these attacks means implementing appropriate safeguards around the consumption of open source in your organization, ensuring that software is never dynamically loaded from external third-party resources at runtime.
Nation-State Actors
For North Korea, supply chain attacks originating from open source are particularly effective at meeting their goals of bypassing sanctions. By some estimates, North Korean actors have stolen an estimated $4 billion from financial and cryptocurrency groups.
We have a long history of tracking state-backed actors active in the open source ecosystems (see 1, 2, 3, 4, 5). Our detections of DPRK campaigns have been wildly effective, forcing the threat actors to repeatedly change tactics in a futile attempt to avoid detection. However, the lucrative - and disproportionate risk-to-reward ratio - means that it's in the best interest of the attacker to persevere. Shockingly, we’ve seen numerous software packages published and nearly immediately removed from the ecosystem. This can only suggest that the attackers are now selectively targeting organizations and only publishing packages at the exact moment of attack. In at least one case, the packages existed for only 90 seconds on npm before being pulled down by the threat actor.
In April 2024, Phylum's automated risk detection platform identified new malicious npm packages linked to North Korean state actors. The threat actor, using the username nebourhood, published react-dom-production-script and hardhat-daemon, which included a preinstall hook to execute the obfuscated deference.js script, delivering malware. This campaign signifies an evolution in their tactics, with a notable shift from targeting primarily Windows systems to now also including macOS.
The sophistication of these attacks highlights the continuous threat posed by nation-state actors to open-source ecosystems. The malware's silent execution capabilities aim to infiltrate systems without detection, leveraging commonly used open-source packages to reach a wide audience. This incident underscores the critical need for developers to maintain rigorous security practices and closely monitor their dependencies.
Phylum's detection of these malicious packages emphasizes the importance of automated security tools in identifying and mitigating risks within software supply chains. Developers are urged to adopt stringent security measures, such as regular audits and the use of security-focused tools, to protect against such advanced threats. The ongoing vigilance in managing dependencies and understanding potential vulnerabilities is crucial in safeguarding software projects from sophisticated attacks orchestrated by state-sponsored actors.
npm Plagued by Large Spam Campaigns
The increasing reliance on open-source sustainability platforms has led to unintended consequences, with opportunistic actors flooding repositories like npm with spam packages. These platforms aim to compensate developers using systems such as the Tea protocol, which rewards contributions with cryptocurrency tokens. However, introducing financial incentives has sparked a surge in automated spam campaigns, severely impacting the ecosystem's integrity. Phylum estimates that about 1 out of every 4 packages published to npm in Q2 2024 are spam.
Despite its noble intentions, the Tea Protocol has inadvertently incentivized the mass publication of non-functional or cloned packages, exploiting its reward system. This activity not only strains resources but also poses significant security risks. The creation of thousands of interconnected packages could lead to a malware outbreak if a single malicious dependency infiltrates the network.
Phylum's investigation into the Tea protocol reveals critical vulnerabilities in the current model, highlighting the need for improved anti-abuse mechanisms. Effective countermeasures and re-evaluating incentive structures are crucial to ensure that these platforms genuinely support and sustain the open-source community without being compromised by malicious actors. The incident underscores the complexity of balancing developer compensation with maintaining ecosystem security and integrity.
Continued Increase in Actor Sophistication
In June 2024, Phylum discovered an npm package exfiltrating crypto extension data, marking an alarming escalation in the sophistication of software supply chain attacks. The node-ipc package, ostensibly designed for inter-process communication, contained a malicious update targeting crypto wallets and browser extensions. This attack exemplified how dependency manipulation can be exploited to infiltrate developer environments and exfiltrate sensitive data, underscoring the critical need for rigorous package vetting processes in maintaining secure development practices.
Simultaneously, Phylum detected a sophisticated Remote Access Trojan (RAT) shell targeting Gulp projects on npm. The glup-debugger-log package deployed an intricate multi-stage malware campaign, leveraging obfuscated JavaScript to install a dropper, establishing persistent remote access on compromised machines. This attack highlighted the increasing complexity of threat actor tactics, combining advanced obfuscation techniques with conditional environment checks to evade detection and maximize the malware’s impact. The persistent nature of this attack underscores the evolving threat landscape in open-source ecosystems.
Adding to these concerns, Phylum identified a malicious Go binary delivered via steganography in a PyPI package. The msdat package concealed a binary within an image file, which was extracted and executed during installation. This innovative approach demonstrated the lengths attackers will go to bypass traditional security measures. By embedding malicious code within seemingly benign files, threat actors are able to exploit the inherent trust within open-source repositories, making it imperative for developers to adopt comprehensive security strategies.
The increased sophistication of these attacks signals a troubling trend in the software supply chain security landscape. Malicious actors continually refine their methods, employing advanced techniques such as obfuscation, multi-stage payloads, and steganography to infiltrate and compromise development environments. These incidents are a stark reminder of the vulnerabilities inherent in open-source ecosystems and the need for robust, multi-layered security measures to protect against these evolving threats.
Conclusion
Malicious threat actors increasingly see the supply chain as a viable attack vector. We see evidence of this in the increasing sophistication of malware packages they distribute and the increased overall volume of packages released.
We are all consumers of open source, deriving value from the same software supply chains. Poisoning just one point in this complicated web of distributed software compromises large swaths of small and large organizations alike.
Without a vigilant eye - or automated monitoring of the entire software supply chain - it is far too easy to fall victim to an attack originating from open source package consumption. As we have said in previous quarters, attacks are up, sophistication has increased, and you are a target whether or not you realize it.
Phylum Q2 Research Recap
We routinely publish research on campaigns and targeted software supply chain attacks. While these do not cover all the campaigns we see, they highlight some of this quarter's more interesting attacks and behaviors.
- A Note About Polyfill
- npm Package Caught Exfiltrating Crypto
- Sophisticated RAT Shell Targeting Gulp Projects on npm
- Malicious Go Binary Delivered Via Steganography in PyPI
- Nation-State Threat Actors Renew Publications to npm
- Rust crate shipping xz backdoor
- Digital Detritus: Unintended Consequences of Open Source Sustainability Platforms
About Phylum
Phylum defends applications at the perimeter of the open-source ecosystem and the tools used to build software. Its automated analysis engine scans third-party code as soon as it’s published into the open-source ecosystem to vet software packages, identify risks, inform users, and block attacks. Phylum’s open-source software supply chain risk database is the most comprehensive and scalable offering available. Depending on an organization’s infrastructure and appsec program maturity, Phylum can be deployed throughout the development lifecycle, including in front of artifact repositories, in CI/CD pipelines, or integrated directly with package managers. Phylum also offers a threat feed of real-time software supply chain attacks. The company is built by a team of career security researchers and developers with decades of experience in the U.S. Intelligence Community and commercial sectors. Phylum won the Black Hat 2022 Innovation Spotlight Competition, was named to Inc. Magazine’s 2023 Best Workplaces, and became a Top Infosec Innovator by Cyber Defense Magazine. Learn more at https://phylum.io, subscribe to the Phylum Research Blog, and follow us on LinkedIn, X and YouTube.




